An analysis by political analyst Tarık Özcan published this week in Meer captures something those...
This blog describes the steps Stamus Networks customers may take to determine if any of your...
The cybersecurity industry has a dirty secret: vendor lock-in isn't a bug, it's a feature. For...
If you’ve been following our recent work at Stamus Networks, you’ve likely seen my demonstrations...
Budgets may not be shrinking, but they certainly aren’t keeping up with the complexity and scale of...
Cloud adoption continues to grow, but so do the challenges security teams face in detecting and...
Suricata Language Server 1.3.0 is now available and it surfs on the concept of magic comment...
When CISA released version 2.0 of its Cross-Sector Cybersecurity Performance Goals last week, the...
Alert fatigue - the condition that arises from being overwhelmed by millions of vague alerts and...
Security teams are under tremendous pressure. Cloud complexity, alert fatigue, staffing shortages,...
Modern security operations face an impossible challenge: the volume and complexity of threats have...
We are pleased to share the news that Stamus has released Clear NDR® Enterprise (formerly known as...
Security operations centers (SOCs) are drowning in a deluge of alerts. Millions of network events...
While detecting malicious attacks is critical for preventing a serious security incident, ensuring...
Security teams are often overwhelmed by a flood of alerts, leading to alert fatigue and missed...
Modern IT infrastructure, whether traditional or hybrid, faces persistent challenges: staff...
One of the significant advantages of Clear NDR’s multi-layered detection is its ability to identify...
Suricata Language Server (SLS) has been available for more than 3 years, and it has always been...
The example outlined in this blog article demonstrates Clear NDR’s value in delivering visibility...
The following example is of an unstructured hunt technique—an investigation based on an idea or...
One of the key strengths of Clear NDRTM is its AI-based TLS beacon detection, which, when combined...
At Stamus Networks, we have always been driven by a commitment to openness, transparency, and...
In this series of articles, we explore a set of use cases that we have encountered in real-world...
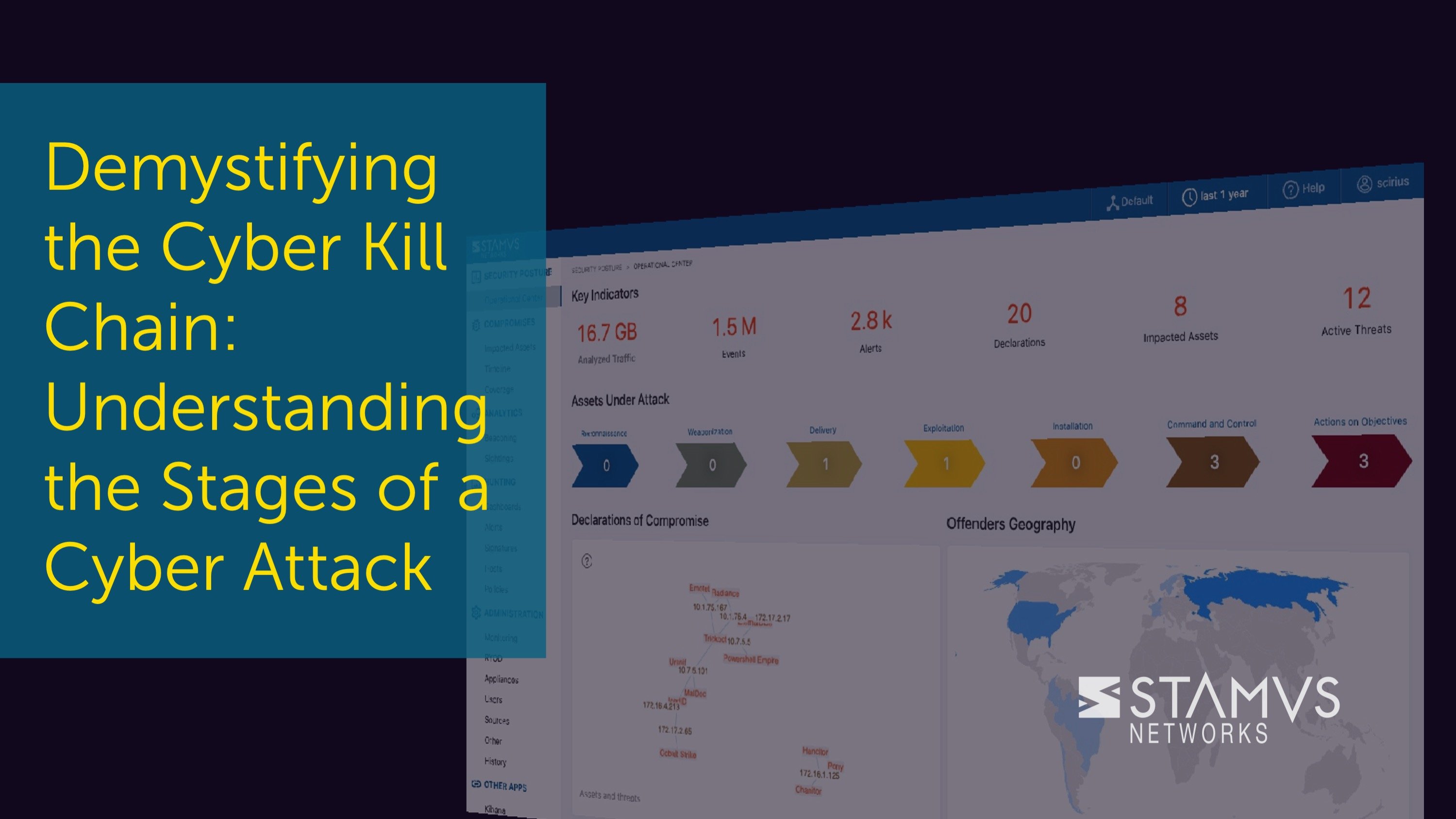
The cyber kill chain is a widely-used framework for tracking the stages of a cyber attack on an...
Clear NDRTM users can now integrate the Malware Information Sharing Platform (MISP) to supplement...
In a recent conversation, one of our customers shared their concerns about the use of ChatGPT in...
This blog describes the steps Stamus Networks customers may take to determine if any of your...
This week’s threat detection blog dives deeper into a common type of malware, remote access trojans...
This week’s guided threat hunting blog focuses on a specific policy violation - the use of...
Phishing is commonly regarded as the most common and effective way attackers can gain access into a...
In this article, we will review one of the most important and critical phases on the cyber kill...
One of the first network-related indications of a botnet or peer-to-peer (P2P) malware infection is...
In this article I want to highlight one of the tactics used by malicious actors to move within your...
In the first article of this series -- Threats! What Threats? -- I mentioned that my colleague,...
In the previous article of the “Feature Spotlight” series, we discussed how to pivot from IDS alert...












.jpg)
.jpg)
















.jpg)




