Suricata Language Server 1.3.0 is now available and it surfs on the concept of magic comment...
Writing and validating Suricata signatures shouldn't require wrestling with complex installation...
Modern security operations face an impossible challenge: the volume and complexity of threats have...
We are pleased to share the news that Stamus has released Clear NDR® Enterprise (formerly known as...
Security operations centers (SOCs) are drowning in a deluge of alerts. Millions of network events...
While detecting malicious attacks is critical for preventing a serious security incident, ensuring...
Security teams are often overwhelmed by a flood of alerts, leading to alert fatigue and missed...
In today's rapidly evolving threat landscape, network detection and response (NDR) solutions play a...
In recent years, AI-based anomaly detection has become a cornerstone of network security marketing....
In today's complex threat landscape, cybersecurity teams face an overwhelming challenge: detecting...
For security teams using Darktrace and similar anomaly-based NDR solutions, the scenario is all too...
For many organizations considering Network Detection and Response (NDR), one of the most valuable...
In recent years, we've observed a notable trend: sophisticated security operations centers (SOCs)...
Stamus Networks will be exhibiting Forum InCyber, one of Europe’s leading cybersecurity events,...
This blog post details how Clear NDR drastically reduces Mean Time to Detect (MTTD) and Mean Time...
For many organizations considering Network Detection and Response (NDR), one of the most valuable...
Analysts in a SOC use many different tools on a daily basis. When hunting for security incidents,...
For many organizations considering Network Detection and Response (NDR), one of the most valuable...
As all cybersecurity defenders know, visibility into the network is the key to understanding what...
One of the new, exciting innovations available with the release ofClear NDRTM U40 is the inclusion...
In this series of articles, we explore a set of use cases that we have encountered in real-world...
In this series of articles, we explore a set of use cases that we have encountered in real-world...
In this series of articles, we explore a set of use cases that we have encountered in real-world...
In November of 2022 we announced a Suricata ruleset specifically focused on detecting lateral...
This article describes the details of the new Open NRD threat intelligence feeds provided by Stamus...
This week’s guided threat hunting blog focuses on hunting for high-entropy NRD (newly registered...
One of the unique innovations in Clear NDRTM is the feature known as Declaration of Compromise™...
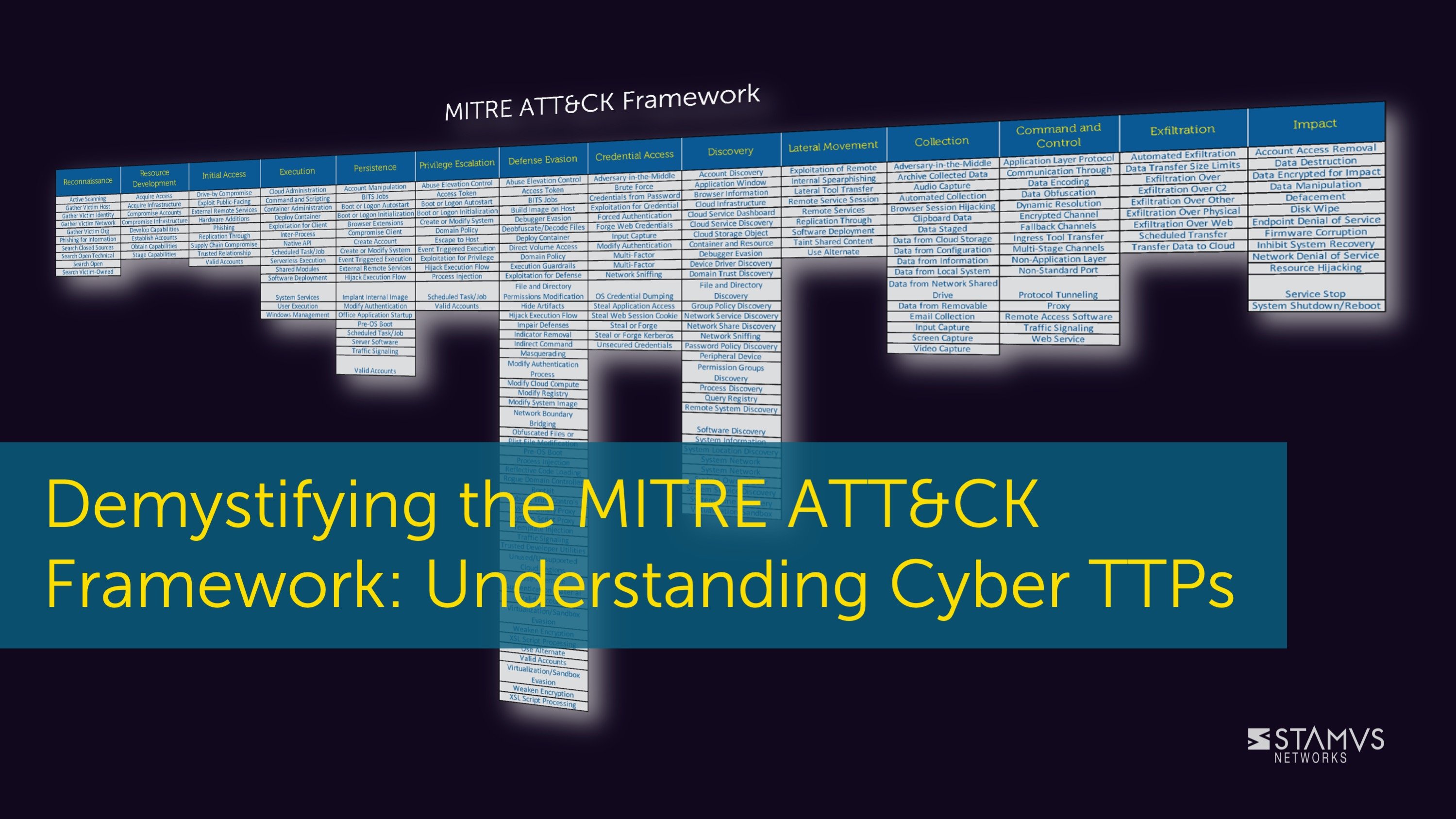
When an organization wants to learn more about the tactics, techniques, and procedures (TTP) used...
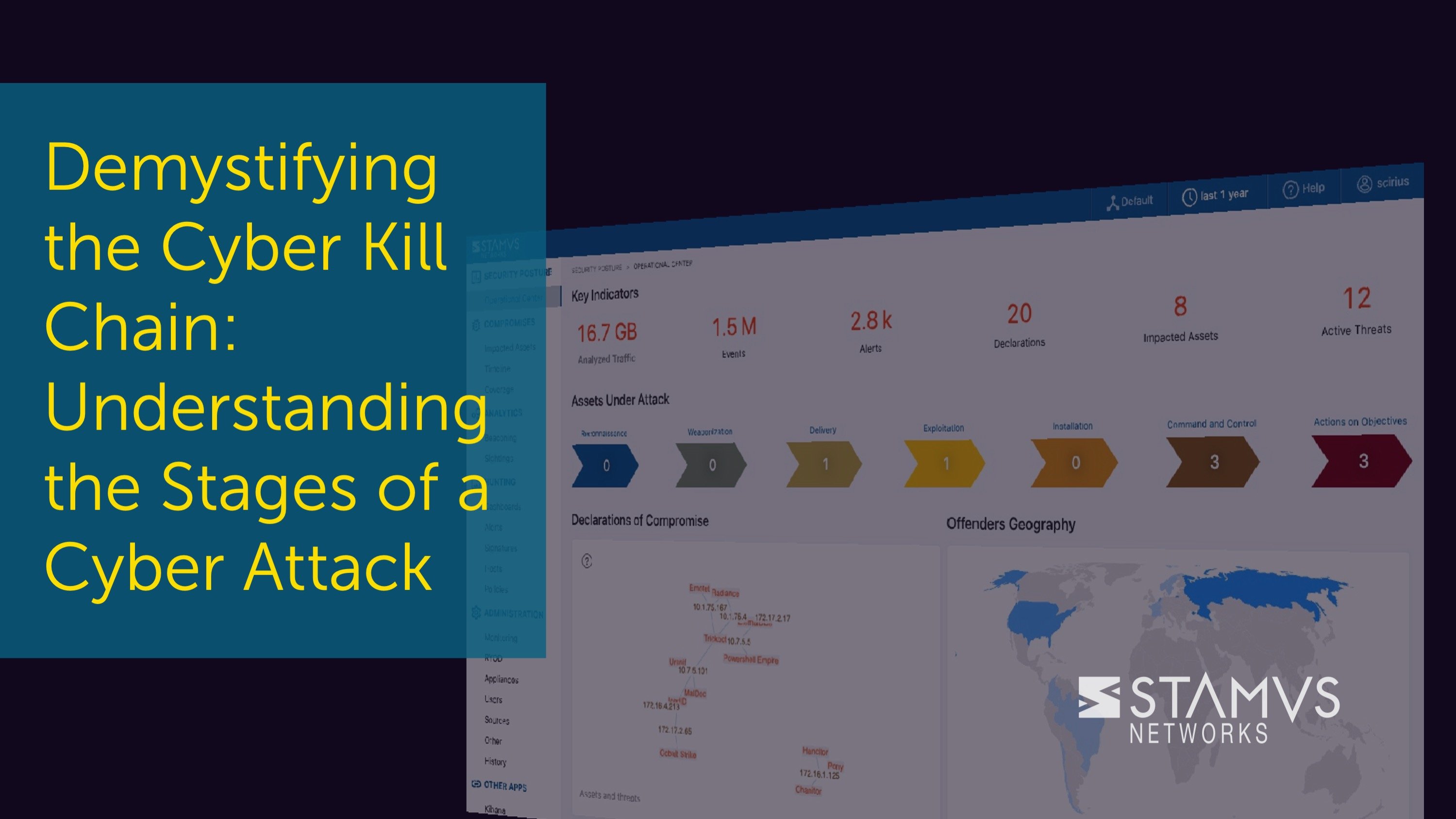
The cyber kill chain is a widely-used framework for tracking the stages of a cyber attack on an...
Intrusion Detection Systems (IDS) can be powerful threat detection tools, but IDS users frequently...
This week’s guided threat hunting blog focuses on verifying a policy enforcement of domain...
It is not uncommon to see executable file transfers within an organization. However, it is...
Punycode domains have traditionally been used by malware actors in phishing campaigns. These...
When you see a domain request from a user/client to a non-local or otherwise unfamiliar or...
Non-local domain requests from the user/client network could signal trouble for an organization....
DNS over HTTPS (DoH) is a network protocol designed to enhance user privacy by encrypting DNS...
Plain text executables (such as those downloaded from a PowerShell user agent) are often seen on...
This week in our series on guided threat hunting, we are focusing on locating internal use of...
This week’s guided threat hunting blog focuses on hunting for foreign domain infrastructure usage...
This week’s guided threat hunting blog focuses on hunting for Let’s encrypt certificates that were...
In this week’s guided threat hunting blog, we will focus on hunting for Let’s Encrypt certificates...
In this week’s guided threat hunting blog, we focus on using Clear NDR to identify rogue proxy...
In this week’s guided threat hunting blog, we focus on using Clear NDR to uncover phishing...
In this series of articles we share hands-on experience from active hunts in the real world. We...
In this series of articles, we explore a set of use cases that we have encountered in real-world...
When the blue team needs to mount a network defense, they must answer some very common questions:
- ...
Clear NDRTM helps bank identify threat to its accounting network
With the help of the Clear NDR, ...
In this series of articles, we explore a set of use cases that we have encountered in real-world...
In this series of articles, we will explore a set of use cases that we have encountered in...




.jpg)