Stamus Security Platform is loaded with features that help security teams leverage network traffic to automatically detect threats against their organizations. In addition to deploying automated threat detection, many large organizations proactively hunt for threats on the data generated by their monitoring systems. When this is the case, defenders need a starting point to look for specific types of threats and other suspicious network activity.
This weekly series will explore the various guided threat hunting filters included in the Stamus Enriched Hunting interface, as well as different steps security practitioners can take upon successful completion of a hunt to stop threats on their network before it's too late.
Introduction to Stamus Security Platform
Stamus Security Platform is a broad-spectrum and open network detection and response (NDR) system that delivers:
- Automated response-ready and high-fidelity threat detection from machine learning, stateful logic, and signatures
- Open interfaces for integration with SOAR, SIEM, XDR, IR, or EDR
- Support for third-party and custom threat intelligence
- Explainable and transparent results – with evidence
- Integrated guided threat hunting
Our threat hunting expertise has been tested and refined by our participation in some of the world’s biggest live fire cyber exercises such as Cross Swords and Locked Shields.
Guided Threat Hunting Overview
One of the most useful features built into the Stamus Security Platform is the integrated guided threat hunting. The user interface, called “Enriched Hunting” empowers users to investigate, classify, escalate, and automate vast amounts of event data, alerts, and contextual metadata using beyond the typical automated threat detection functionality of the system. This gives users the ability to proactively search for threats or investigate areas of special interest in a structured way.
Enriched threat hunting also lets users create their own hunting filters and turn their ideas into automated processes. The enriched hunting interface's main purpose is for proactive defense, however it also provides resources for knowledge transfer from experienced analysts to less-experienced personnel. This series will cover a new hunting filter each week where we will detail the path Stamus Security Platform guides you on, information on the threat type, as well as the steps you can take after the hunt to automate and further streamline your threat hunting experience.
Before beginning the weekly series, we want to provide an overview of the Stamus Security Platform integrated threat hunting interface, and highlight several unique features available to users.
Dashboard
The Enriched Hunting dashboard serves as the main overview to the threat hunting tool. It includes over 50 elements of event metadata that can be viewed at a quick glance. It also includes pivoting capabilities for connection and correlation to other hunting tools.
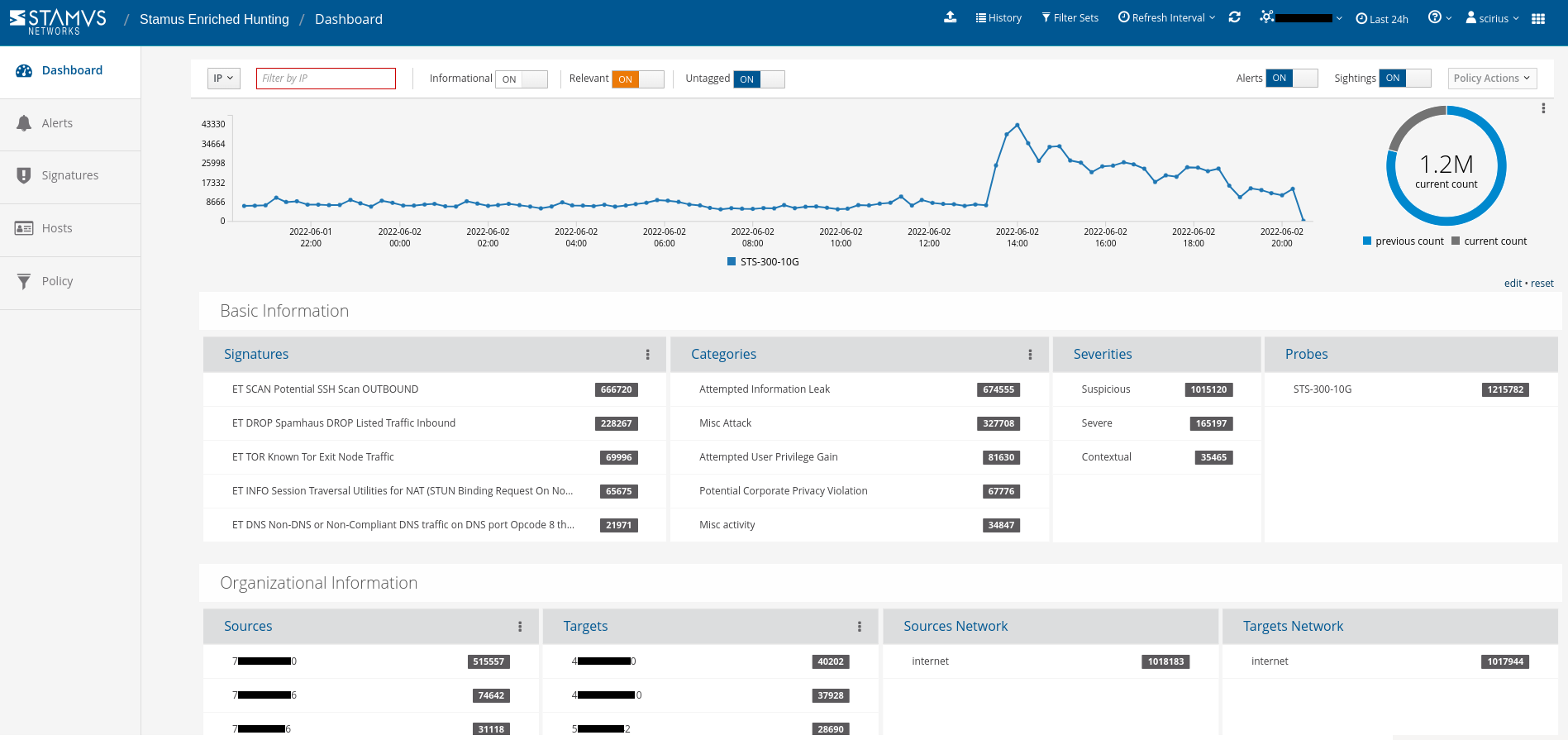
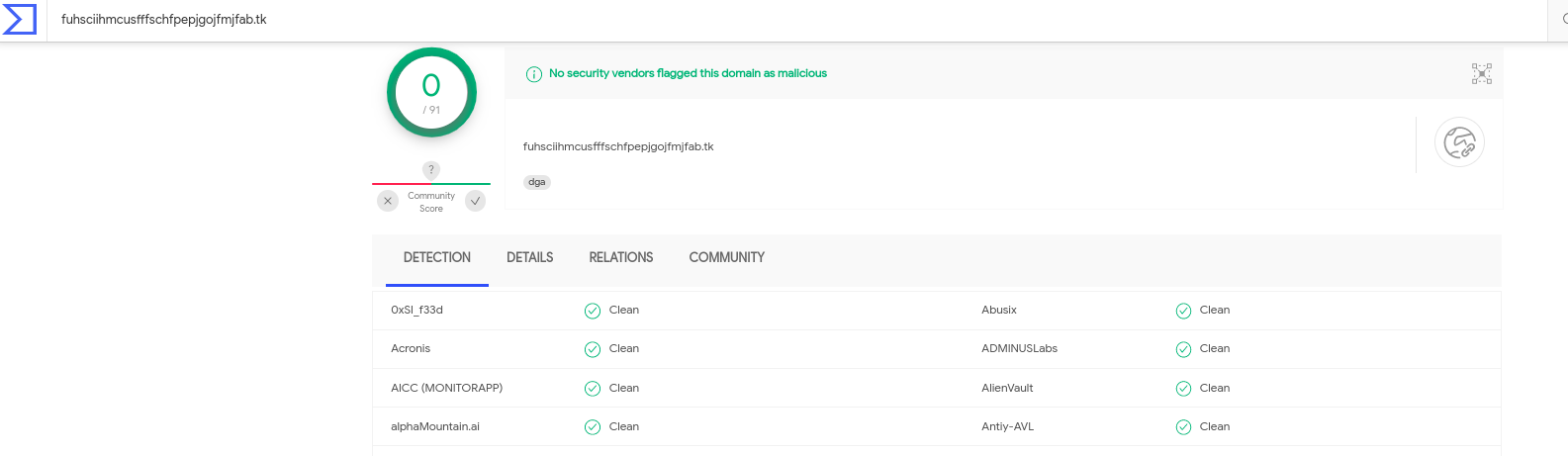
Security analysts can use any piece of metadata to create simple or complex filters for things like wildcarding, negation, or inclusion. You can even include multiple fields for fast drill down capabilities. All domains, TLS SNI, IP addresses, HTTP hosts, and more can easily be checked with an external threat intelligence provider such as Virus Total.
Hunting Tools
The Stamus Enriched hunting module (as part of Stamus Security Platform) has a few major components that help the hunters in various daily tasks:
- Guided hunting filtersets
- Context and classification
- Previously unseen communications
- Metadata search tools
- Host Insights
- Automation
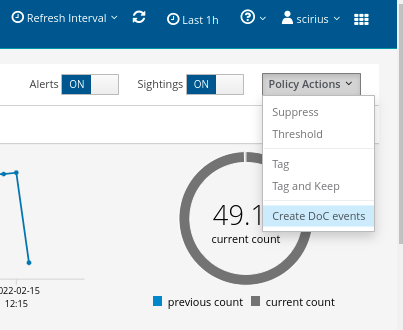
Automation
Any existing or created filter-set (whether local or global) can be used to:
- Create thresholding or suppression (to tackle the noise)
- Auto classify any occurrences that match the filter-set
- Escalate:
- To Stamus Security Platform/STR
- Create a mail or SoC chat notification
- (via a webhook) Auto open Incident Response ticket or trigger a SOAR/EDR action - such as network quarantining an endpoint.
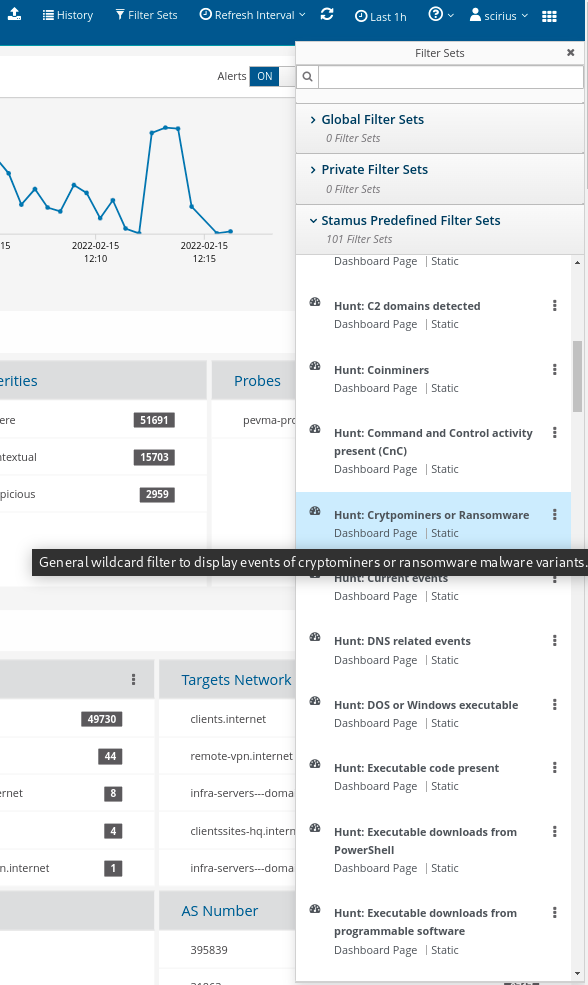
Guided Hunting Filter-Sets
Stamus Enriched hunting comes with over 111 ready to use guided hunting filtersets. Apart from that, any other custom filterset can be created and is limited only by the hunter’s imagination and ideas.
The filter-sets hold a very powerful hunting advantage because they can display anything from an alert event to a new proxy, printer, domain controller, or network service in the enterprise. For example, a new python based web server in the marketing department can be displayed with just a quick click.
Contextual Data
Any events that get displayed include contextual data like raw logs, related network transaction protocol data (file transactions/htp/tls/dns/flow etc), other alerts, payloads, and even extracted files.
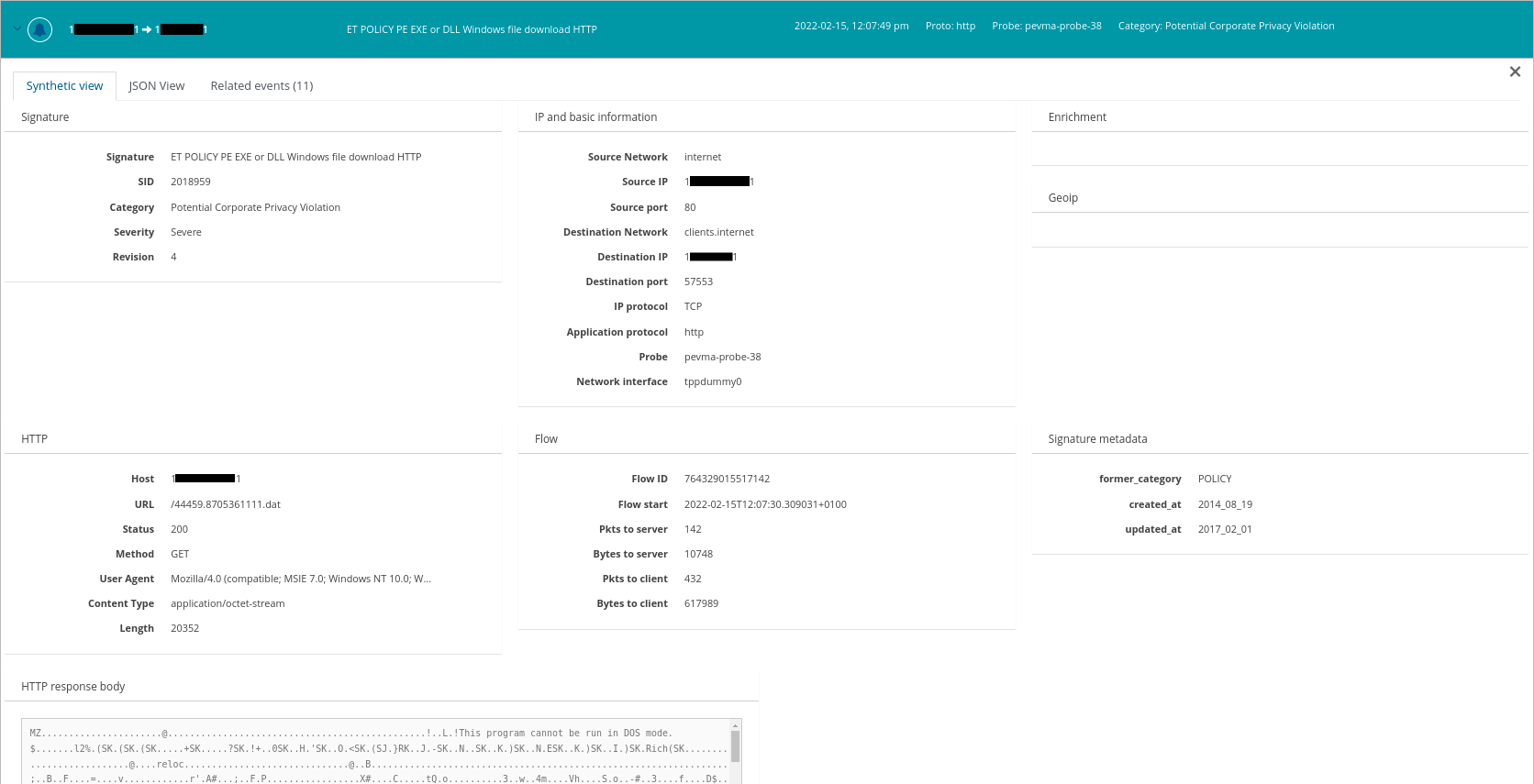
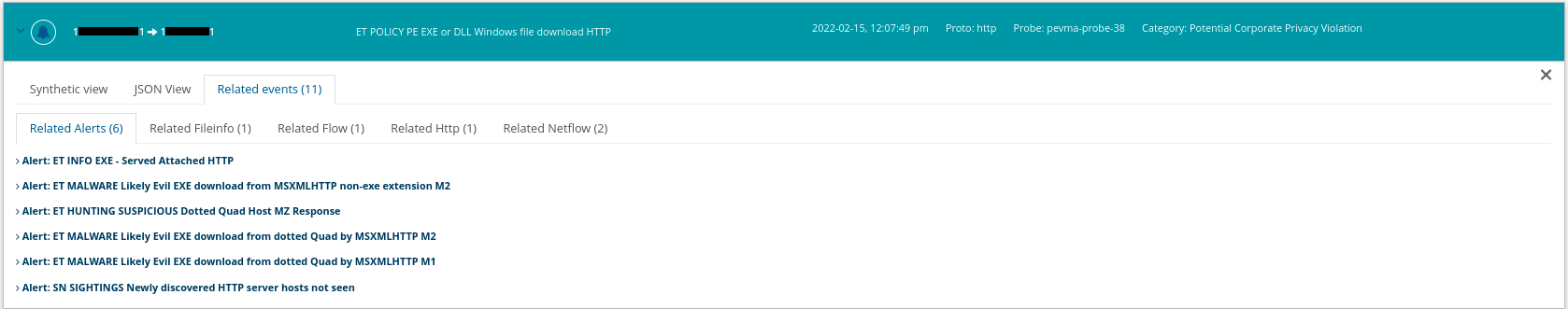
For example, in addition to the alert itself, we can see here that there are 11 other related events.
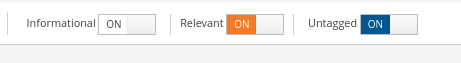
Classification
Viewing both classified and unclassified data is performed with a simple switch. By toggling the needed switches, you can quickly view informational, relevant, and/or unclassified events.
Previously Unseen Communications
In the Stamus Security Platform previously-unseen communications are labeled as “Sightings”.
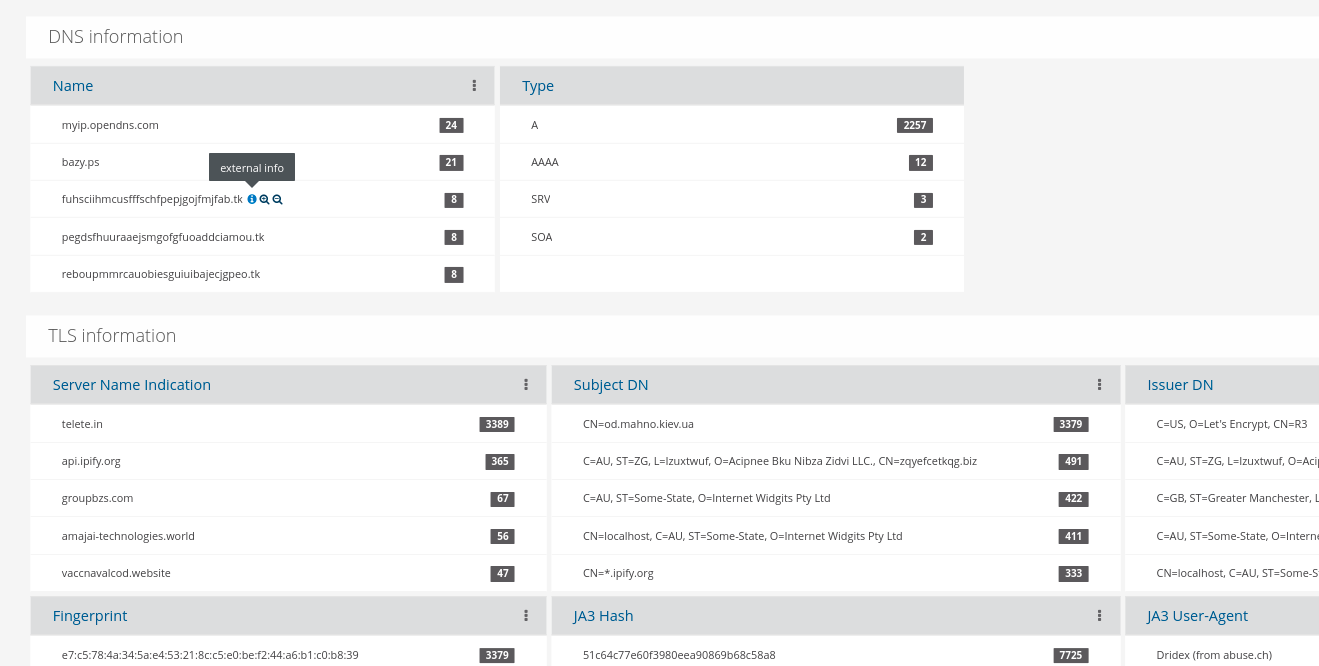
Knowing when certain communication metadata pieces are being seen on the network for the first time provides a big advantage to any hunter. Here, the analyst may view first time sightings of domain queries, HTTP hosts, JA3, JA3S, SMB file transfers, TLS certificates, TLS SNI, and more.
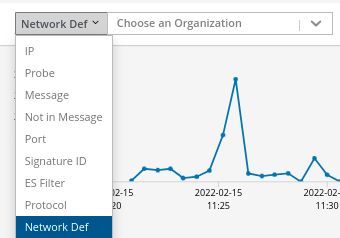
Metadata Search Tools
A drop down tool box is available to allow for easy selection of data aspects. You can even use organizational-specific network definitions to filter the search using context specific to your organization.
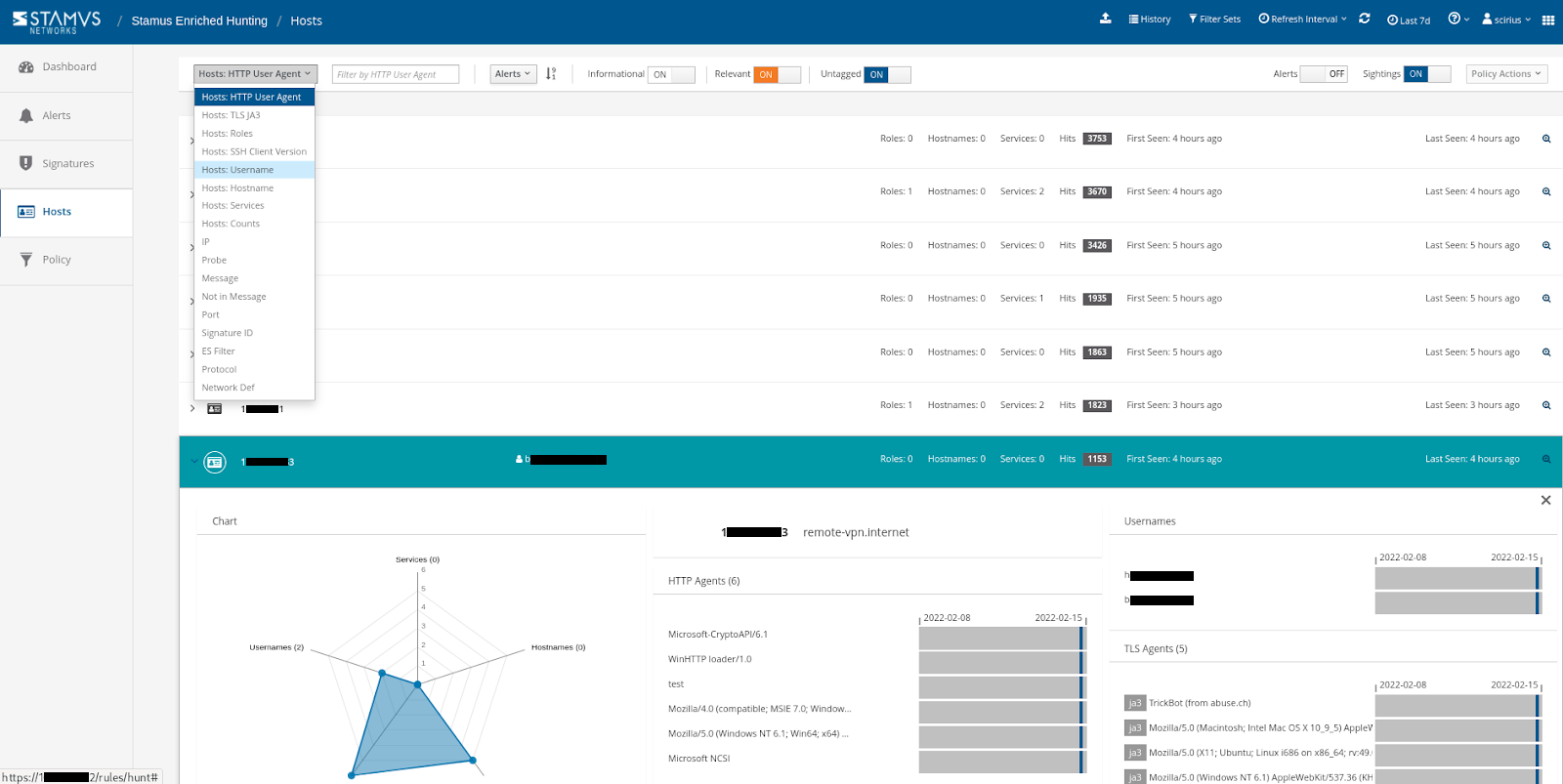
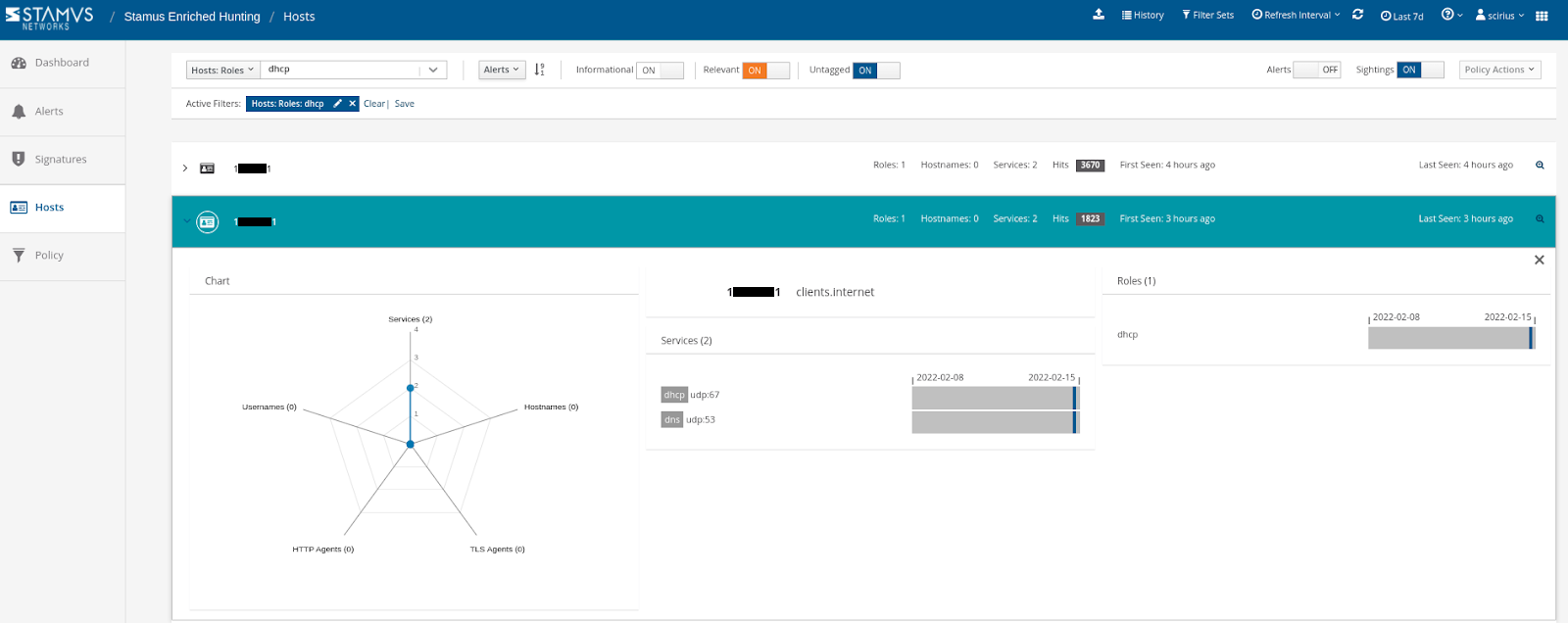
Host Insights
The “Host Insights” feature tracks over 60 security-related network transactions and communication attributes of a host. This provides a single place to view many aspects of the network activity relative to a given host, such as network services, users, or TLS fingerprinting forensic evidence.
Conclusion
Enriched Threat Hunting on the Stamus Security Platform (SSP) goes beyond just locating potential threats. It can be used to identify policy violations such as the presence of shadow IT. Additional features allow for automation and escalation, which enable the user to take action after a threat has been found.
For more information on what actions you can take after a threat has been found, read our “After the Hunt” feature article. In it we detail the ways security teams can use those automation and escalation tools to know more, respond sooner, and mitigate risk for their organizations.
To learn more about Network Detection and Response (NDR) from Stamus Networks or the included Stamus Enriched Hunting interface, click on the link below to schedule a demo.







