Threat hunting is a common practice for many mature security organizations, but it can be time consuming. A lack of context and automation are leading contributors to this.
First, analysts waste precious time after initially identifying the source of a potential threat or policy violation trying to contextualize its origin and impact on the organization. It takes too much time, for example, to determine if it was associated with an individual user, a server, someone in the marketing department, or on the guest wifi, etc.
Then, once an issue has been uncovered the first time, how does an analyst confirm the threat and then set up a process to automatically notify the team when that type of activity occurs in the future?
Stamus Networks has developed a very simple system to bring organizational context to threat hunters, thereby accelerating their time to identify and validate threats. By using network definitions configured by the security teams, Stamus Security Platform automatically generates metadata that provides vital information directly to the analyst without their needing to pivot to outside systems like IP address management (IPAM) software or hard copy network diagrams and spreadsheets.
While a simple concept, this form of organizational context is an enrichment provided by the Stamus Security Platform (SSP) to help users perform more efficient threat hunting and turn findings into automated detections for future occurrences. We included these features in SSP based on real-world experiences our team has gathered in the field and from our enterprise security customers.
In this article, we will explain what we mean by “network definitions” and “organizational context” and share some examples of how these can help analysts improve their threat hunting and escalation processes.
What are Network Definitions and how do they deliver Organizational Context?
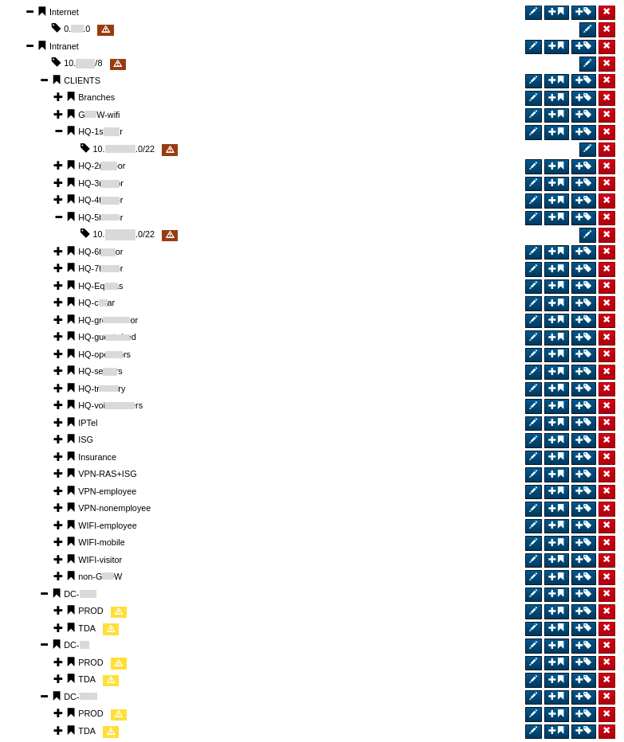
When users set-up the Stamus Security Platform (SSP), we encourage them to configure network definitions. This tells SSP how the organization refers to their clients, servers, critical infrastructure, and applications based on IP addresses. By doing so, the administrator is literally defining the location and other important characteristics of endpoints on their network.
For example, one group of IP addresses might be designated to “3rd floor - accounting department” whereas another might be “basement - server room 1”. Network definitions can be created manually or imported as standard JSON - such as Service Now, Device42, router/switch network descriptions, IT management systems, etc – and then be updated continuously, as needed.
This process may take some time, but the time spent during initial set-up will be worth it for the time savings later during a hunt, while performing forensics, doing incident response, or when creating custom Declarations of Compromise™ (DoCs).
Organizational context is the enriched metadata for those defined IP address spaces. Once network definitions are configured, SSP begins to enrich any and all generated logs with the data. That data can be accessed, searched, and viewed at any time. This data is unique to the network architecture, and when viewed within the context of the organization can provide rapid insights into network activity that would otherwise require a pivot into another tool or document. This is valuable not only for threat hunting, but also for creating hyper-focused escalations on specific threat types, thus minimizing noise and potential false positives.
How to add new network definitions
To add new network definitions, follow this process:
- 1. Go to “Administration”
- 2. Select “Appliances”
- 3. Select “Network Definitions” from the left hand side panel
- 4. Add, edit, or group addresses as needed
*Please note: These steps can be automated via a REST-API
Threat Hunting with Organizational Context
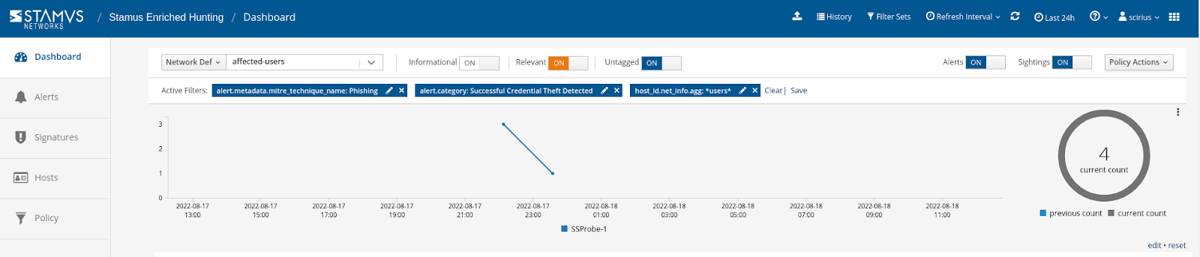
When conducting a threat hunt using one of SSPs guided threat hunting filters, the user can filter results based on specific organizational context. For example, they could initiate a hunt for all potential phishing activity, which might return dozens of alerts from IP addresses across the organization. If they wish to narrow the hunt to concentrate only on potential phishing activity targeting upper level management or the accounting department, they may add a filter to see just that, returning only those specific events that require further investigation.
The screenshot below shows a set of filters for this type of activity from the selected user group:
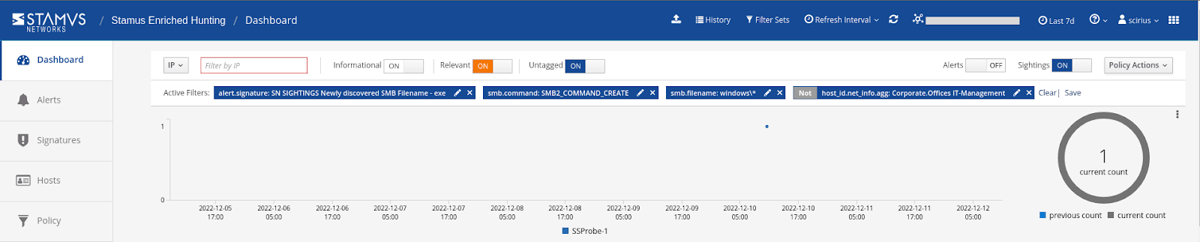
Alternatively, organizational context can be used to start a hunt. All organizational context is included in log records for the defined IP addresses. So if the user has a hypothesis that there might be suspicious lateral executable transfers originating from clients located in their corporate office, they can filter accordingly to view those logs. They can then launch a hunt from there to investigate that data.
This screenshot shows only one alert is returned when data is filtered to see only events originating from outside IT management department at the corporate office:
Simply put, network definitions allow SSP to embed organizational context into the metadata for event records. This lets users create a filter to search through all events using familiar names instead of IP addresses.
Creating Custom Declarations of Compromise with Organizational Context
While it is helpful to use this organizational context to create starting points for a hunt, the true value comes from creating automated escalations for future events.
Using Stamus Security Platform, users can classify, automate, and escalate vast amounts of event data, alerts, and contextual metadata. In many cases, hunting is driven by a hypothesis and conducted with the specifics of their organization in mind. These hypotheses can then be formulated into an SSP automation, and the results can be classified or automatically escalated.
The ability to turn a hypothesis into an automated hunt using organizational context allows security practitioners to reduce their time to act, respond, and make decisions. These hypotheses — enriched by organizational context — can also be used to create custom DoC events.
Declarations of Compromise™ (DoCs) are the highest-confidence assertion SSP provides, highlighting a specific threat and the asset(s) it is impacting. A DoC event includes a detailed timeline of the threat activity as well as relevant supporting evidence and context. These DoC events can notify the analyst using a third party tool, such as chat or email via webhooks, and may be used to trigger an automated response via EDR, firewall, SOAR, SIEM, or XDR
By creating a DoC based on network definitions and organizational context, like FQDN or usernames, users gain the ability to customize the detections they want to have automatically escalated. For example, a user could create a custom DoC that would trigger when one of the employees from their sales team violates file transfer policy. That DoC would not only include the details of the event, but also all the corresponding logs for the defined addresses. An organization could have any number of reasons to want custom DoCs for these types of events, and it ultimately comes down to which kind of activity the analyst feels is worthy of an automatic escalation.
To create a custom DoC based on a specific organizational context, the user just needs to first create a filter including that organizational context, then select the option from the Policy Actions drop down menu on the right hand side panel in the Stamus Enriched Hunting interface.
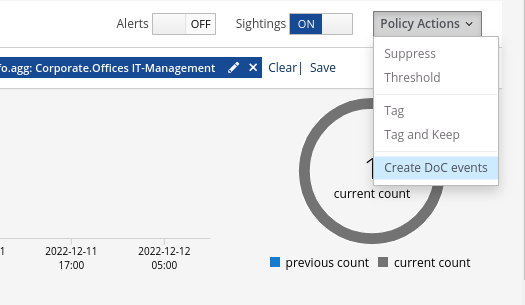
Then the user adds some information describing the type of threat, defines some parameters, and indicates whether or not they want to retrospectively generate DoC events from historical data.
From an escalation and automation perspective, organizational context lets practitioners create more focused events based on user friendly attributes rather than IP addresses, giving the user more freedom in the types of events they look for.
Organizational Context is vital for Network Detection and Response (NDR)
When evaluating NDR options, organizations should be considering the level of customizability a system provides them. This is not just about the extensibility of the platform integrating with their existing security stack, but also the ability to make changes within the platform itself to fit the specific requirements of the organization. Including network definitions and the resulting organizational context is a key component of this, as these features give security teams greater visibility into the network and streamlines threat hunting and event escalations.
Stamus Security Platform (SSP) is a broad-spectrum, open, and extensible network-based threat detection and response system (NDR). It gives organizations the ability to create their own network definitions and view organizational context that can positively impact the efficacy of threat hunting activities.
To learn more about threat hunting with the Stamus Security Platform, read the blog article titled, “Introduction to Guided Threat Hunting”.






