This blog describes the steps Stamus Networks customers may take to determine if any of your...
Cloud adoption continues to grow, but so do the challenges security teams face in detecting and...
When CISA released version 2.0 of its Cross-Sector Cybersecurity Performance Goals last week, the...
Alert fatigue - the condition that arises from being overwhelmed by millions of vague alerts and...
Security operations centers (SOCs) are drowning in a deluge of alerts. Millions of network events...
While detecting malicious attacks is critical for preventing a serious security incident, ensuring...
Security teams are often overwhelmed by a flood of alerts, leading to alert fatigue and missed...
In today's complex threat landscape, cybersecurity teams face an overwhelming challenge: detecting...
For security teams using Darktrace and similar anomaly-based NDR solutions, the scenario is all too...
In recent years, we've observed a notable trend: sophisticated security operations centers (SOCs)...
For many organizations considering Network Detection and Response (NDR), one of the most valuable...
For many organizations considering Network Detection and Response (NDR), one of the most valuable...
Determining whether or notNetwork Detection and Response (NDR) is right for your organization, and...
The rapid proliferation of IoT devices, network devices, and cloud infrastructure has drastically...
As any seasoned security professional will likely tell you, detecting a threat is only part of the...
One of the unique innovations in Clear NDRTM is the feature known as Declaration of Compromise™...
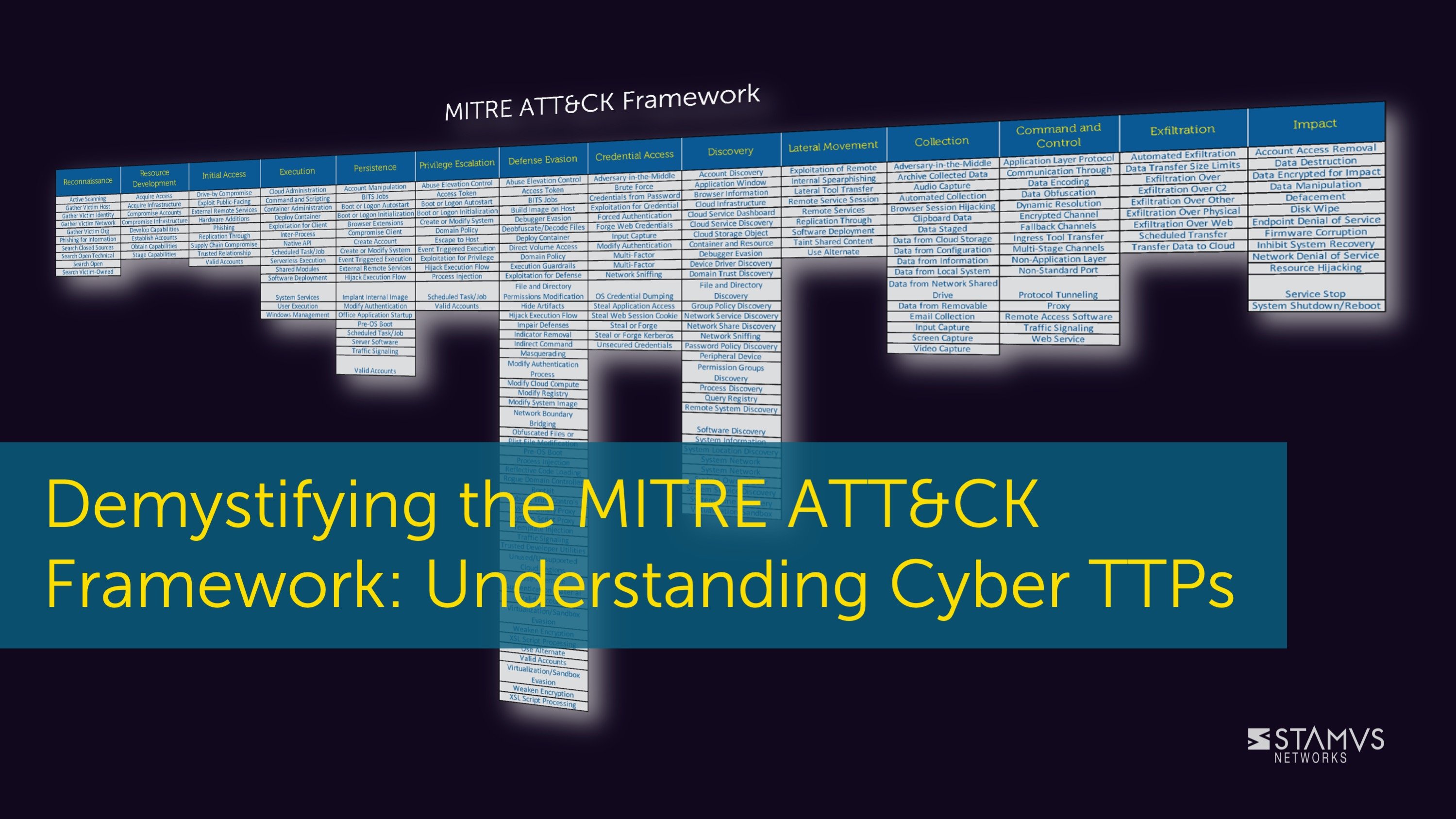
When an organization wants to learn more about the tactics, techniques, and procedures (TTP) used...
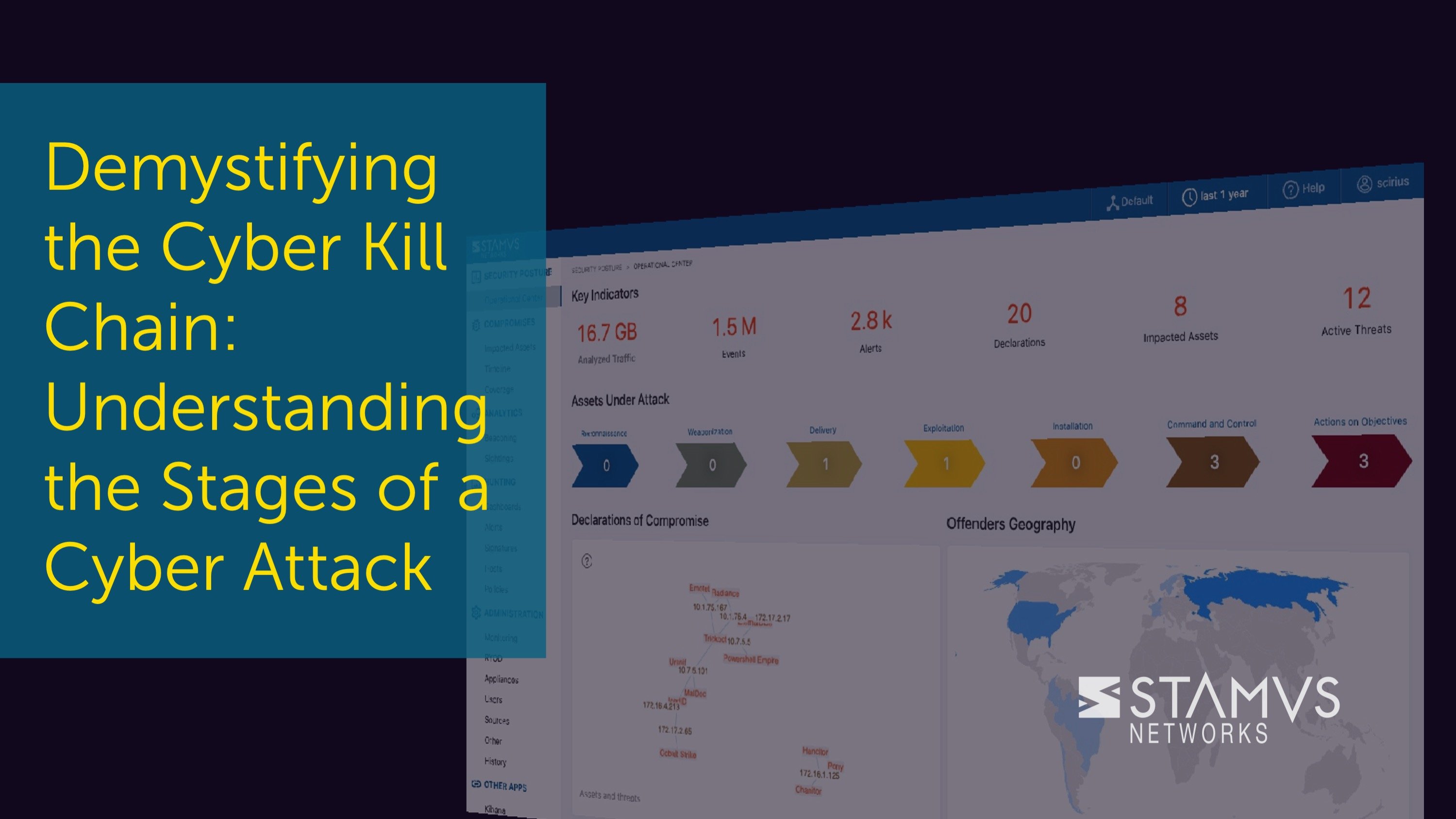
The cyber kill chain is a widely-used framework for tracking the stages of a cyber attack on an...
Threat hunting is a common practice for many mature security organizations, but it can be time...
Intrusion Detection Systems (IDS) can be powerful threat detection tools, but IDS users frequently...
So, what’s next? You’ve had a successful hunt, uncovered some type of threat or anomalous behavior...
Existing systems that aggregate network security alerts and metadata do not properly detect and...