This week’s guided threat hunting blog focuses on policy violations; specifically, violations centered around the use of unauthorized file sharing services used by members of your organizations. Security teams set certain policies in order to ensure safe practices across the network, so it is important that they have the ability to see when these policies are violated. This is where guided threat hunting with a policy violation filter can help.
Stamus Security Platform (SSP) is adept at automatically detecting and identifying threats present on the network, and presenting security teams with incident timelines and extensive context for each threat. Many organizations take advantage of advanced SSP features and take an even more proactive approach to their defenses. When this is the case, they might task a security analyst with hunting for specific threat types, anomalous activity, or suspicious behaviors. To do this, they can use the Stamus Enriched Hunting Interface.
This interface provides users with over 100 ready-to-use guided threat hunting filters, including various filters centered on different types of policy violations, that they can follow to investigate, classify, escalate, and automate vast amounts of event data, alerts, and contextual metadata. For a more detailed look at the Enriched Hunting Interface, read our blog titled, “Introduction to Guided Threat Hunting”.
How can using a file sharing service be a policy violation?
Many policy violations do not involve malicious intent, but rather from an employee’s desire to make their work more efficient and productive. While the intentions are good, the practice can leave the organization open to attacks. This is the case with file sharing service policy violations.
Online sharing services - dropbox, onedrive, google drive, transfer.sh, etc - are valuable resources for file sharing in a work setting, but when services are used that have not been approved and secured by the IT department there is a potential for attackers to gain access into the network. This can cause data leaks, lead to breaches, allow malicious software to be installed, or have other negative consequences. Sometimes, it is not the file sharing service by itself that is the issue. Rather, it is the accessing of these services from an employee’s unsecure home network that can lead to an attacker’s entry into the network or access to sensitive data.
Identifying file sharing service policy violations using Stamus Security Platform
The enriched hunting interface provides a filter that guides hunters to find this exact type of activity within their organization’s infrastructure using insights gathered from the network. Let’s take a look at an example:
In the past 48 hours, we have had about 1.6 million alert events which have triggered hundreds of thousands of results.
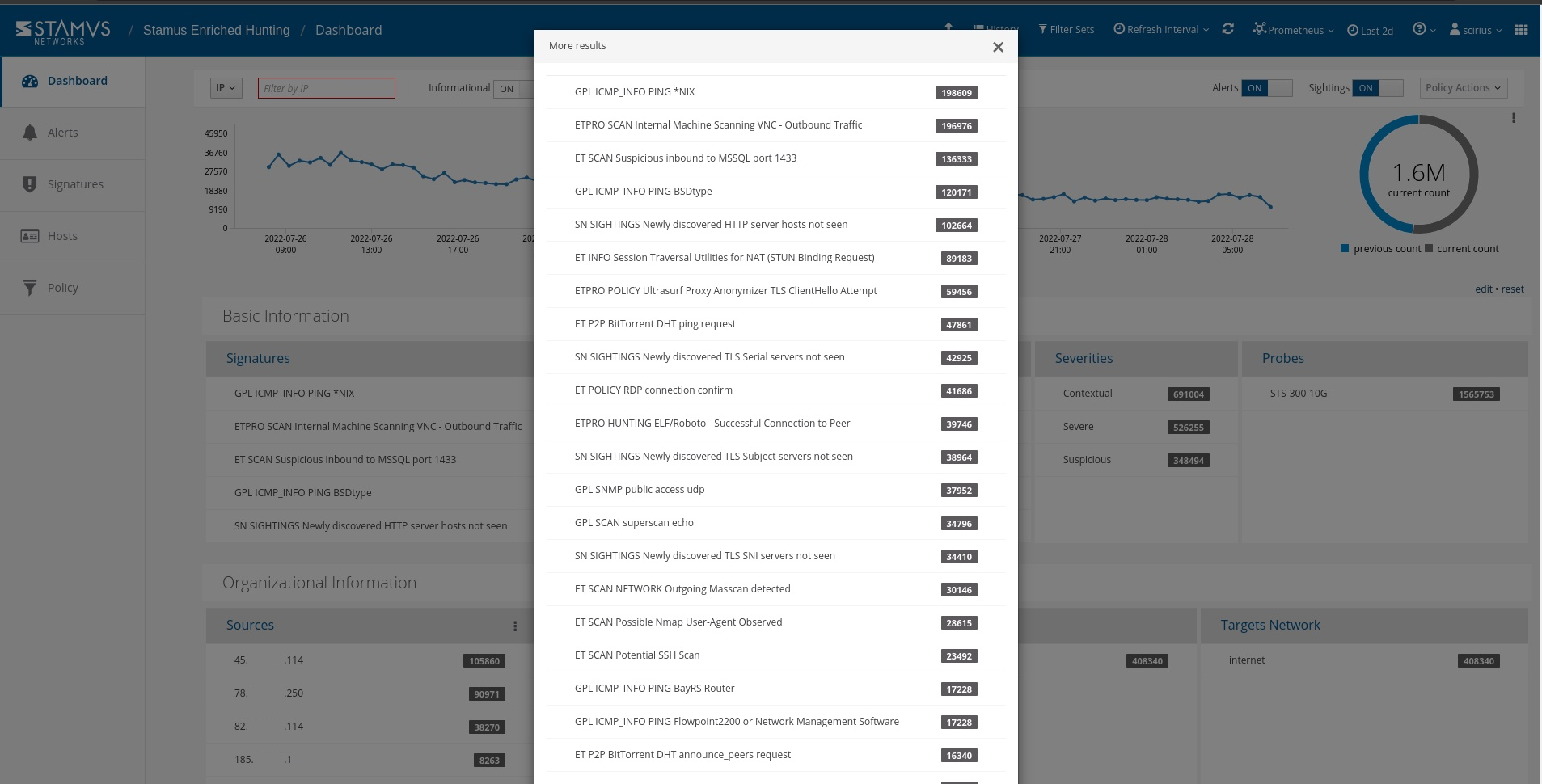
The Hunt for Sharing Service Policy Violations
To begin this hunt, we first have to select the relevant filter from the drop down list. Since there are over 100 guided hunting filters, we need to narrow the list down and find the filter we want. To do this, we can search for “policy” and then select the needed filter. In this example, the filter is titled, “Policy: Abused file sharing hosting”.
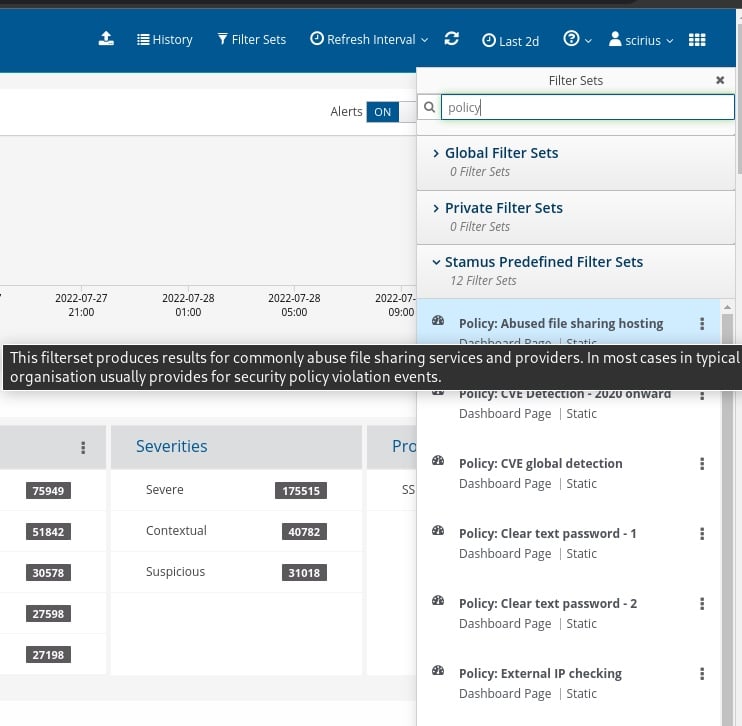
Selecting this filter narrows our results from 1.6 million down to only 3 in the selected timeline. This gives us an excellent starting point to work from.
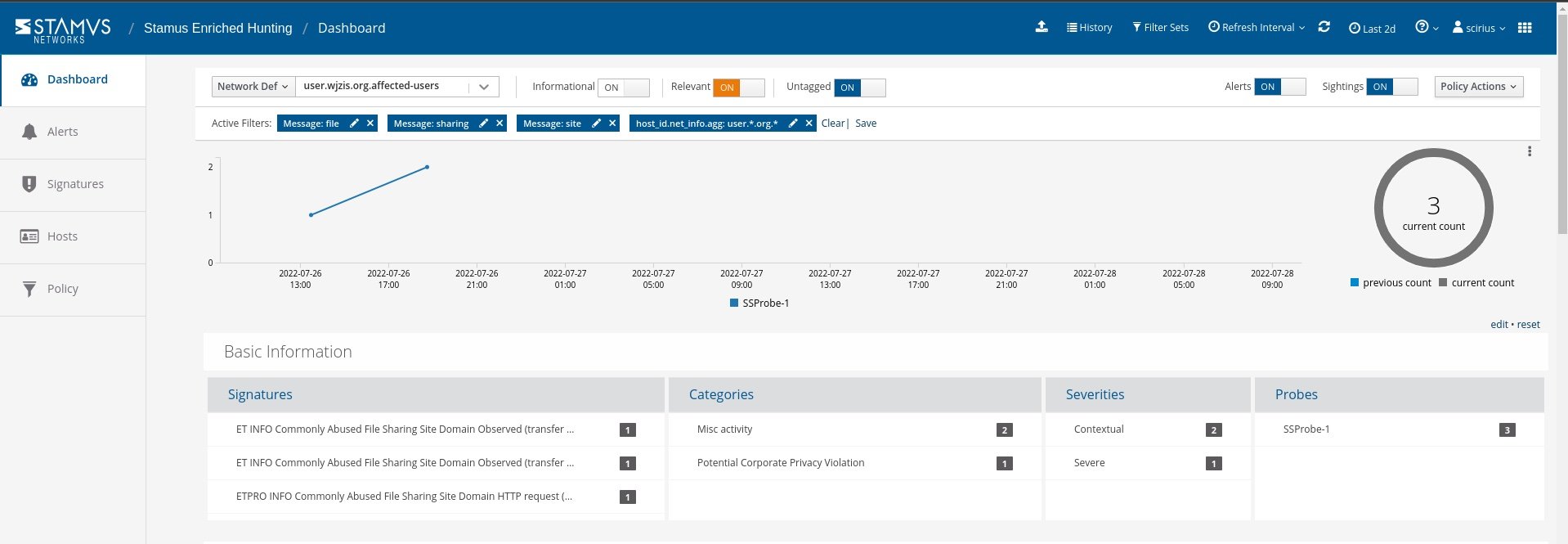
It is important to note that SSP enriched hunting also provides additional organization-specific context. Users can filter for queries from various departments or user groups within the organization, allowing them to hyper-focus on specific areas without having to aggregate events or organize IP addresses to find specific users or departments.
Evidence for Incident Response
With just a few clicks, We are able to view two important sets of evidence:
- The associated network protocol transactions and flow logs
- Host Insights - a single screen for reviewing 60+ network activity attributes collected for every host
The generated events are already enriched by SSP to include important metadata like DNS records, TLS protocol data containing certificate names, fingerprint JA3/JA3S, connection flow sizes, http user agent, http host, request body, status codes, file transaction info, and more.
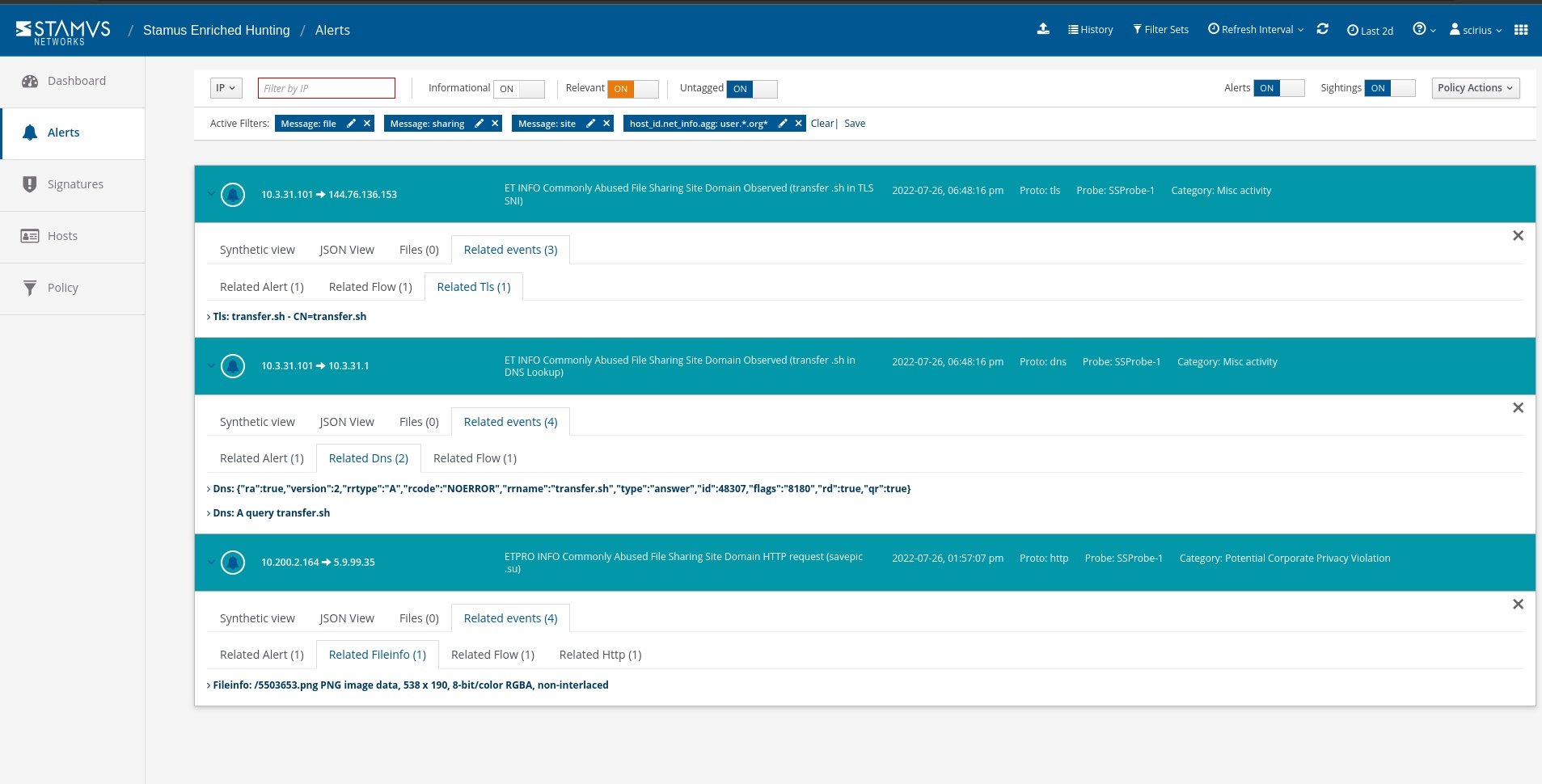
From here, we can select a specific event and further review the supplemented network protocol and connection logs evidence. This information not only provides context for our current hunt, but also allows us to use the available metadata to create other hunting filters for future use.
Security analysts can use any piece of metadata to create simple or complex filters for things like wildcarding, negation, or inclusion. You can even include multiple fields for fast drill down capabilities. All domains, TLS SNI, IP addresses, HTTP hosts, and more can easily be checked with an external threat intelligence provider such as Virus Total.
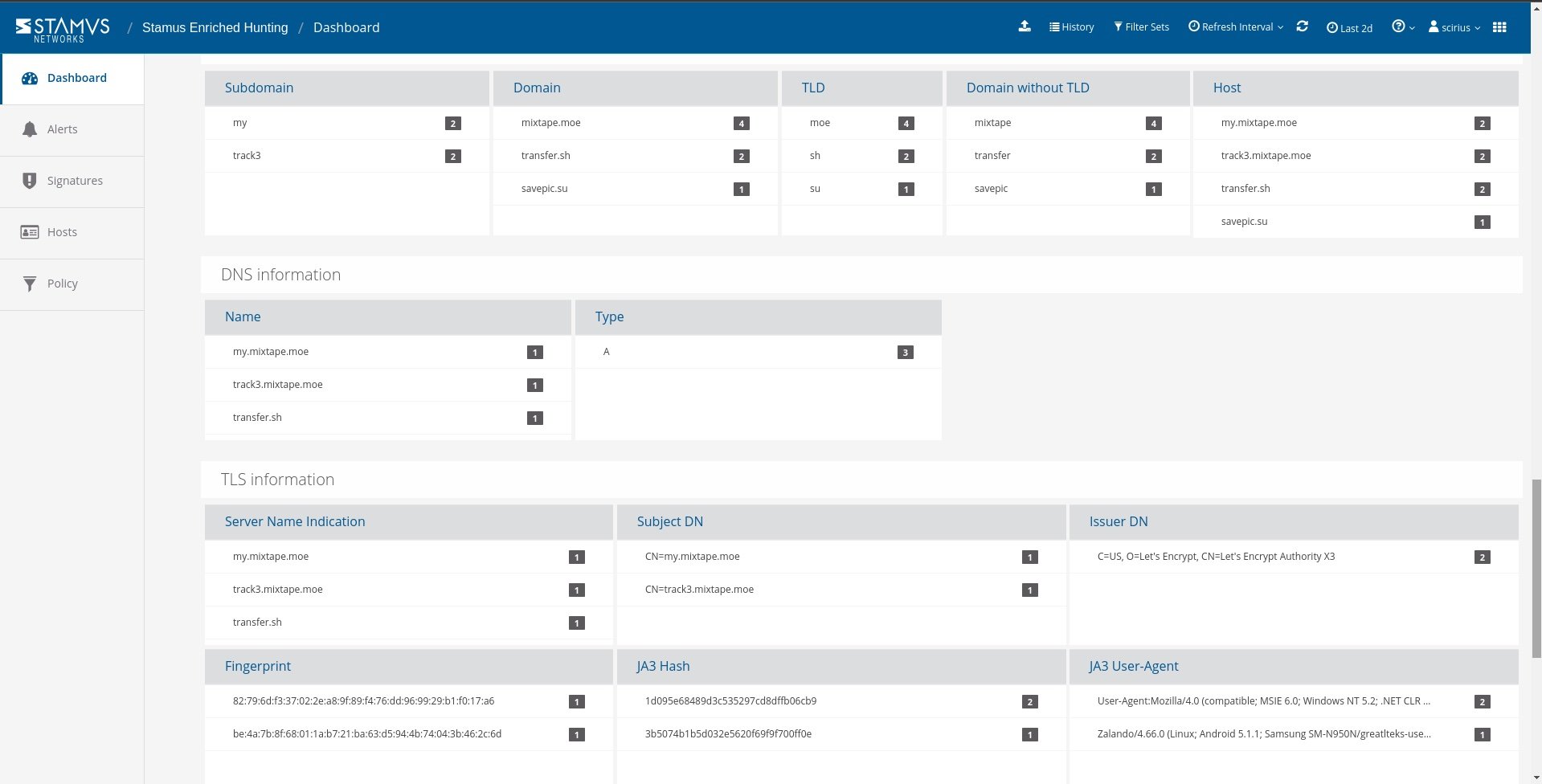
It’s important to know who the client and offending hosts are and if there is additional information about those seen on the network. Specifically, we need to see which services are running on the offender’s host.
To do this, we can use Host Insights - a very powerful feature included with the Stamus Security Platform. Host Insights tracks over 60 security-related network transactions and communication attributes of a host. This provides a single place to view many aspects of the network activity relative to a given host, such as network services, users, or TLS fingerprinting forensic evidence.
We can click the “Hosts” tab on the left hand side panel and be transferred from the actual events logs to the Host Insights screen. In this example we can see an unusual user agent with a name that starts with “cpp-httplib…”
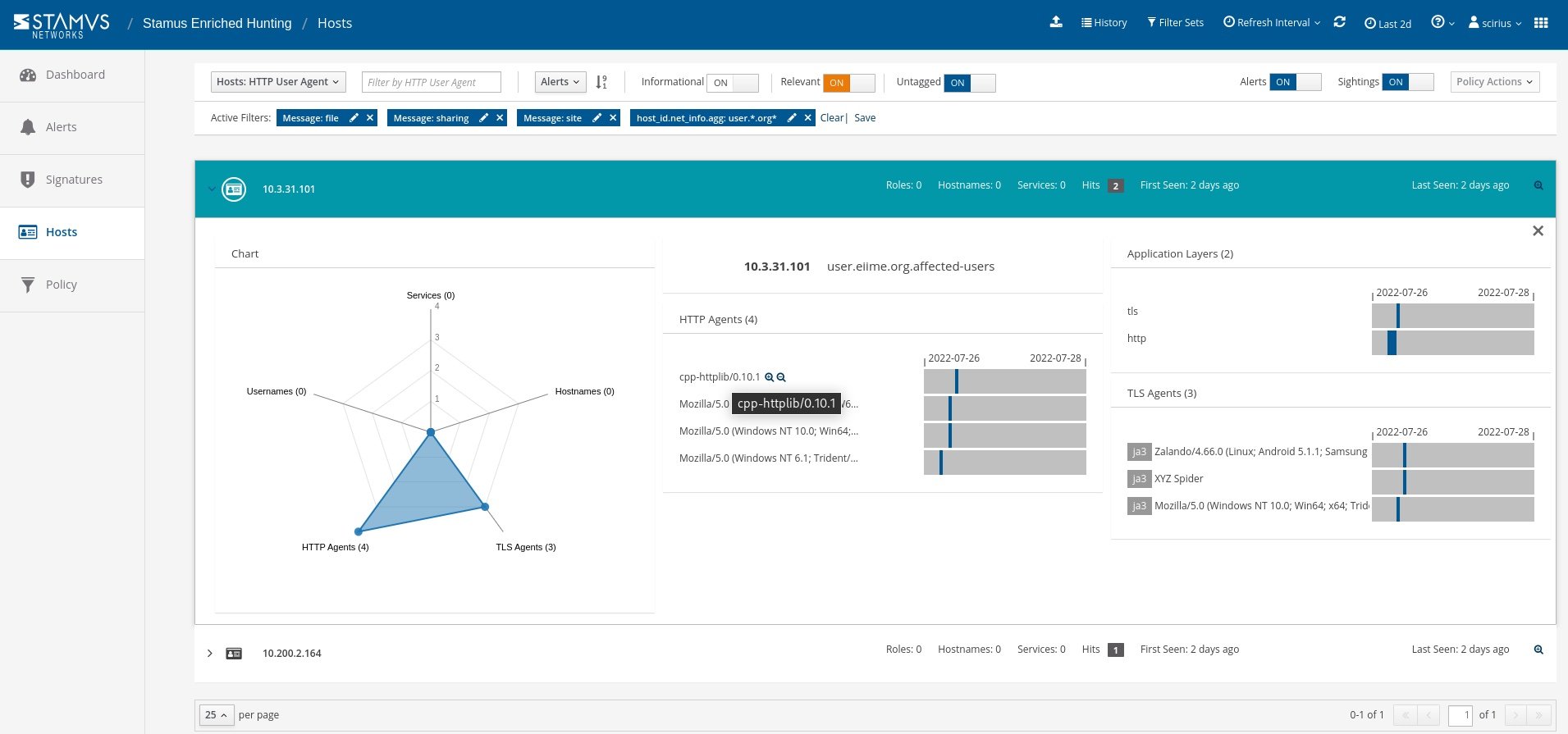
With a single click we can see if that user agent is seen anywhere else on the network.
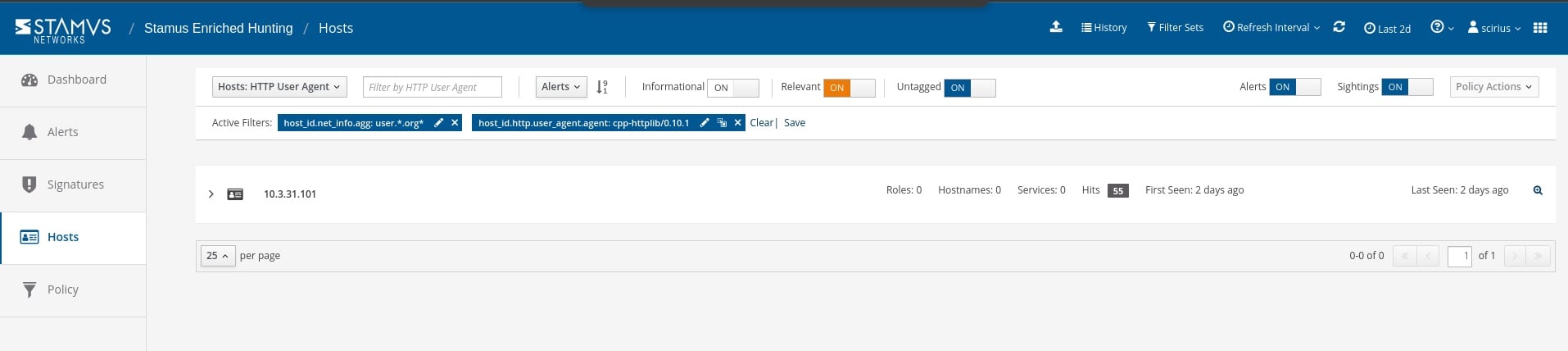
We also want to wildcard the search term to see if anything else comes up.
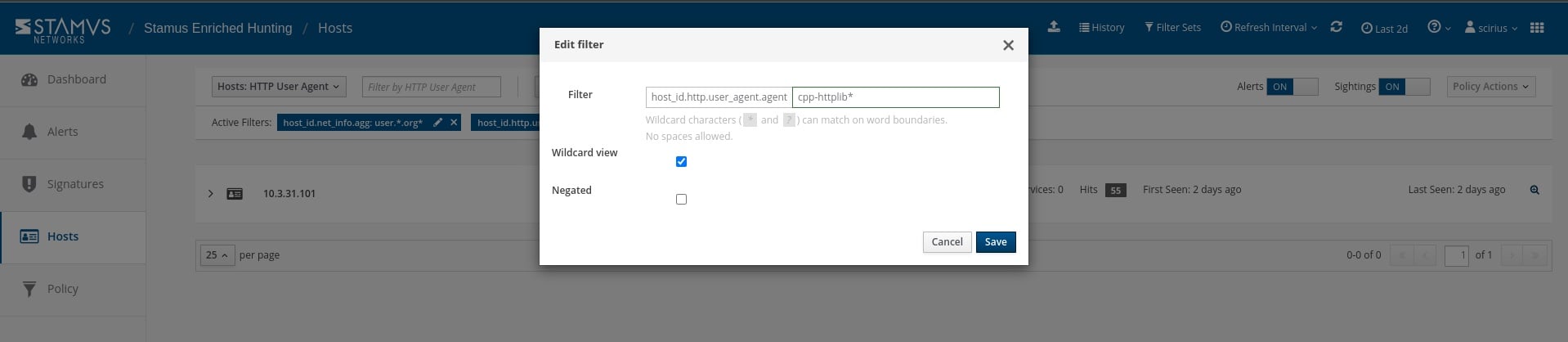
Armed with the above information and evidence, a threat hunter has enough information to generate an Incident Response ticket.
However, there are still two tasks left to complete:
- 1 - We do not want to have to repeat this exact same process again in the future, so we need to set up classification and auto-escalation for future occurrences.
2 - If anything like this has happened before, we want it to be found and escalated with all the associated evidence - all based on historical data.
Classification
In order to streamline the event review/triage process in the future, an experienced analyst can choose to tag/classify the events associated with this filter By doing so, SSP will tag future events that match the filter criteria as “relevant” or “informational,” depending upon the analyst’s selection. These tags can be used to automate event review/triage and make it easier for a less-experienced analyst to identify events that are relevant for manual review.
To do so, the analyst selects the Tag option from the Policy Action menu on the right hand side menu. This action will cause SSP to insert a tag into each event record as shown below:
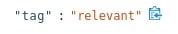 This allows the analyst to easily filter out or search for them in any SIEM (Chronicle, Splunk, Elasticsearch, etc) or data lake using that tag.
This allows the analyst to easily filter out or search for them in any SIEM (Chronicle, Splunk, Elasticsearch, etc) or data lake using that tag.
It also allows for easy filtering out of those events in the Stamus Enriched Hunting GUI by switching to “relevant” only classified events.
Escalation and Automation of this Threat Hunt
To set up an automation which causes SSP to escalate past and future occurrences, we can create a Declaration of Compromise (DoC) event from the Policy Actions drop down menu on the right hand side panel in the Stamus Enriched Hunting Interface.
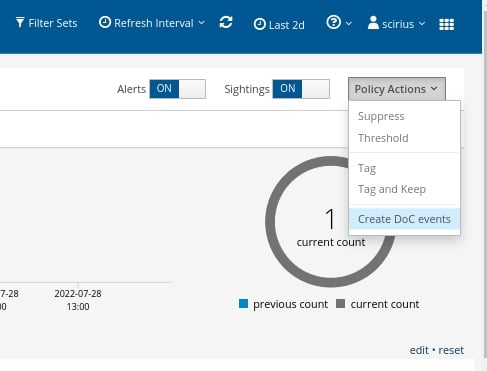
The next step is to add some explanation about the type of threat. This also gives us a chance to provide informational context and helps convey knowledge to colleagues.
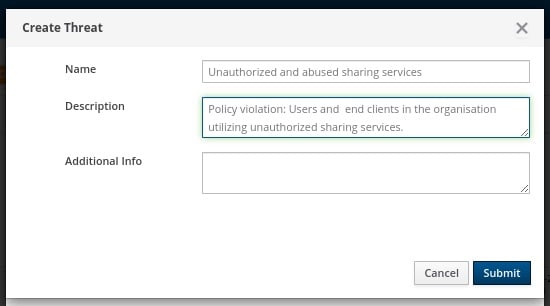
Select options to generate events from historical data and generate Webhook notifications.
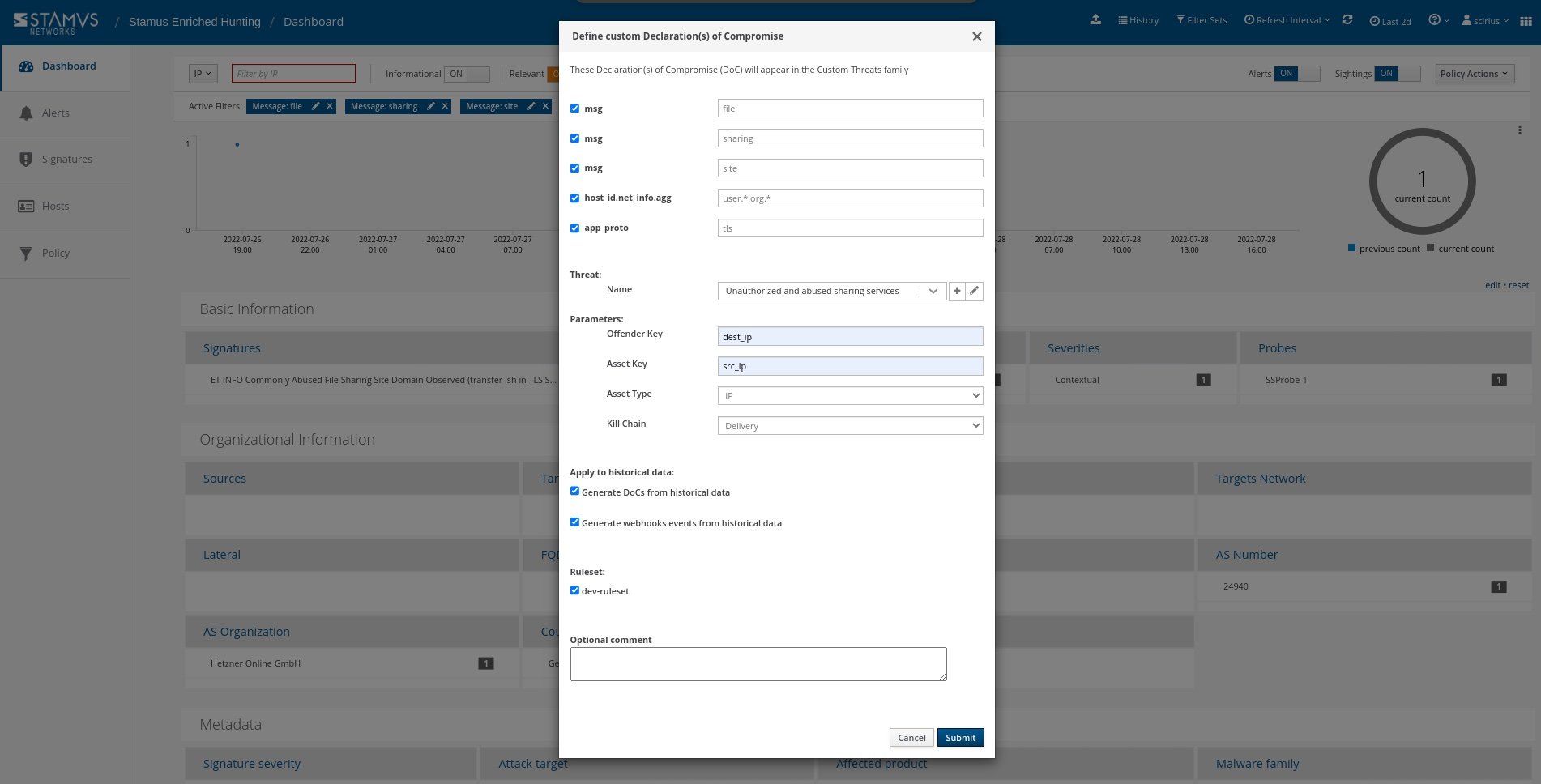
Just like that, the hunt and all related activities are complete. Any past or future generated events from that automation will then be further auto-classified and escalated to the desired response process - via SOAR playbook, chat notification, or incident response ticket.
Conclusion
The post-hunt activities completed in this example are just the tip of the iceberg when it comes to the automation and escalation capabilities of Stamus Security Platform (SSP). To learn more about these features and how to implement them, read our article titled “After the Hunt”.
To learn more about Network Detection and Response (NDR) from Stamus Networks and see the enriched hunting interface for yourself, click the button below and schedule a live demo.







