In the first article of this series –Threats! What Threats? – I mentioned that my colleague, Steve Patton, thought we at Stamus Networks weren’t doing enough to explain what we mean when we say “threats.” His reasoning was – we talk a lot about threats, but we never really explain what we mean.
So, in this article we dig deeper into one of the most insidious threats facing organizations around the world - ransomware. We define ransomware and review how Stamus Security Platform can help users detect this threat in its early stages before it inflicts significant damage.
What is ransomware and why is it bad?
Ransomware is malware designed to damage or disable the IT operations of a user or organization. Files and data can be encrypted preventing access, or files containing sensitive, proprietary or personal information can be published to the public unless a ransom payment is made. By encrypting these files and demanding a ransom payment for the decryption key, or publishing a tiny sample of the stolen data as proof that access has been made, this malware often places organizations in a position where paying the ransom may seem like the easiest and least-costly way to regain access to and control of their data.
And often the threat actors have stolen and are in possession of the organization’s sensitive data. This means that paying the initial ransom to decrypt the systems may not be enough. The perpetrator may still enter a second round of extortion in which they demand payment to not release or sell the data.
Finally, the international legal system and law enforcement officials provide little clarity – and often contradictory guidance – on how to proceed.
This puts organizations facing a ransomware demand in an incredibly difficult position.
Detecting Ransomware Before it’s Too Late
This is why organizations wish to detect the ransomware attack before its damage is done.
Ransomware – like most malware installations – follows a typical progression, in many cases taking control of the key assets in the network then triggering payload encryption and potentially exfiltration of data.
Unfortunately for many victims, detecting the ransomware occurs too late, when they receive a message on a display or in an email that indicates their files have been encrypted or their data has been stolen.
The Stamus Security Platform has a number of constantly-updated detection mechanisms which can alert the operator when ransomware is in progress infiltrating the network, trying to gain access to key assets, communicating back to a command and control server, or moving laterally within the infected network. The key is to detect these stages of its progression before the data theft or encryption takes place.

A challenge with traditional intrusion detection (IDS) and network security monitoring systems (NSM) is the volume of alerts that can swamp a user trying to prioritize the most important and impacting events that indicate an imminent attack. Next, the analyst must sort out the false positives from true positives, an exhaustive effort that often involves pivoting among multiple systems and user interfaces. With potentially 100’s of thousands of alerts each day from network traffic, and only a small handful indicating threats leading to installation of ransomware, the attack could be missed.
This is where the broad spectrum detection in the Stamus Security Platform with its prioritization and detection algorithms makes the job of the defender easier by removing the background noise and only promoting the most serious and imminent threats to the cyber kill chain. We call these Declarations of Compromise™, ultra-high-confidence events associated with a given asset with threats tracked along the cyber kill chain and supported by extensive evidence.
Our threat research team at StamusLabs is constantly adding to and refining the ransomware threat coverage through behavioral anomaly, signature, and machine learning -based detection. More important than explicit ransomware coverage, Stamus Security Platform includes detection coverage for numerous precursor threats along with tools, tactics and procedures (TTPs), including downloaders, data theft, lateral movement, command and control communications, and backdoors.
To get an idea of the coverage areas, see screenshot of Stamus Security Platform threat coverage page below.
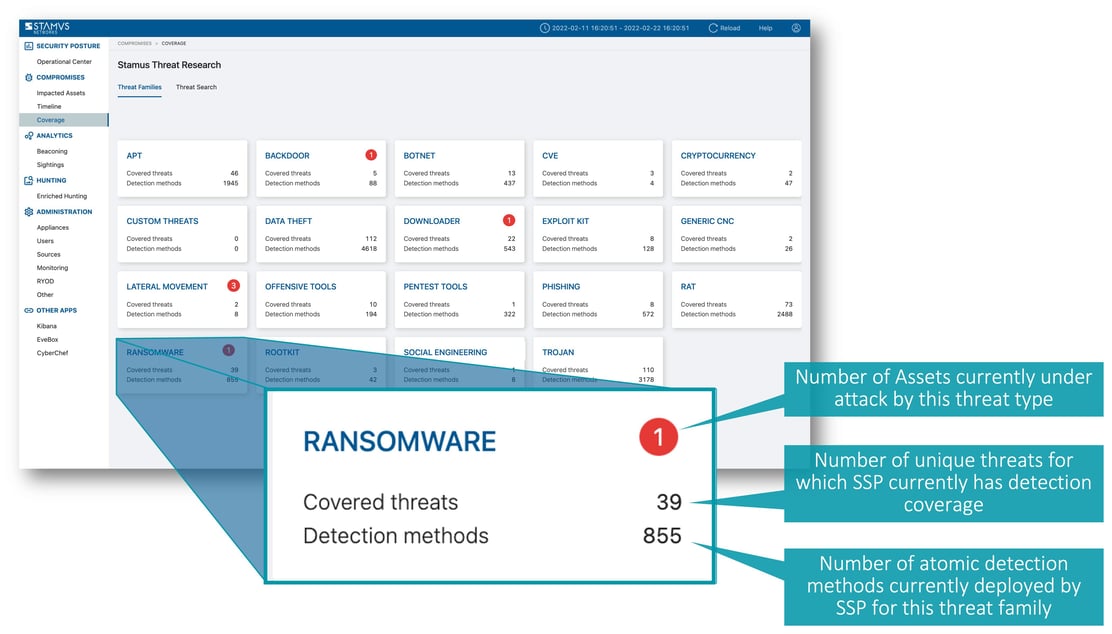
In addition to explicit ransomware detections shown in the screenshot above, Stamus Security Platform includes detection mechanisms and methods for other actors, tools and techniques used as part of a ransomware attack. These include mechanisms to detect downloaders, offensive tools, trojans, remote access trojans, lateral movement, and advanced persistent threats, and others. All of these may be used in the early stages of a ransomware attack.
This detection coverage is updated and pushed to the users’ Stamus Security Platform every single day.
More information on Stamus Security Platform
So, next time my colleague Steve asks “why don’t we ever mention the types of threats we’re talking about?” I can thank him and point him to this blog series.
If you’d like to get a live demonstration of Stamus Security Platform or discuss how it might help you detect early stages of and respond to ransomware threats in your network, please click on the button below to request a demo.







