We talk often about “threats” and “threat detection” in our marketing materials and in discussions with our customers.
But my colleague, Steve Patton recently asked “why don’t we ever mention the types of threats we’re talking about?”
Well, that’s a great question, Steve !
Network Security for Threat Detection & Response
As a reminder, at Stamus Networks we are a provider of network-based threat detection and response solutions. The reason we focus on the network is that it holds the ground truth for an enterprise’s security posture and does not require complex endpoint agents in order to be effective.
Even as more organizations shift to cloud-based resources, encrypted transmission, and remote workforces, nearly all cyber threats generate communications that can be observed on the network. And in many BYOD environments and with the proliferation of IoT devices, you can’t rely on endpoint detection to uncover threats.
So, what threats are we talking about?
Users of our Stamus Security Platform (SSP) will be familiar with the list of threat coverage displayed on this SSP threat "coverage" screen:
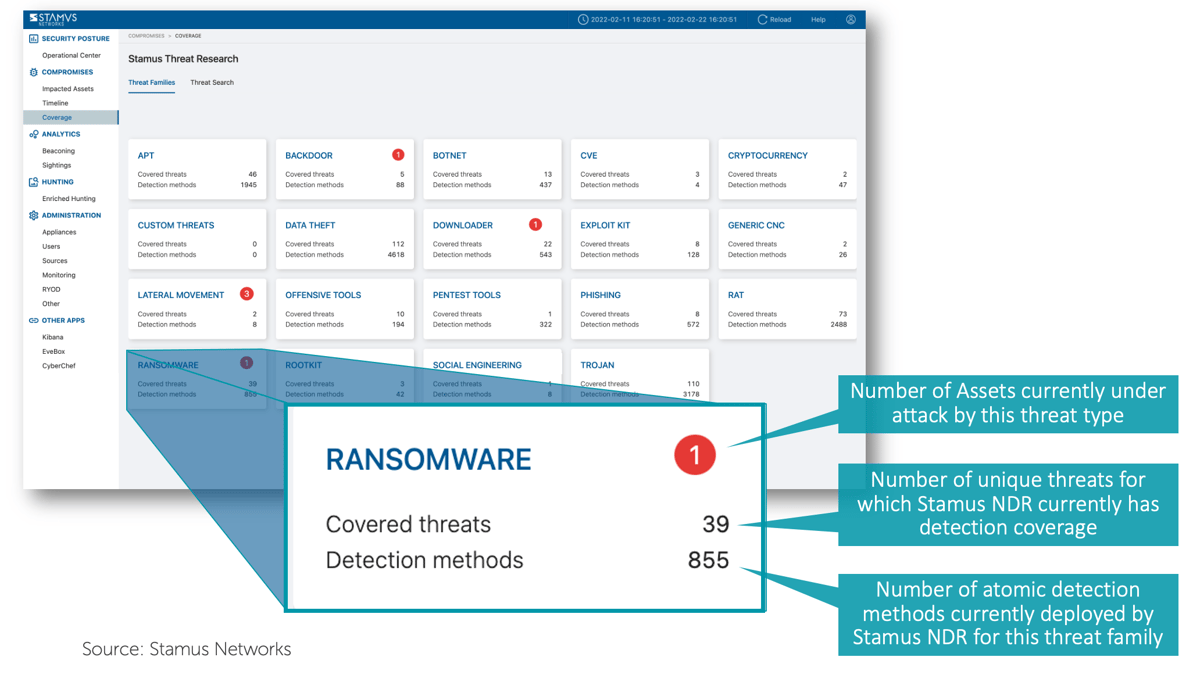
This screen captures the key threat families we’re talking about.
And there are even more types of threats that can be detected by using our guided hunting interface to create a custom threat detection rule - which would appear on the above screen under “Custom Threats.”
In this article, I’d like to highlight a reasonably short list of 18.
Here's my short list:
- Malware (see blog here >>)
- Ransomware (see blog here >>)
- Lateral movement (see blog here >>)
- Shadow IT (see blog here >>)
- Malware beacons (see blog here >>)
- Command and control communications (see blog here >>)
- Crypto-mining
- Policy violations
- Exploit kits
- Botnets
- Data exfiltration
- Penetration tests
- Remote access trojans
- Rootkits
- Social engineering
- Offensive tools
- Phishing
Here's a short video I hope makes the point in 17 seconds.
In subsequent articles, we will describe what we mean by each of the above threat categories and explain what sorts of things we can uncover with the Stamus Security Platform.
Does this help, Steve?
So, next time my colleague Steve asks “why don’t we ever mention the types of threats we’re talking about?” I can thank him and point him to this blog.
If you’d like to get a live demonstration of the Stamus Security Platform or discuss how it might help you detect and respond to threats in your network, please click on the button below to request a demo.







