This blog describes the steps Stamus Networks customers may take to determine if any of your...
Budgets may not be shrinking, but they certainly aren’t keeping up with the complexity and scale of...
Cloud adoption continues to grow, but so do the challenges security teams face in detecting and...
When CISA released version 2.0 of its Cross-Sector Cybersecurity Performance Goals last week, the...
Alert fatigue - the condition that arises from being overwhelmed by millions of vague alerts and...
Security teams are under tremendous pressure. Cloud complexity, alert fatigue, staffing shortages,...
Modern security operations face an impossible challenge: the volume and complexity of threats have...
We are pleased to share the news that Stamus has released Clear NDR® Enterprise (formerly known as...
In today's complex threat landscape, organizations of all sizes need robust network visibility and...
Security operations centers (SOCs) are drowning in a deluge of alerts. Millions of network events...
While detecting malicious attacks is critical for preventing a serious security incident, ensuring...
tl;dr
This article explores the integration of NixOS, a declarative Linux distribution, with...
Security teams are often overwhelmed by a flood of alerts, leading to alert fatigue and missed...
Modern IT infrastructure, whether traditional or hybrid, faces persistent challenges: staff...
One of the significant advantages of Clear NDR’s multi-layered detection is its ability to identify...
Suricata Language Server (SLS) has been available for more than 3 years, and it has always been...
The example outlined in this blog article demonstrates Clear NDR’s value in delivering visibility...
The following example is of an unstructured hunt technique—an investigation based on an idea or...
One of the key strengths of Clear NDRTM is its AI-based TLS beacon detection, which, when combined...
In recent years, AI-based anomaly detection has become a cornerstone of network security marketing....
For security teams using Darktrace and similar anomaly-based NDR solutions, the scenario is all too...
For many organizations considering Network Detection and Response (NDR), one of the most valuable...
In recent years, we've observed a notable trend: sophisticated security operations centers (SOCs)...
This blog post details how Clear NDR drastically reduces Mean Time to Detect (MTTD) and Mean Time...
NOTE: The following article was originally published 06 December 2024 on VMblog.com
At Stamus Networks, we have always been driven by a commitment to openness, transparency, and...
For many organizations considering Network Detection and Response (NDR), one of the most valuable...
Determining whether or notNetwork Detection and Response (NDR) is right for your organization, and...
The rapid proliferation of IoT devices, network devices, and cloud infrastructure has drastically...
As any seasoned security professional will likely tell you, detecting a threat is only part of the...
Over the course of the last decade, Network Detection and Response (NDR) naturally evolved out of...
Today, we are proud to announce the general availability of Update 40 (U40) - the latest release of...
The recent global outage caused by an update to CrowdStrike Falcon, CrowdStrike's endpoint...
The recent global outage caused by an update to CrowdStrike Falcon, CrowdStrike's endpoint...
In this series of articles, we explore a set of use cases that we have encountered in real-world...
Tl:DR: A Large U.S. university lacked sufficient visibility into a large segment of its environment...
TL;DR: An American school district needed to monitor over 5000 school-owned student devices, making...
TL;DR: A European managed security service provider seeking to launch an MDR service chose Stamus...
Network detection and response (NDR) is a critical component of a comprehensive cyber defense...
This week we announced that an important new software release Update 39.1 (or “U39.1”) for our...
In an era of rapidly advancing technology and digital transformation, the realm of cybersecurity is...
This article describes the details of the new Open NRD threat intelligence feeds provided by Stamus...
For a large organization, keeping track of numerous security systems or internal security policies...
In our past series, “Threat! What Threats?” we covered the topic of phishing in a generic way, but...
Every day, new Internet domains are registered through the Domain Name System (DNS) as a natural...
One of the unique innovations in Clear NDRTM is the feature known as Declaration of Compromise™...
The cyber kill chain is a widely-used framework for tracking the stages of a cyber attack on an...
Network security plays a crucial role in today's digital landscape as it safeguards sensitive...
Cyber threats are becoming increasingly sophisticated and pervasive, causing organizations to place...
Threat hunting is a common practice for many mature security organizations, but it can be time...
Clear NDRTM users can now integrate the Malware Information Sharing Platform (MISP) to supplement...
Intrusion Detection Systems (IDS) can be powerful threat detection tools, but IDS users frequently...
In a recent conversation, one of our customers shared their concerns about the use of ChatGPT in...
This blog describes the steps Stamus Networks customers may take to determine if any of your...
When it comes to cyber threats, we understand that a threat to one organization can quickly become...
Maintaining an effective security posture is difficult enough for any organization. But for those...
When you already know the specific attacks faced by your organization, then the basic detection...
Intrusion detection systems (IDS) function incredibly well when it comes to making signature based...
This blog describes the steps Stamus Networks customers may take to determine if any of your...
Command-and-control (C2) attacks are bad news for any organization. Attackers use C2 servers to...
Intrusion detection systems (IDS) have proven to be a highly effective and commonly used method of...
This week’s threat detection blog dives deeper into a common type of malware, remote access trojans...
In this week’s threat detection blog, we will be reviewing a financially-motivated threat that is...
This week we are taking a closer look at Shadow IT, which is the use of information technology by...
Phishing is commonly regarded as the most common and effective way attackers can gain access into a...
In this article, we will review one of the most important and critical phases on the cyber kill...
One of the first network-related indications of a botnet or peer-to-peer (P2P) malware infection is...
In this article I want to highlight one of the tactics used by malicious actors to move within your...
In the first article of this series -- Threats! What Threats? -- I mentioned that my colleague,...
In this series of articles we share hands-on experience from active hunts in the real world. We...
Existing systems that aggregate network security alerts and metadata do not properly detect and...
In the first article of this series –Threats! What Threats? – I mentioned that my colleague, Steve...
We talk often about “threats” and “threat detection” in our marketing materials and in discussions...
In this series of articles, we explore a set of use cases that we have encountered in real-world...
In the previous article of the “Feature Spotlight” series, we discussed how to pivot from IDS alert...
Sometimes, even after extensive training, we forget about important features or ways of using a...
So, you are considering migrating your legacy or aging intrusion detection and prevention system...
So, you are considering migrating your legacy or aging intrusion detection and prevention system...
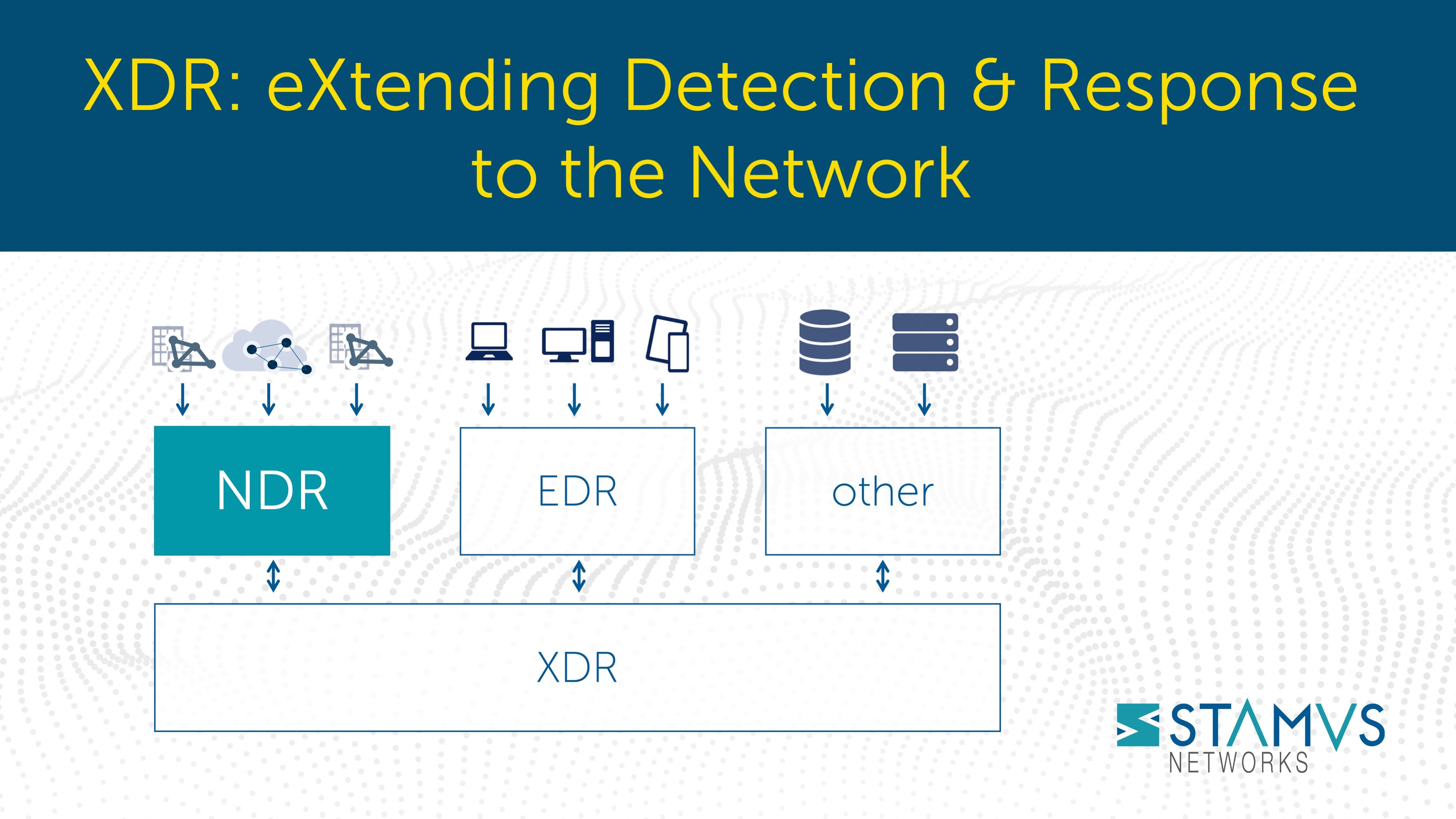
Extended detection and response, or XDR, has generated substantial interest in recent years - and...
On 16 November 2021, my colleague Ed Mohr and I will be giving our second talk entitled “The Case...
On 12 October 2021, my colleague Ed Mohr and I will be giving a talk entitled “The Case for...
When the blue team needs to mount a network defense, they must answer some very common questions:
- ...
In my last blog article, I introduced some of the factors that have contributed to our successes...
In cybersecurity as soon as you stand still, you’re falling behind. Change, whether it’s in the...
Clear NDRTM helps bank identify threat to its accounting network
With the help of the Clear NDR, ...
In this series of articles, we explore a set of use cases that we have encountered in real-world...
Recently, Stamus Networks introduced outgoing webhook capabilities to its Stamus Security Platform....
Threat hunting—the proactive detection, isolation, and investigation of threats that often evade...
In this series of articles, we will explore a set of use cases that we have encountered in...
Stamus Networks? They are the Suricata company aren’t they? And Suricata? It’s an open source IDS...
As mentioned in an earlier article, organizations seeking to identify cyber threats and mitigate...
Organizations seeking to proactively identify and respond to cyber threats in order to mitigate...
Sometimes the greatest vulnerabilities and risks an organization faces are created by users'...
Today we announced the general availability of Scirius Threat Radar (now called Stamus NDR), a...
Every great story begins with the first chapter. And with each new chapter the characters develop...
Following the release of Scirius Community Edition 2.0, Stamus Networks is happy to announce the...








.jpg)
.jpg)
























































.jpg)