Security monitoring is perhaps the least discussed element of a Zero Trust strategy
Over the past decade, the concept of Zero Trust has been heavily promoted and widely adopted by security practitioners. It’s grown from its humble beginnings as a network-centric concept into a more complete architecture and/or philosophy. Even while this more modern approach to Zero Trust is itself beginning to gain traction, an important element of the architecture is often ignored, neglected, or even shunned.
You may recall hearing about former American President Ronald Reagan's frequent use of his interpretation of the Russian proverb, “Doveryai, no proveryai (Доверяй, но проверяй),” beginning in 1986. Reagan explained that the U.S. will take a “trust but verify” approach to arms control negotiations with the Soviet Union.
Well, if “verify” makes sense with an entity you “trust,” there most certainly must be a continuous “verify” component to a system with Zero Trust.
So, what does a modern Zero Trust architecture look like?
Well, just this week Forrester analysts David Holmes and Jess Burn updated the definition originally proposed over a decade ago by their former colleague, John Kindervag. You can read their blog post here >>
They distinguish this new modern definition from its original by applying the popular "eXtended" moniker. Now referred to as Zero Trust eXtended (ZTX), Forrester has redefined Zero Trust eXtended as follows:
Zero Trust is an information security model that denies access to applications and data by default. Threat prevention is achieved by only granting access to networks and workloads utilizing policy informed by continuous, contextual, risk-based verification across users and their associated devices. Zero Trust advocates these three core principles: All entities are untrusted by default; least privilege access is enforced; and comprehensive security monitoring is implemented.
This final sentence is key here. It outlines the three principles of a Zero Trust strategy.
- Untrusted by default
- Least privilege access
- Comprehensive security monitoring
These are illustrated in the pyramid diagram below:
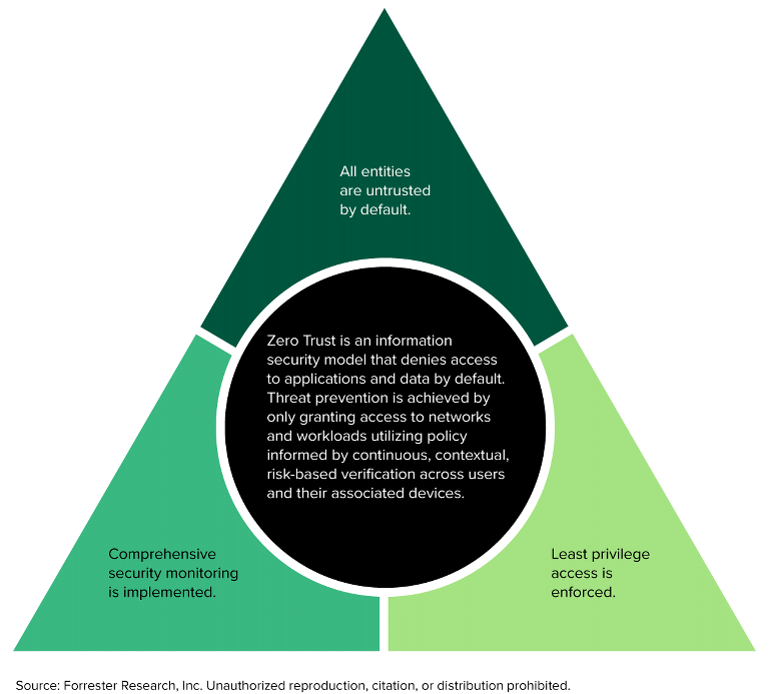
It is this last bullet (shown in the bottom left corner of the pyramid above) that remains widely disparaged and often overlooked. In fact, there are even advocates of Zero Trust who believe it to be completely unnecessary. This is, of course, nonsense.
The physical security team for a major banking operation in Paris would never consider skipping the installation of surveillance cameras or motion detectors in their vaults after installing physical access controls and limiting physical access to only those who need it. Similarly, cybersecurity executives who implement an untrusted-by-default model and least privilege access controls but fail to deploy comprehensive security monitoring are ignoring a critical element of the model.
While the phrase “trust but verify” was first uttered in the US by an American president, another US administration brought this concept full circle with a memo issued this week by Shalanda Young, acting director of the White House Office of Management and Budget (OMG).
In the memo, Young endorses the idea of continuous security monitoring, saying “it is a dramatic paradigm shift in philosophy of how we secure our infrastructure, networks, and data, from verify once at the perimeter to continual verification of each user, device, application, and transaction" [emphasis added]
If that is true, why is this core principle often neglected? Well, we intend to explore this more in upcoming blog articles.
Finally, as Forrester states, Zero Trust is an “information security model, one that can be worked toward but without an ultimate end state.”
Here we see that perfection is not the goal, but rather the goal should be one of continuous improvement in the direction of Zero Trust.
At Stamus Networks, we have made it our mission to help defenders advance their efforts towards Zero Trust through effective network-based monitoring and threat detection solutions.







