Budgets may not be shrinking, but they certainly aren’t keeping up with the complexity and scale of...
D. Mark Durrett

Recent Posts
Cloud adoption continues to grow, but so do the challenges security teams face in detecting and...
When CISA released version 2.0 of its Cross-Sector Cybersecurity Performance Goals last week, the...
Alert fatigue - the condition that arises from being overwhelmed by millions of vague alerts and...
Security teams are under tremendous pressure. Cloud complexity, alert fatigue, staffing shortages,...
In today's complex cybersecurity landscape, Network Detection and Response (NDR) solutions have...
In today's rapidly evolving threat landscape, network detection and response (NDR) solutions play a...
In recent years, AI-based anomaly detection has become a cornerstone of network security marketing....
In today's complex threat landscape, cybersecurity teams face an overwhelming challenge: detecting...
For security teams using Darktrace and similar anomaly-based NDR solutions, the scenario is all too...
In recent years, we've observed a notable trend: sophisticated security operations centers (SOCs)...
This week’s threat detection blog dives deeper into a common type of malware, remote access trojans...
In this week’s threat detection blog, we will be reviewing a financially-motivated threat that is...
This week we are taking a closer look at Shadow IT, which is the use of information technology by...
Phishing is commonly regarded as the most common and effective way attackers can gain access into a...
In this article, we will review one of the most important and critical phases on the cyber kill...
One of the first network-related indications of a botnet or peer-to-peer (P2P) malware infection is...
In this article I want to highlight one of the tactics used by malicious actors to move within your...
In the first article of this series -- Threats! What Threats? -- I mentioned that my colleague,...
The world of cybersecurity is rapidly changing and enterprises have to quickly adapt in order to...
On 25 March 2022, my colleague Ed Mohr and I will be attending the Cyber Security Summit in...
In the first article of this series –Threats! What Threats? – I mentioned that my colleague, Steve...
We talk often about “threats” and “threat detection” in our marketing materials and in discussions...
Security monitoring is perhaps the least discussed element of a Zero Trust strategy
Over the past...
So, you are considering migrating your legacy or aging intrusion detection and prevention system...
So, you are considering migrating your legacy or aging intrusion detection and prevention system...
Regular readers of this blog and friends of Stamus Networks will know that we are very closely...
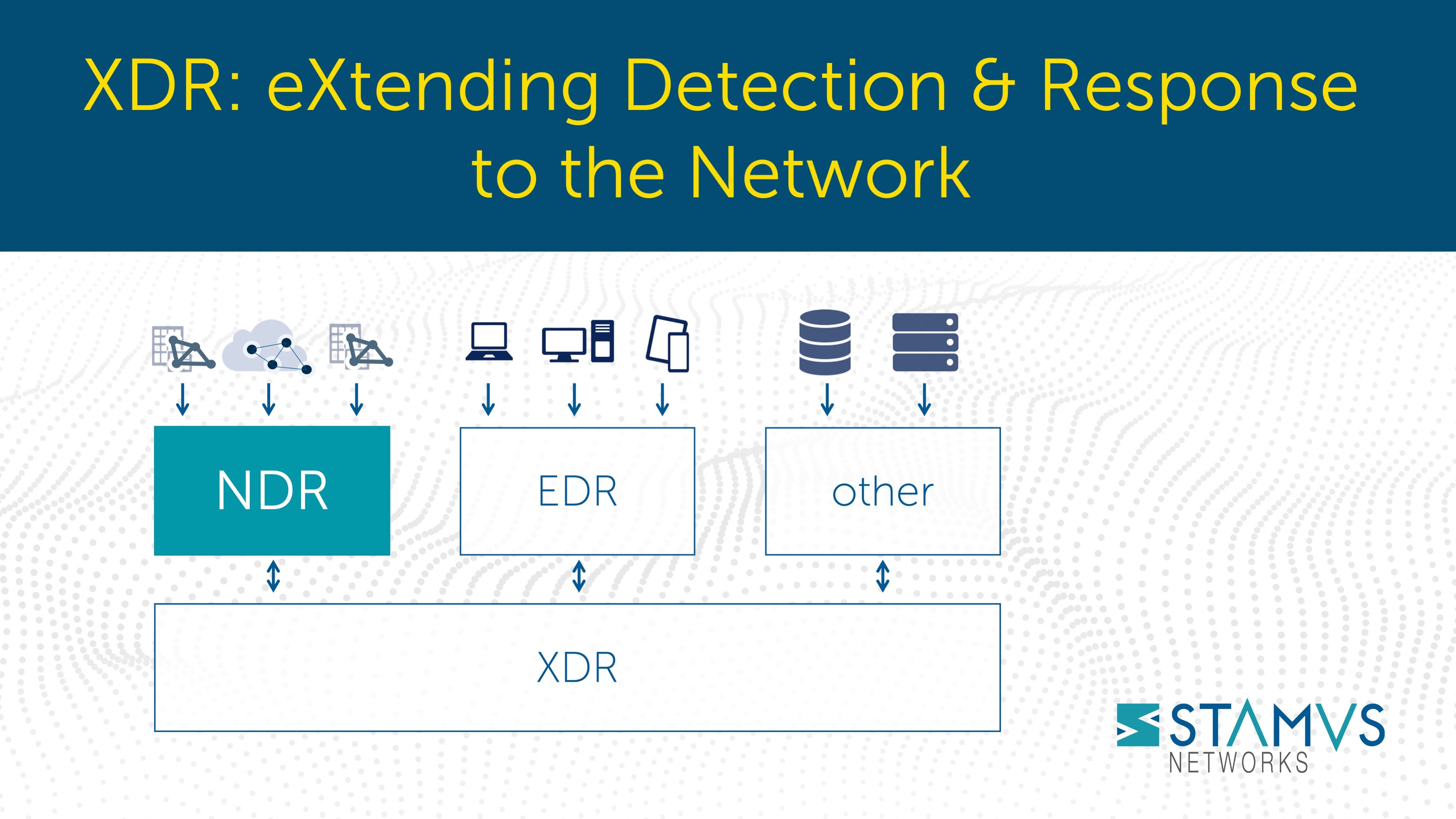
Extended detection and response, or XDR, has generated substantial interest in recent years - and...
Next week, Stamus Networks will participate for the first time in SecurityCON, a virtual...
As mentioned in an earlier article, organizations seeking to identify cyber threats and mitigate...
Organizations seeking to proactively identify and respond to cyber threats in order to mitigate...






.jpg)











.jpg)