This week in our threat detection blog we are mixing things up and discussing an important Clear NDRTM coverage area that isn’t actually a threat - penetration testing and offensive tools. Your defensive security team will want to detect these tools operating on your network in order to demonstrate their visibility into all network activity, whether it is malicious or not. In this article we will discuss what penetration testing is, what offensive tools are used for, why it is important to detect them, and how Clear NDR can help.
At Stamus Networks we talk about threats often, but we realized that we hadn’t spent much time highlighting what threats we were talking about. This series — Threats! What Threats? — seeks to solve that problem.
What is Penetration Testing?
Penetration testing, otherwise known as pen testing, is a simulated cyber attack used to check a system or network for vulnerabilities. The insights gathered from these tests are used to inform new policies and implement changes to the security structure of the system.
Some organizations have in-house employees that conduct pen tests, and others will hire outside firms to run surprise tests. This not only checks the system for any weaknesses, but also helps assess the security team's response to potential threats. That is why it is important for an organization’s network security tool to be able to detect not only real, malicious threats, but also simulated ones.
There are tools, like Cobalt Strike, which function as a commercially-available, full-featured suite of adversary simulation tools. These platforms emulate long-term embedded APTs, and include various features like the ability to change its indicators to look like different types of malware.
Other offensive tools, like FireEye, Mimikatz, and Koadic, simulate different types of attacks a network might face. These tools are based on the same technology and strategies used by attackers, and security teams can use them to conduct pen testing. By seeing which tools are effective, they can locate holes in their systems capabilities and make adjustments as needed.
While it is clearly important to detect real threats, it is also helpful for the defender’s systems to detect penetration testing activities. The security team should have the highest level of visibility into network activity, so catching the presence of offensive tools or pen testing software helps demonstrate that they are capable of locating these types of threats in a real attack. By design, these tools are designed to be sneaky, and in some cases they will target known weaknesses in the network. Catching these simulated attacks and then tracing their activity throughout the network can shed light on which areas of the system’s security are lacking.
How does Clear NDR Detect Pen Testing?
Clear NDR can help security teams identify pen testing in three primary ways:
Declarations of Compromise™
Clear NDR can detect millions of alerts within a given timeframe, but no security analyst has the time to look through each alert to find the most serious, imminent threats. To take away the guesswork, Clear NDR automatically escalates those high-value, potentially dangerous threats into a Declaration of Compromise™ (DoC). These events are the most high-confidence assertion that the system provides.
A DoC highlights a single, specific threat and the asset(s) it is impacting. It then includes a detailed timeline of the threat’s activity on the network with included context surrounding the impacted asset(s). These events are automatically escalated and the analyst can be notified via webhook in a variety of applications - SOAR, SIEM, Discord, web chat, etc.
Clear NDR includes multiple coverages for pen testing platforms and other offensive tools, as well as additional third-party resources to educate security teams on those tools. The Stamus Labs research team continually adds new threat coverages and updates users daily.
The screenshot below illustrates a sampling of Clear NDR coverage for general offensive tools
Guided Threat Hunting
Declarations of Compromise escalate the highest priority alert events, but what about the other alerts? An organization might want to spend some time proactively searching through those events in order to find specific threat types. When this is the case, they can use the Stamus Enriched Hunting Interface. Included in this interface are over 100 guided threat hunting filters that enable a user to search for hyper-focused threat types, anomalous behaviors, and suspicious activity.
This tool can be used to search for various activities and techniques that are frequently used by pen testers. A user can hunt for vulnerable software, policy violations, MITRE techniques, and more in just a few minutes. These filters narrow down alert events and then provide in-depth context with additional capabilities to classify, automate, and escalate processes for future events.
For a more thorough introduction into the Stamus enriched hunting face, read the “Introduction to Guided Threat Hunting” on the Stamus Networks Blog.
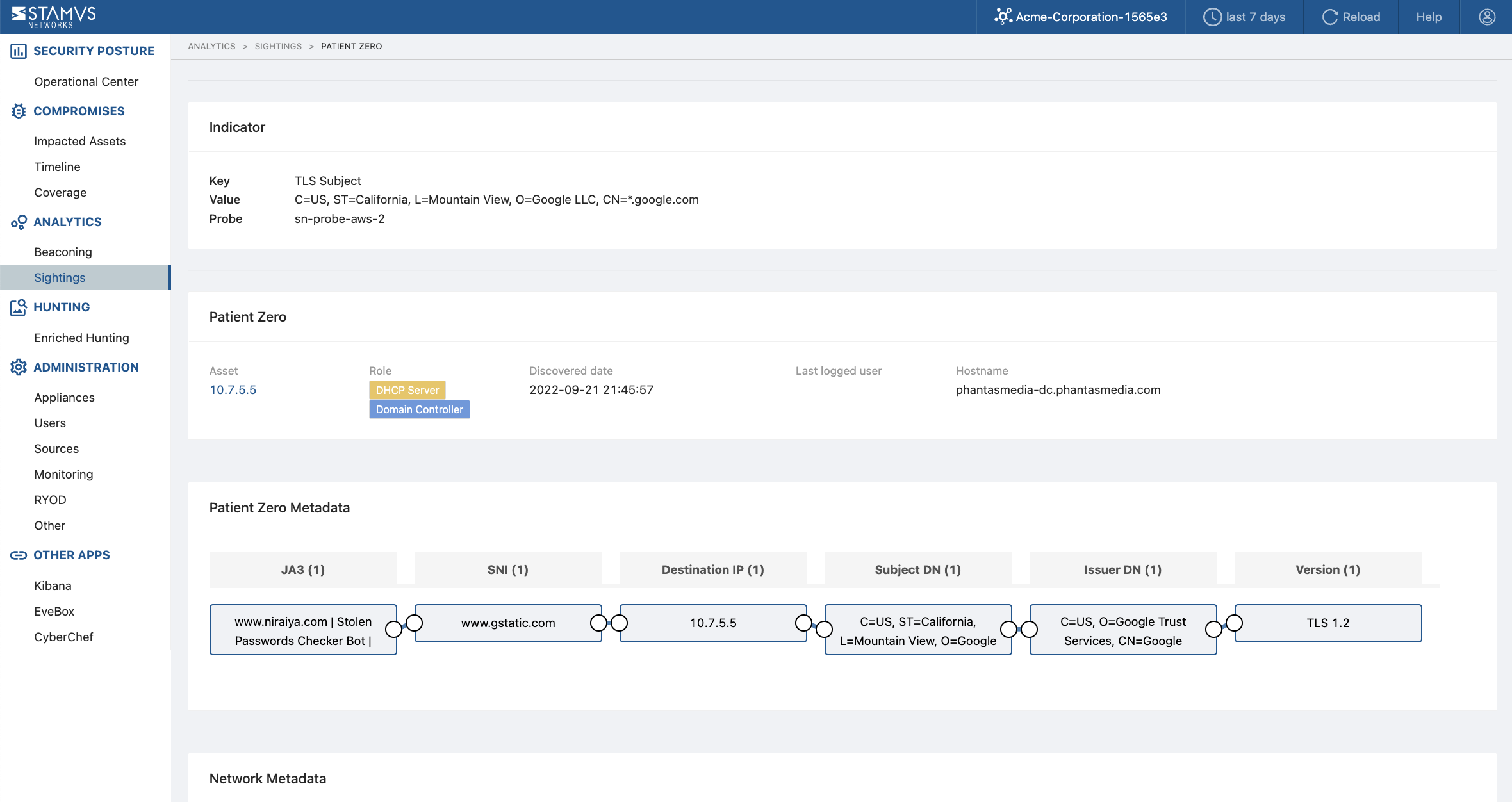
Encrypted Connections and HTTP Transfers via Sightings
Previously unseen encrypted connections and HTTP transfers can be indicative of pen testing activities, so spotting these communications can lead to the discovery of pen testing software or offensive tool usage within an organization. Clear NDR includes a feature called “Sightings”, which uses detection algorithms to identify the occurrence of never-before-seen artifacts from critical infrastructure.
Sightings can include connections based on discovered Host roles - domain controllers, DHCP servers, proxies, printers, etc. This gives the user a quick view of potentially suspicious activity like new, encrypted connections to a pen testing C2 server or HTTP transfers from the client to an offensive tool server.
The screenshot below shows the results of the sightings detections.
More information on Clear NDR
Penetration testing, and the offensive tools associated with it, is incredibly valuable to determine weaknesses in an organization’s security protocols. Regardless of whether the offensive tools are able to infect a system or if they are caught in the act, a successful pen test is one that helps determine areas of improvement.
If you would like to see a live demonstration of how Clear NDR detects crypto mining malware or want to discuss how else it could help you detect and respond to threats in your network, please click on the button below to request a demo.







