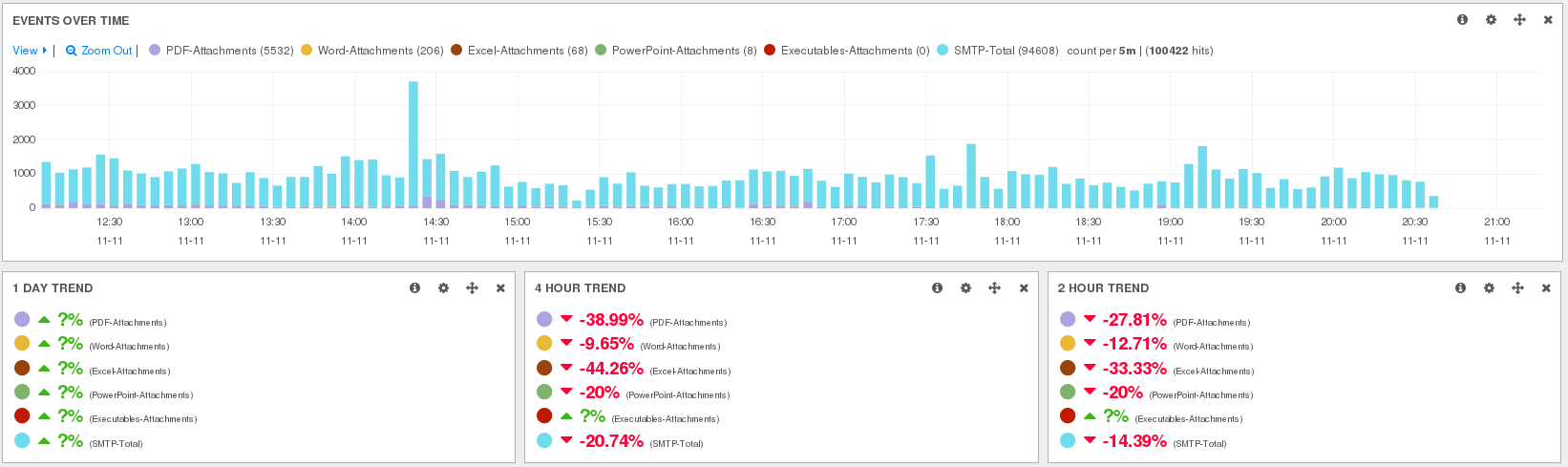
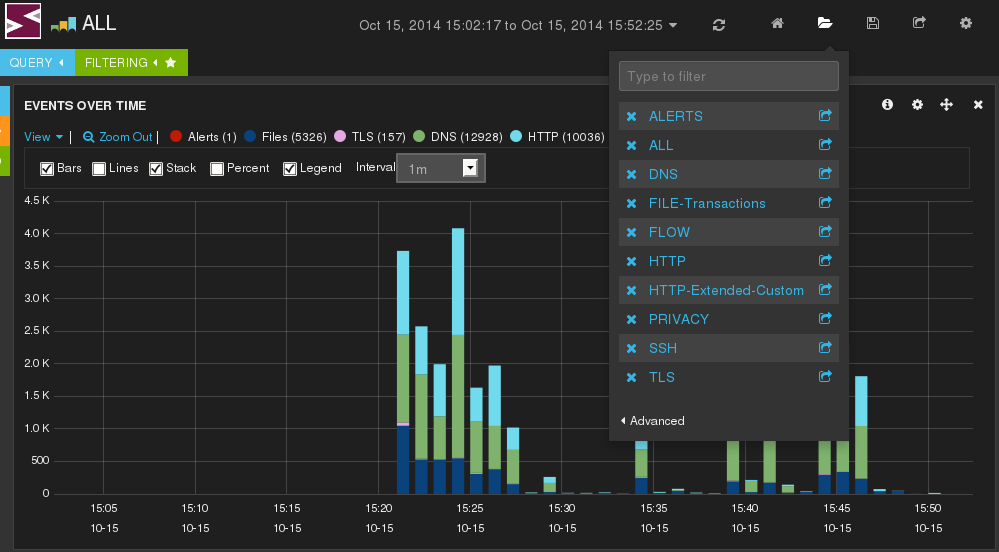
An analysis by political analyst Tarık Özcan published this week in Meer captures something those...
Peter Manev

Recent Posts
Modern IT infrastructure, whether traditional or hybrid, faces persistent challenges: staff...
One of the significant advantages of Clear NDR’s multi-layered detection is its ability to identify...
The example outlined in this blog article demonstrates Clear NDR’s value in delivering visibility...
The following example is of an unstructured hunt technique—an investigation based on an idea or...
One of the key strengths of Clear NDRTM is its AI-based TLS beacon detection, which, when combined...
For many organizations considering Network Detection and Response (NDR), one of the most valuable...
This blog post details how Clear NDR drastically reduces Mean Time to Detect (MTTD) and Mean Time...
For many organizations considering Network Detection and Response (NDR), one of the most valuable...
NOTE: The following article was originally published 02 December 2024 on Help Net Security
In this series of articles, we explore a set of use cases that we have encountered in real-world...
In this series of articles, we explore a set of use cases that we have encountered in real-world...
In this series of articles, we explore a set of use cases that we have encountered in real-world...
In November of 2022 we announced a Suricata ruleset specifically focused on detecting lateral...
Stamus Networks is pleased to announce the release and availability of SELKS 10 (now Clear NDR -...
This month, we celebrate the 10th anniversary of SELKS (now Clear NDR - Community), Stamus...
Before beginning any sort of threat hunt, it is important to consider the tools you are using. This...
This is a follow-up to our third blog on hunting using the publicly available Newly Registered...
This is a follow-up to our second blog on hunting using the publicly available Newly Registered...
This is a follow-up to our first blog on hunting using the publicly available Newly Registered...
In aprevious blog post, we announced the release of Open NRD from Stamus Networks - a set of threat...
This article describes the details of the new Open NRD threat intelligence feeds provided by Stamus...
In aprevious blog post, we compiled a number of useful JQ command routines for fast malware PCAP...
Previously, we compiled a number of useful JQ command routines for fast malware PCAP network...
In aprevious blog post, we compiled a number of useful JQ command routines for fast malware PCAP...
When a threat researcher is investigating malware behavior and traces on the network, they need a...
This week’s guided threat hunting blog focuses on hunting for high-entropy NRD (newly registered...
Every day, new Internet domains are registered through the Domain Name System (DNS) as a natural...
In a recent conversation, one of our customers shared their concerns about the use of ChatGPT in...
This week’s guided threat hunting blog focuses on verifying a policy enforcement of domain...
It is not uncommon to see executable file transfers within an organization. However, it is...
Punycode domains have traditionally been used by malware actors in phishing campaigns. These...
When you see a domain request from a user/client to a non-local or otherwise unfamiliar or...
Non-local domain requests from the user/client network could signal trouble for an organization....
DNS over HTTPS (DoH) is a network protocol designed to enhance user privacy by encrypting DNS...
Plain text executables (such as those downloaded from a PowerShell user agent) are often seen on...
This week in our series on guided threat hunting, we are focusing on locating internal use of...
This week’s guided threat hunting blog focuses on hunting for foreign domain infrastructure usage...
This week’s guided threat hunting blog focuses on hunting for Let’s encrypt certificates that were...
In this week’s guided threat hunting blog, we will focus on hunting for Let’s Encrypt certificates...
In this week’s guided threat hunting blog, we focus on using Clear NDR to identify rogue proxy...
In this week’s guided threat hunting blog, we focus on using Clear NDR to uncover phishing...
This week’s guided threat hunting blog focuses on a specific policy violation - the use of...
This week’s guided threat hunting blog focuses on policy violations; specifically, violations...
For week 2 of our series on guided threat hunting, we will be reviewing a hunting technique to...
So, what’s next? You’ve had a successful hunt, uncovered some type of threat or anomalous behavior...
In addition to deploying advanced detection technologies, many security teams make threat hunting...
Stamus Security Platform is loaded with features that help security teams leverage network traffic...
In this series of articles we share hands-on experience from active hunts in the real world. We...
RSA Conference San Francisco is back in June 2022 and we are excited to once again be a part of one...
In this series of articles, we explore a set of use cases that we have encountered in real-world...
The importance of having a strong security team has been growing in recent years, and many...
As I mentioned in the introductory article in this series (see here >>), Suricata produces not only...
When the blue team needs to mount a network defense, they must answer some very common questions:
- ...
Clear NDRTM helps bank identify threat to its accounting network
With the help of the Clear NDR, ...
In this series of articles, we explore a set of use cases that we have encountered in real-world...
Background
As we have previously written, for all Suricata’s capabilities, building out an...
Background
As we have previously written, for all Suricata’s capabilities, building out an...
Background
As we have previously written, for all Suricata’s capabilities, building out an...
For all Suricata’s capabilities, building out an enterprise-scale deployment of Suricata with...
Exciting news - the OISF just announced that Suricata 6 is now available. This is the culmination...
In this series of articles, we will explore a set of use cases that we have encountered in...
SELKS 6 is out!
If you are still teleworking, you may wish to test and deploy this new edition to...
SELKS 5 is out! Thank you to the whole community for your help and feedback! Thank you to all the...
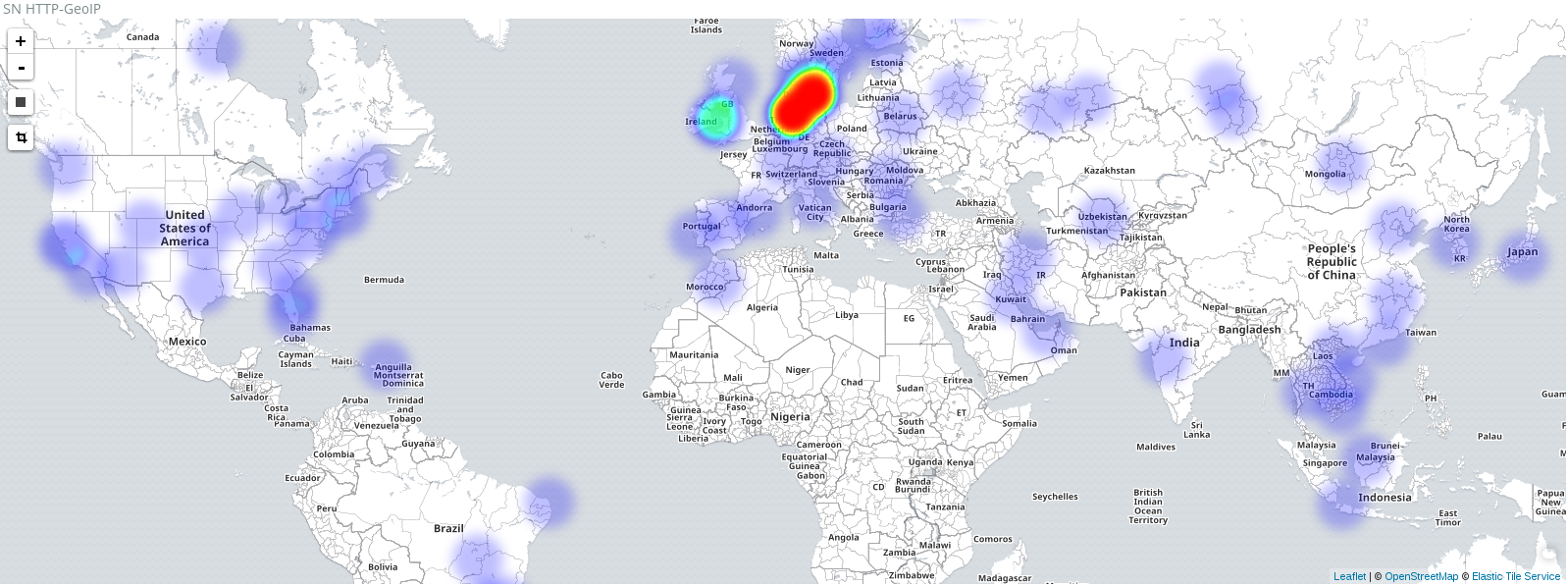
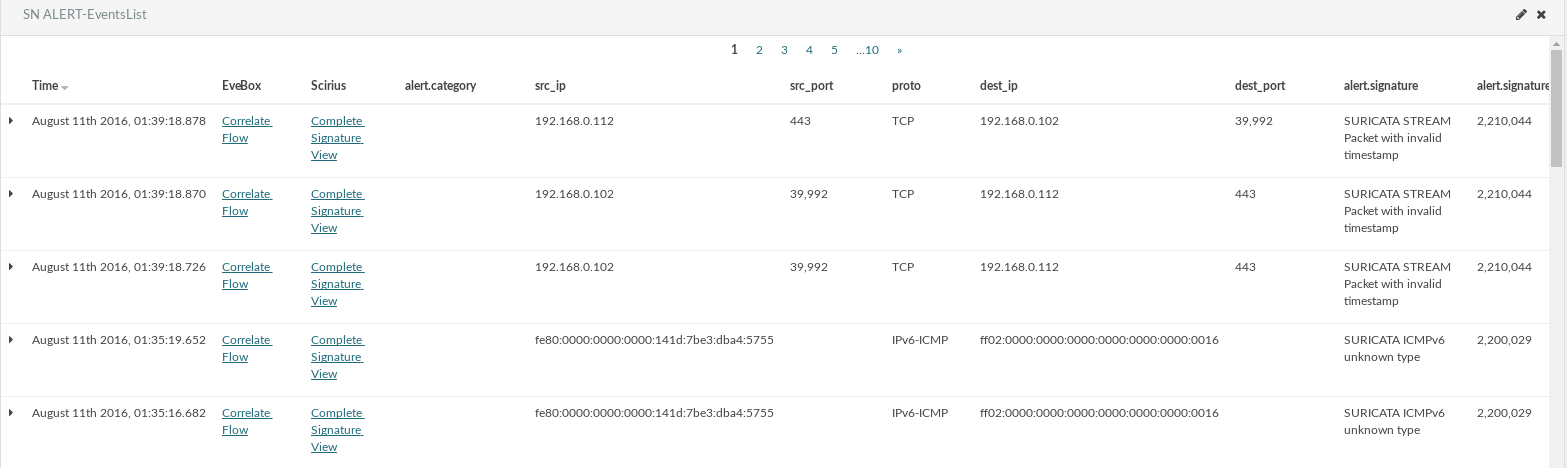
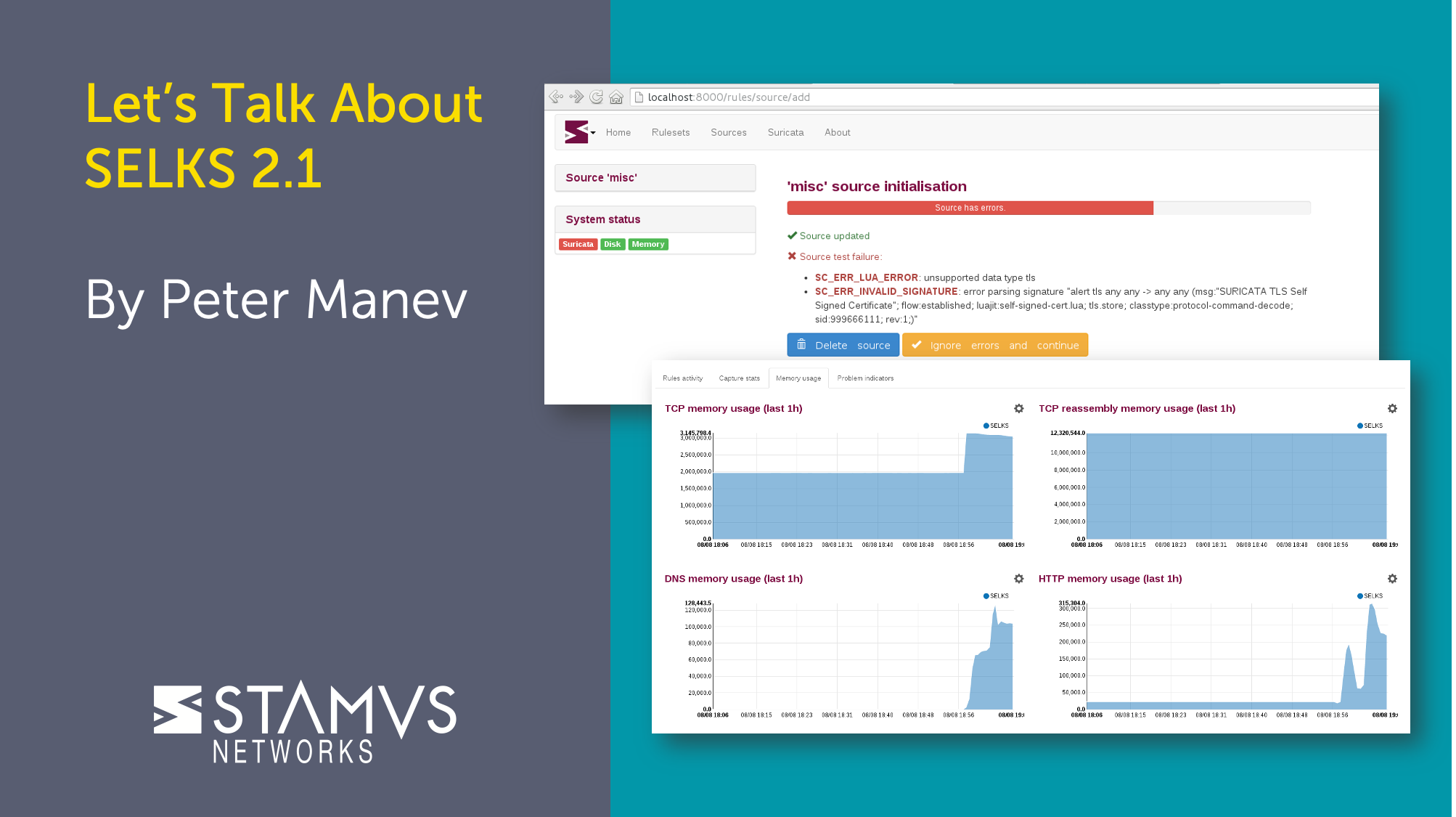
Hi!Yet another upgrade of our SELKS. We are very thankful to all the great Open Source projects and...
Hey! Our new and upgraded showcase for Suricata has just been released - SELKS5 Beta. Thanks to...
This first edition of SELKS 4 is available from Stamus Networks thanks to a great and helpful...
After a very valuable round of testing and feedback from the community we are pleased to announce...
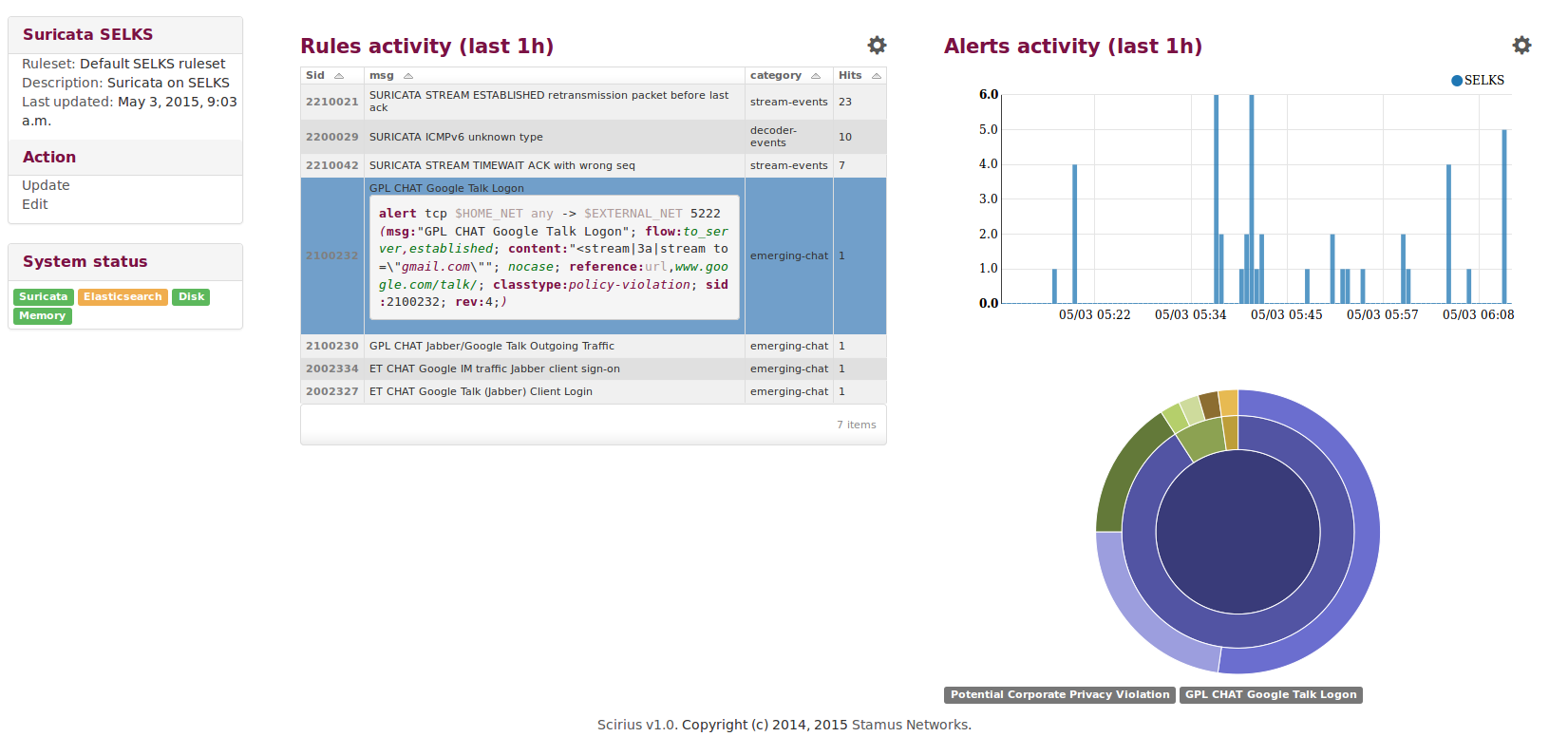
Yes, we did it: the most awaited SELKS 3.0 is out. This is the first stable release of this new...
After some hard team work, Stamus Networks is proud to announce the availability of SELKS 3.0RC1.
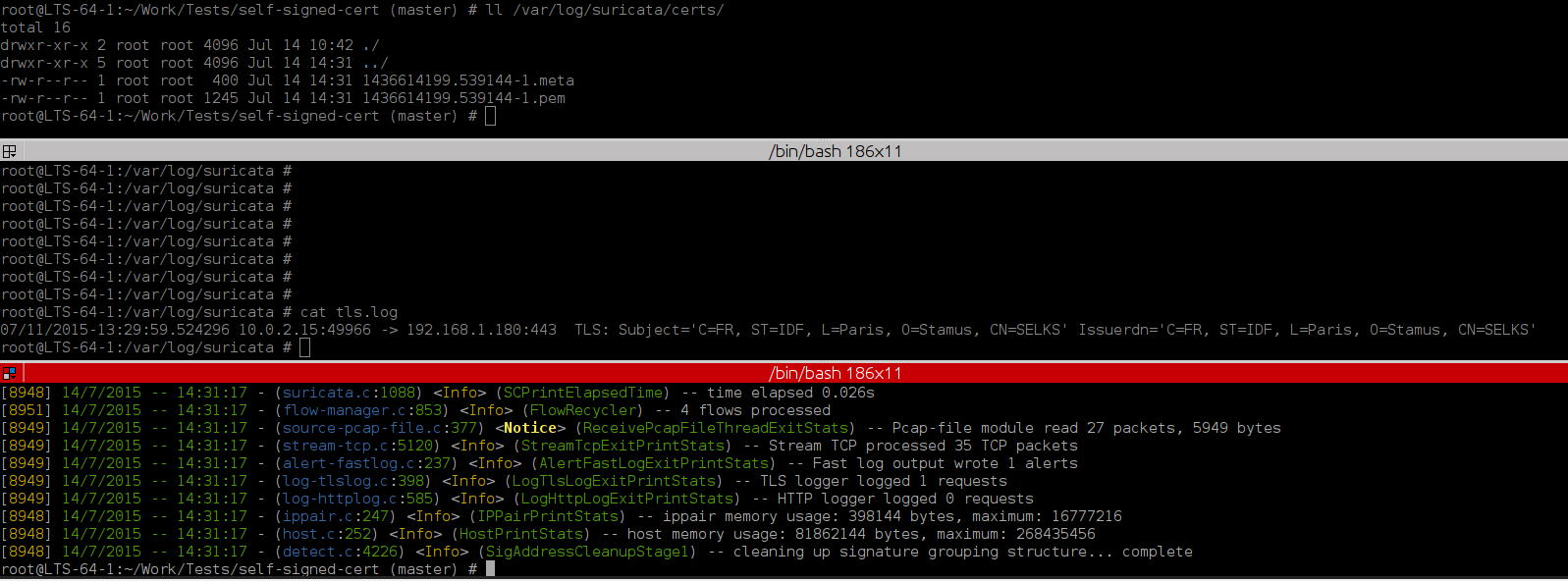
Introduction
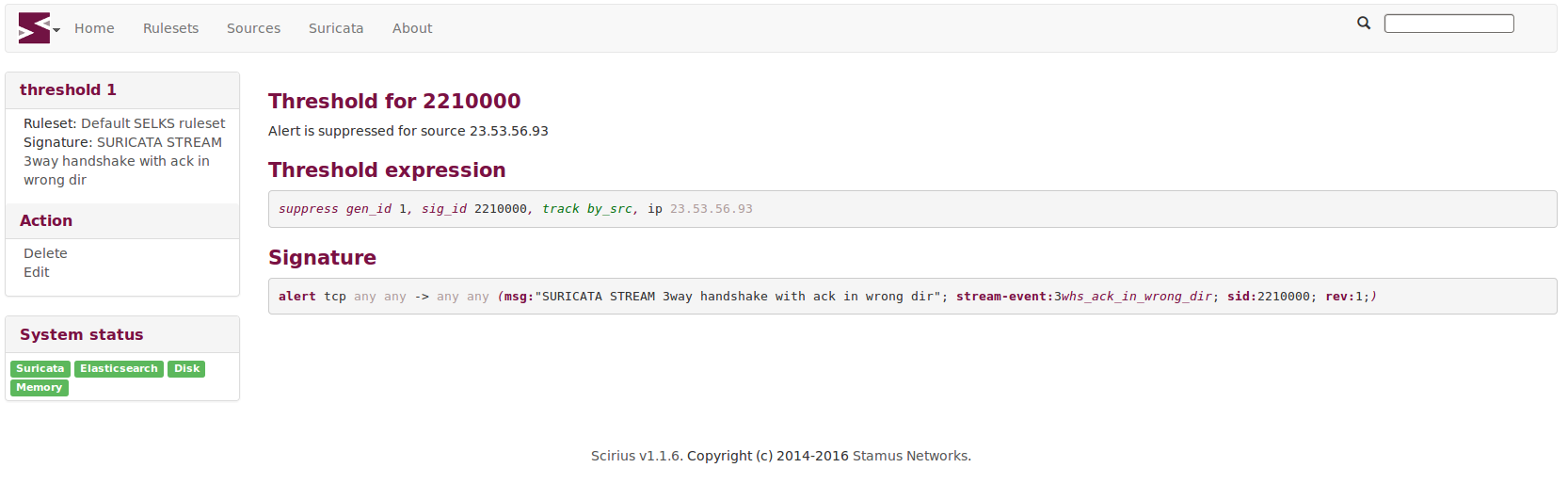
This is a short tutorial of how you can find and store to disk a self signed TLS...
Stamus Networks is proud to announce the availability of SELKS 2.0 release.
Stamus Networks is proud to announce the availability of SELKS 2.0 BETA1 release. With Jessie...
Stamus Networks is proud to announce the availability of SELKS 1.1 stable release. SELKS is both...
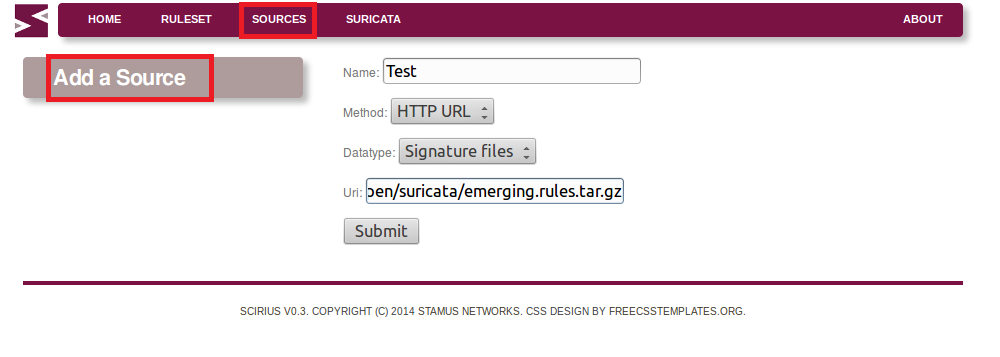
Stamus Networks supports its own generic and standard Debian Wheezy 64 bit packaging repositories...
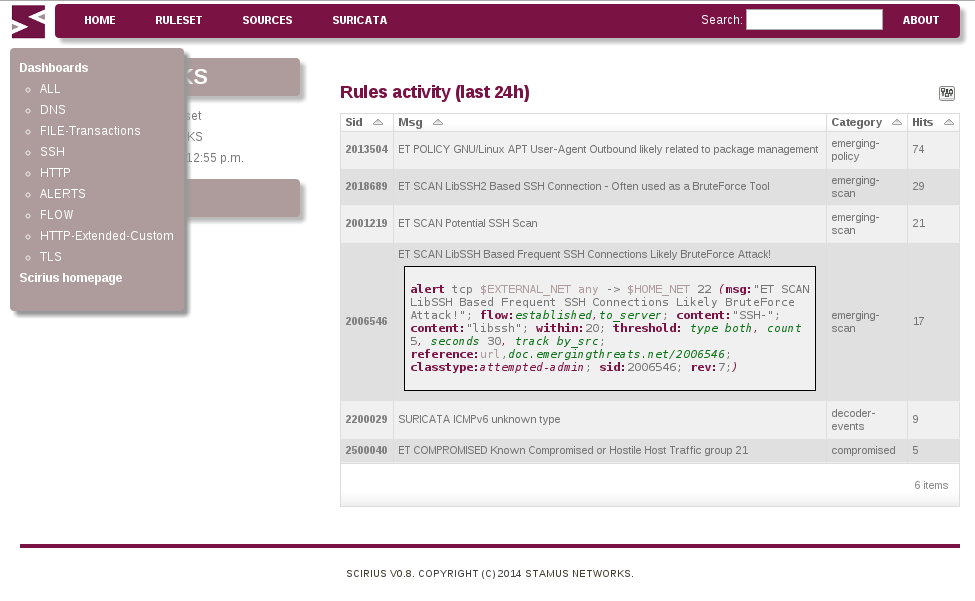
Stamus Networks is proud to announce the availability of SELKS 1.0 stable release. SELKS is both...
Stamus Networks is proud to announce the availability of SELKS 1.0 RC1. This is the first release...
The Ubuntu used in this tutorial: