This series introduces SELKS 7, the latest update to the free, open-source, turn-key Suricata based Intrusion Detection/Protection System (IDS/IPS) developed by Stamus Networks. After nearly a decade of providing cyber defenders a capable, free IDS platform intended for small to medium businesses, home networks, and training, the seventh iteration of the SELKS system is now available for download. With the release comes new features and benefits, making it more powerful and capable than ever before.
For a brief overview of SELKS 7, go back and read part 1 of this series, SELKS 7: An Introduction. To learn more about how SELKS can be used, read SELKS 7: Deployment and Application. If you want to learn more about the new features included in SELKS 7, then continue reading.
What’s New in SELKS 7?
In SELKS 7, Stamus Networks has updated many capabilities to ensure that users have access to the most complete set of open-source network security tools. With new tools for hunting, updated integrations, predefined dashboards, and more, SELKS 7 provides greater usability and utility to users, whether they are implementing the system in a small to medium sized organization, on their home network, or for training purposes.
With SELKS 7, you will see improvements or completely new capabilities in the following areas
- Updated Network Threat Hunting Tools
- Dashboards and Reporting
- New Integrations
- SELKS on Docker
- Ruleset and Threat Intel Management
- System Monitoring
In the following sections, we share some details and example screenshots of each.
Updated Network Threat Hunting Tools
The hunting tools in SELKS 7 are primarily powered by the Scirius CE user interface, which provides predefined filters and enhanced contextual views to not only assist the hunter in searching for threats, but also to ensure they have all the information needed to investigate and stop threats once they have been found.
- New and Updated Queries and Filters
The newest version of SELKS places heavy emphasis on the ability to be fully functional right out of the box by providing additional predefined hunting queries, filtersets, dashboards, and visualizations. The capabilities of Suricata are further
advanced by the implementation of the Scirius hunting interface.
The predefined threat hunting filters designed specifically for Suricata not only give the hunter a starting point, but also provide greater context to the network information while minimizing noise. You can also create, save, and share your own custom hunting filters and queries. By combining wildcarding, negation, inclusion, and a few clicks, anyone can create powerful hunting filters.
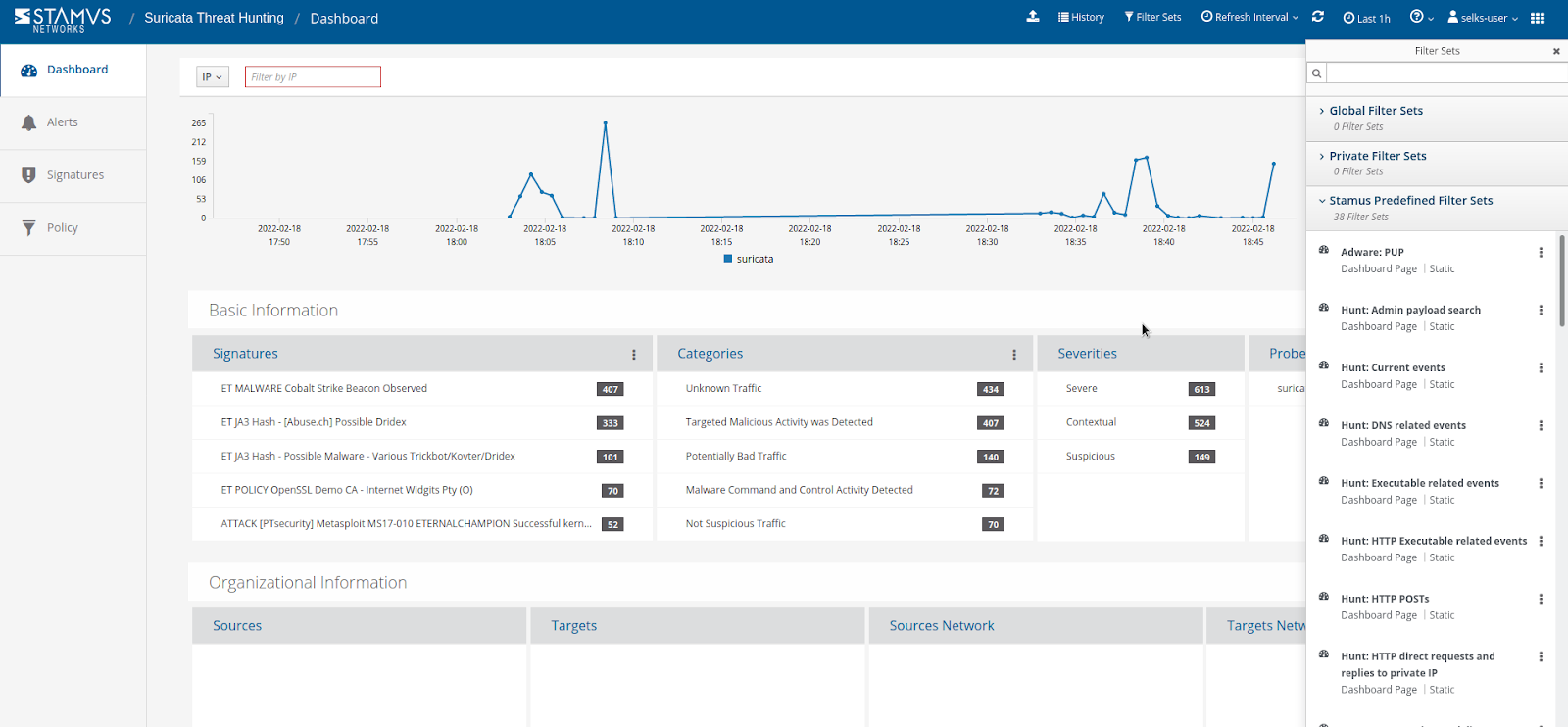
- Alerts Enriched with MITRE ATT&CK Context
The MITRE ATT&CK knowledge base is a valuable tool for the cyber defender. Based on real-world observations, the ATT&CK data enriches alerts, offering insight on adversary tactics and techniques. With SELKS 7, these enrichments are automatically made available when the fields are populated in the Suricata rules.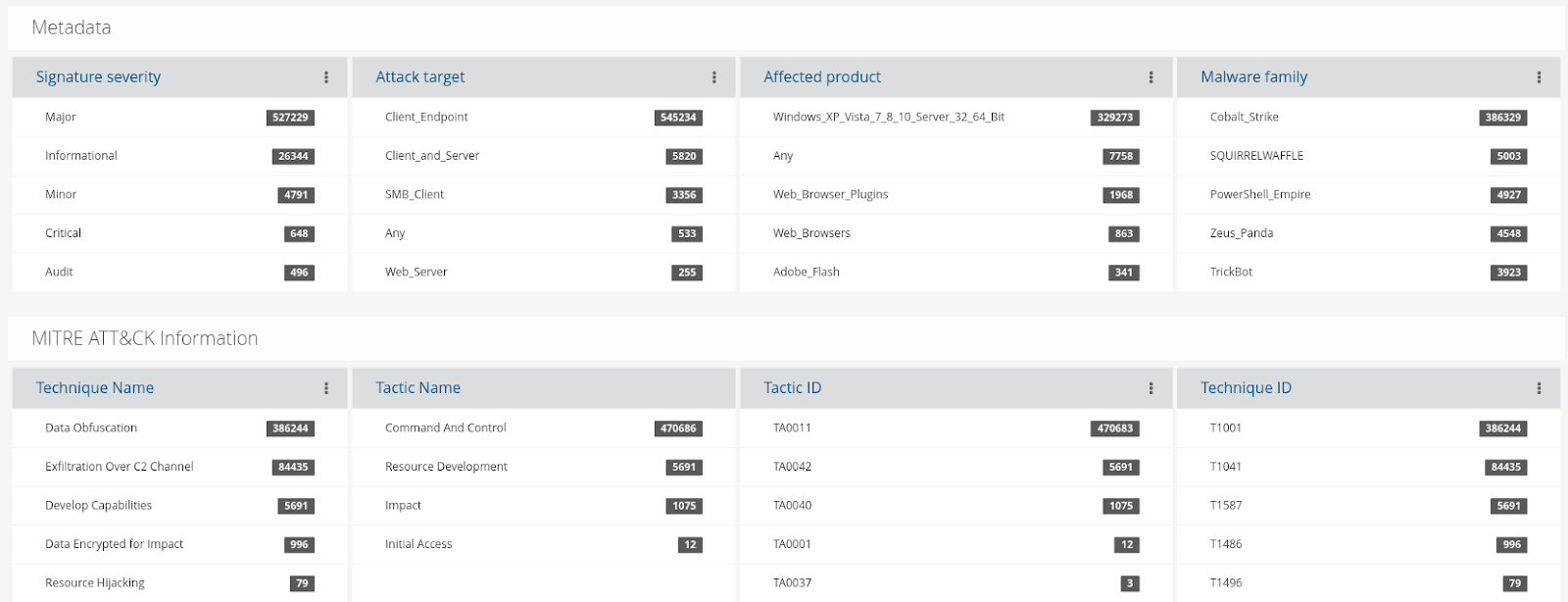
- Additional Contextual Insights and Forensic Data
Example - this predefined filter set lets you look for executable files being downloaded on the network: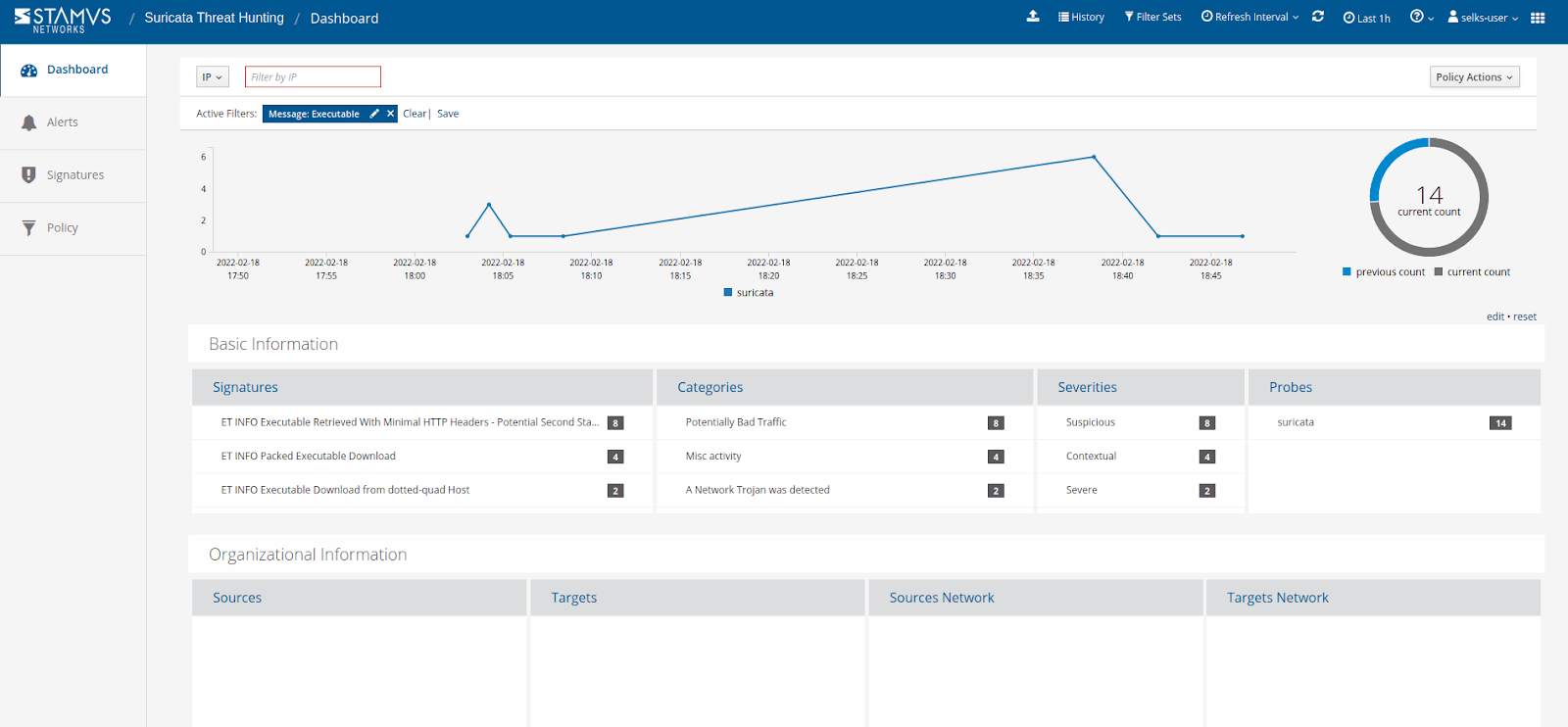
Additionally, you can review these related alerts across any time window: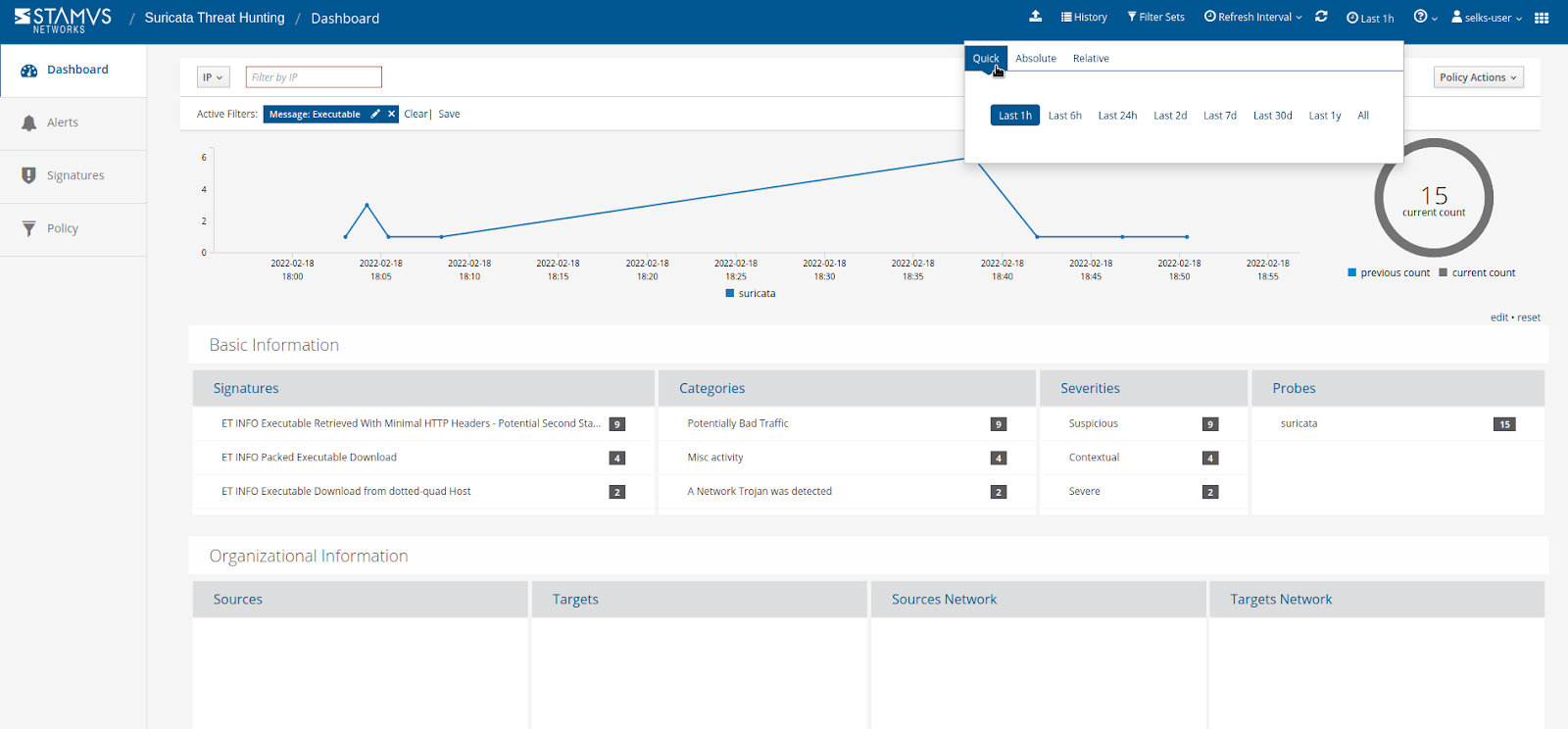
The alert payloads and metadata are displayed directly in the hunting interface: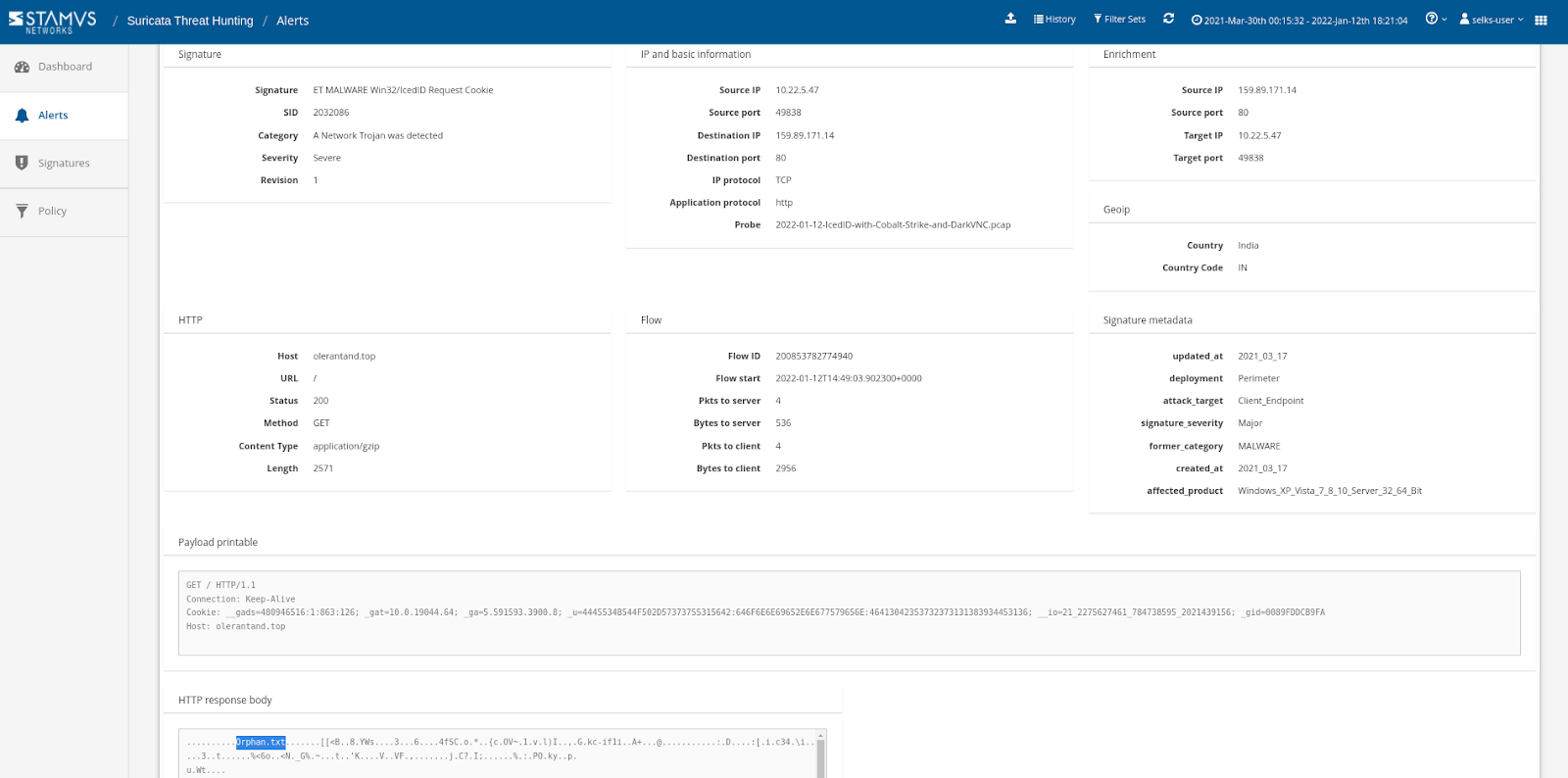
If you want to dig even deeper, you can see the protocol, flow, and file transactions associated with those alerts: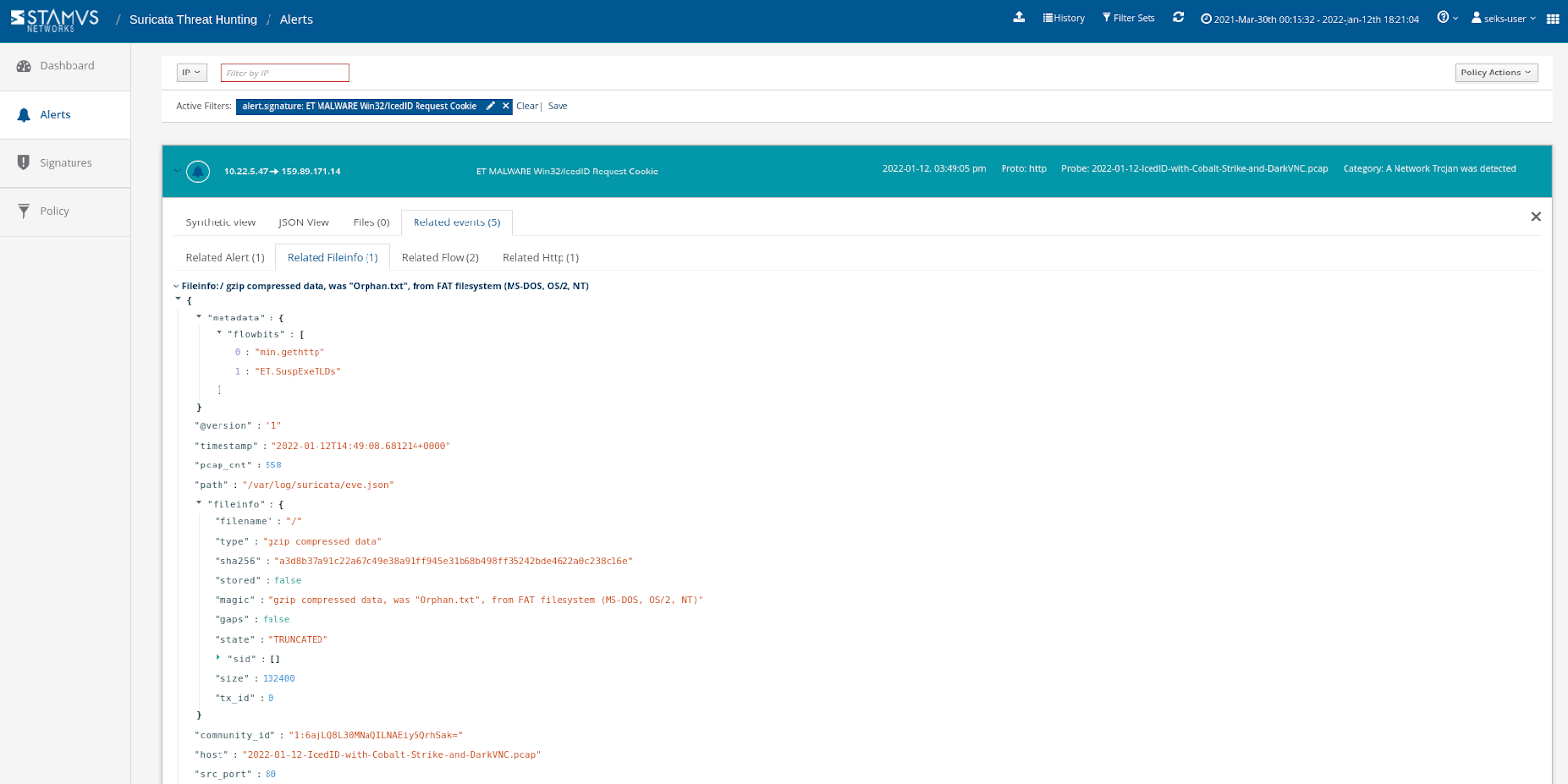
- Log and Monitor HTTP Events
SN-HTTP Kibana Dashboard: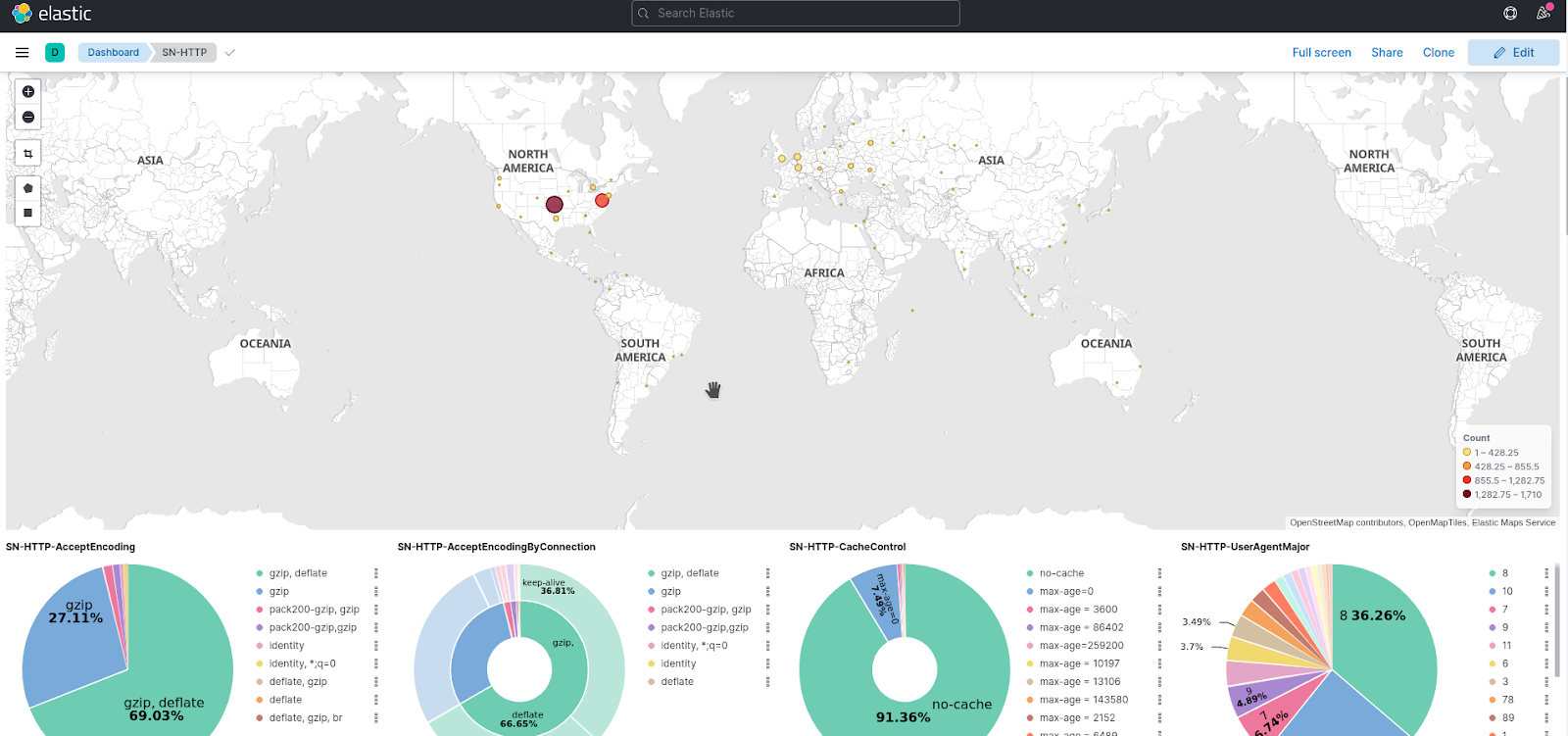
SN-Hunt-1 Dashboard: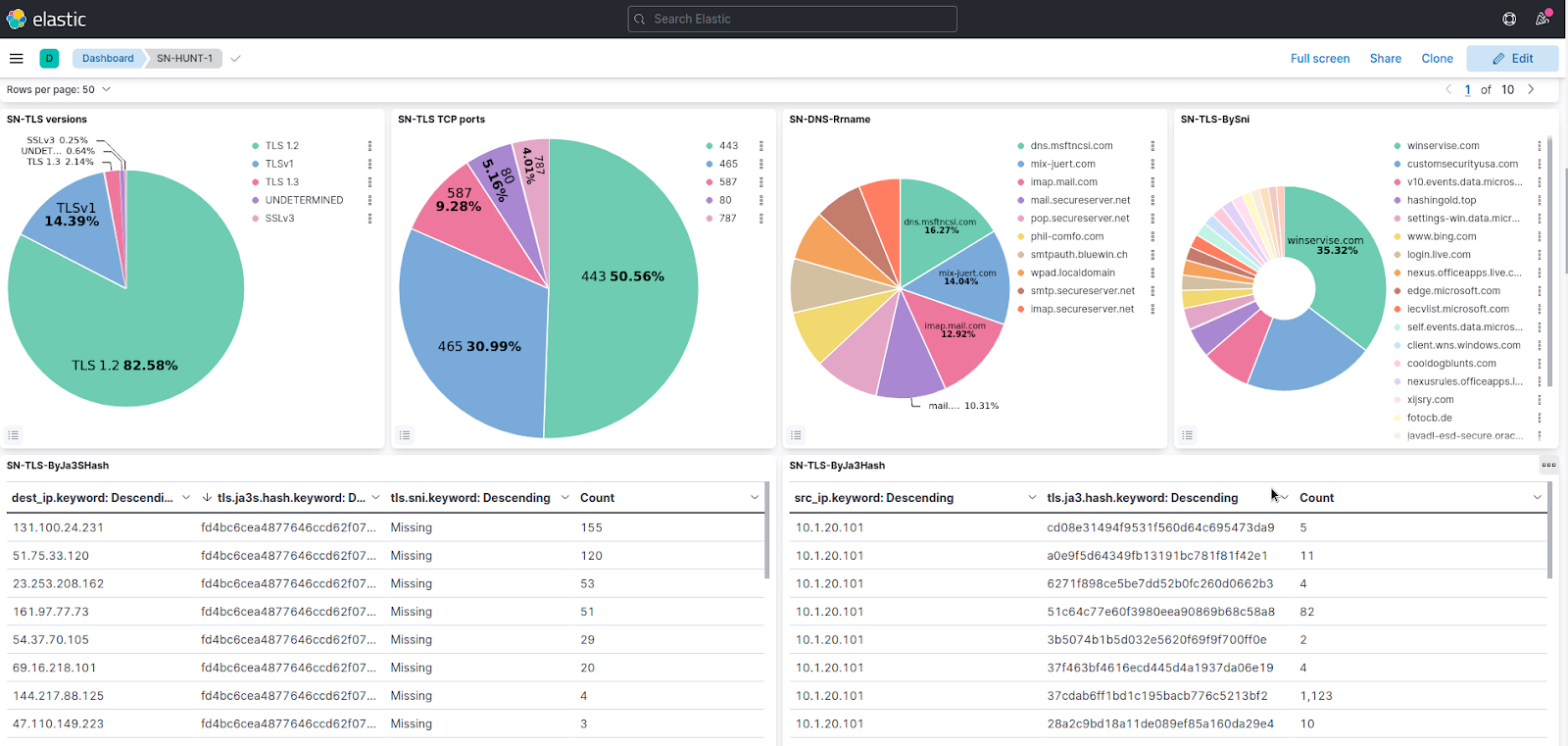
CyberChef at Work: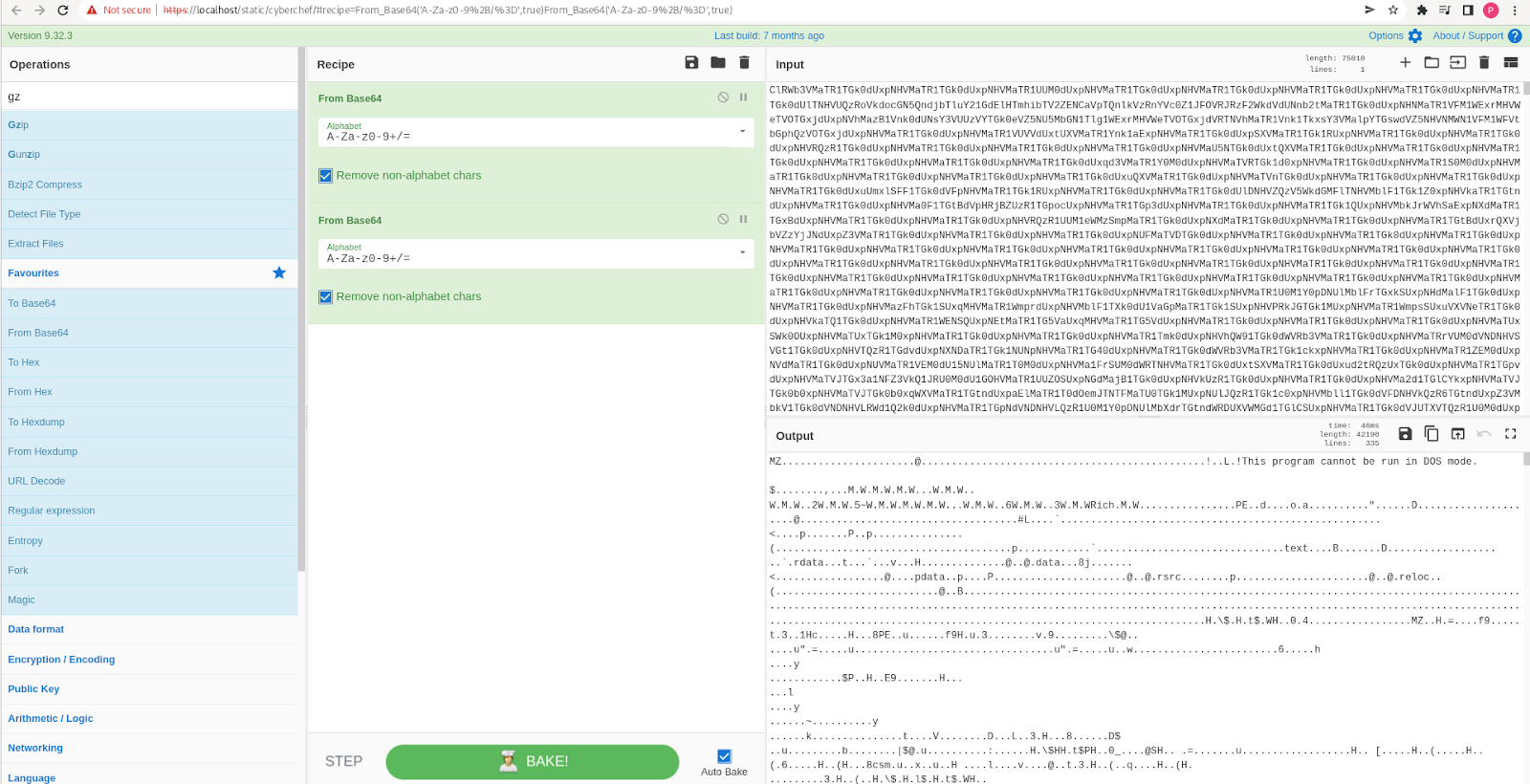
Arkime Viewer at Work: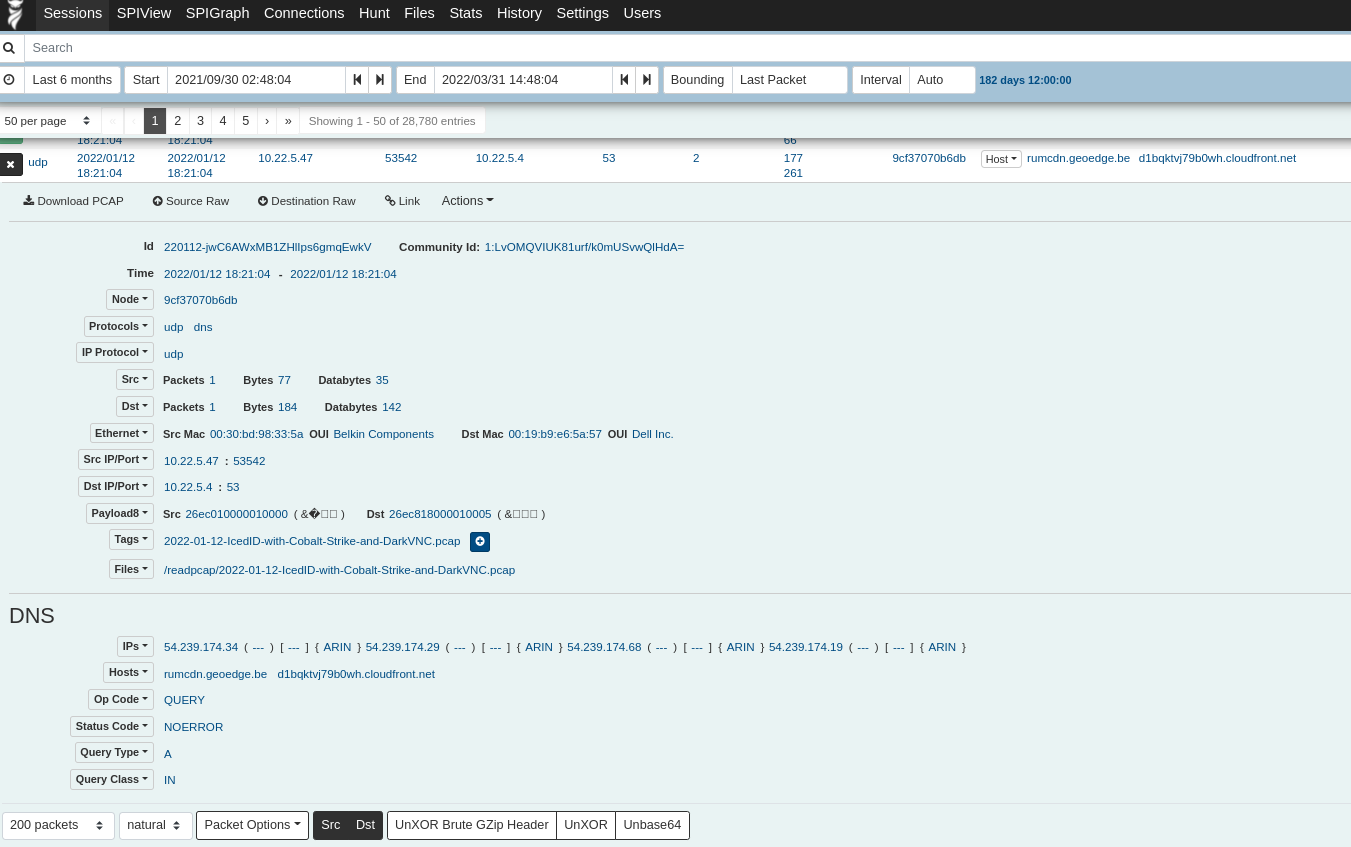
- Zoom in on Particular Flows With Evebox
An SMB transaction flow generated by Suricata: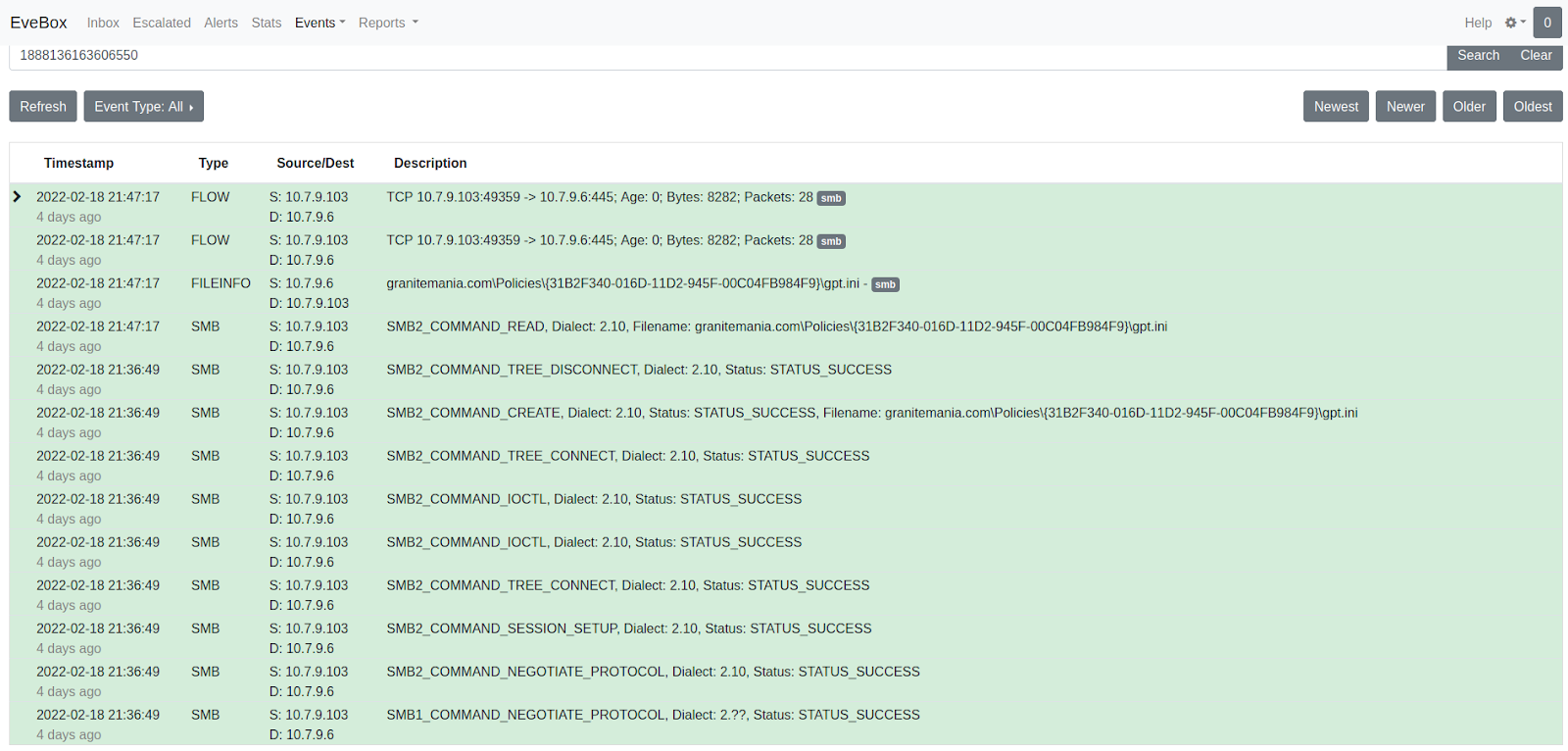
- Dashboards and Reporting
The ability to see different dashboards is vital to the user experience. One of the biggest benefits of SELKS 7 is that it provides a way to visualize all the data being fed through Suricata, allowing the user to get a complete picture of what’s taking place on their network and generate reports.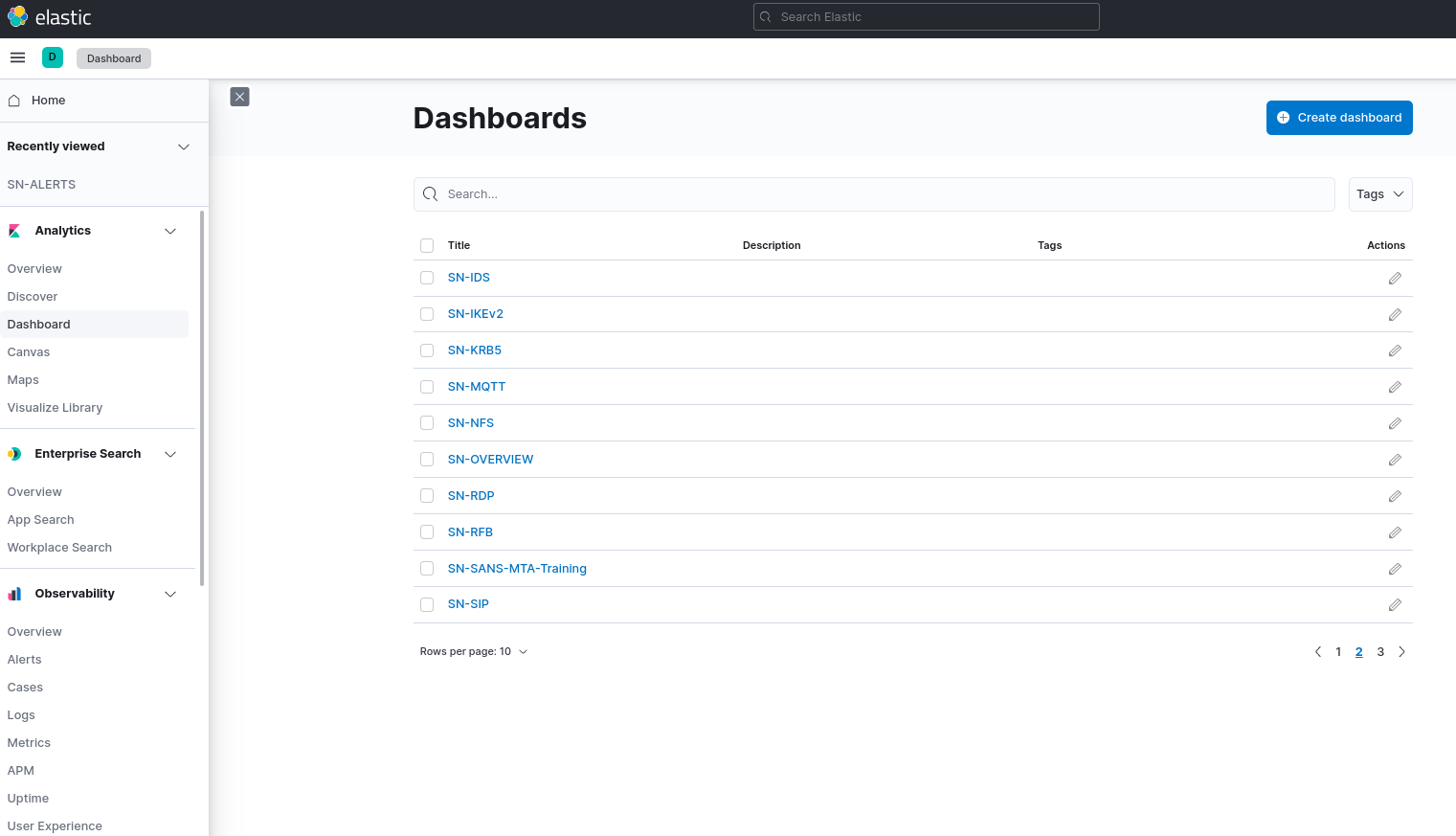
- New Integrations
As an open-source platform powered by the community, SELKS 7 is embedded with several other applications, including Kibana, Evebox, Cyberchef. In this version, switching between those applications is simple and seamless.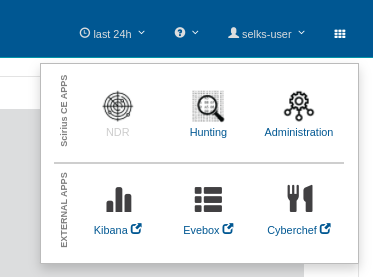
- SELKS on Docker
The biggest change when it comes to integrations is the Docker implementation of SELKS 7. Every key component is now stored inside a separate, individual Docker container/volume. This provides an easy way of upgrading or version locking of the different components separately or together based on your needs. making it very flexible for deployments to cloud setups like Amazon, Azure, or Google.
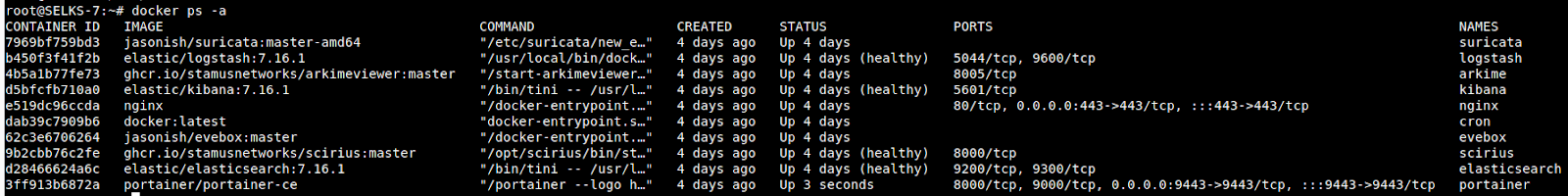
When deploying the SELKS 7 Docker implementation you also get the latest docker images. At the time of official release those are:
- Scirius CE (Community Edition 3.8.0) - Including improvements and bug fixes in the threat hunting interface while incorporating dozens of predefined threat hunting filters.
- Kibana 7 (7.16.1) - 28 ready to use and up to date dashboards, over 400 visualizations, and 24 separate searches that correlate alert events to network security monitoring (NSM) data.
- Elasticsearch 7 (7.16.1)
- Logstash (7.16.1)
- Suricata
- Portainer (2.11.1)
- EveBox
- Arkime (3.2.1) - a phenomenal tool with an intuitive web interface for packet capture and view.
./easy-setup.sh --elk-version <version-number>
You can do the same with the Scirius version. The version can be a branch name, tag, release number, or a git sha.
./easy-setup.sh --scirius-version <version>
- Ruleset and Threat Intel Management
SELKS 7 is rules and threat intel agnostic and it can manage multiple Suricata rulesets and threat intelligence sources including both custom and local instances.
Example: Predefined sources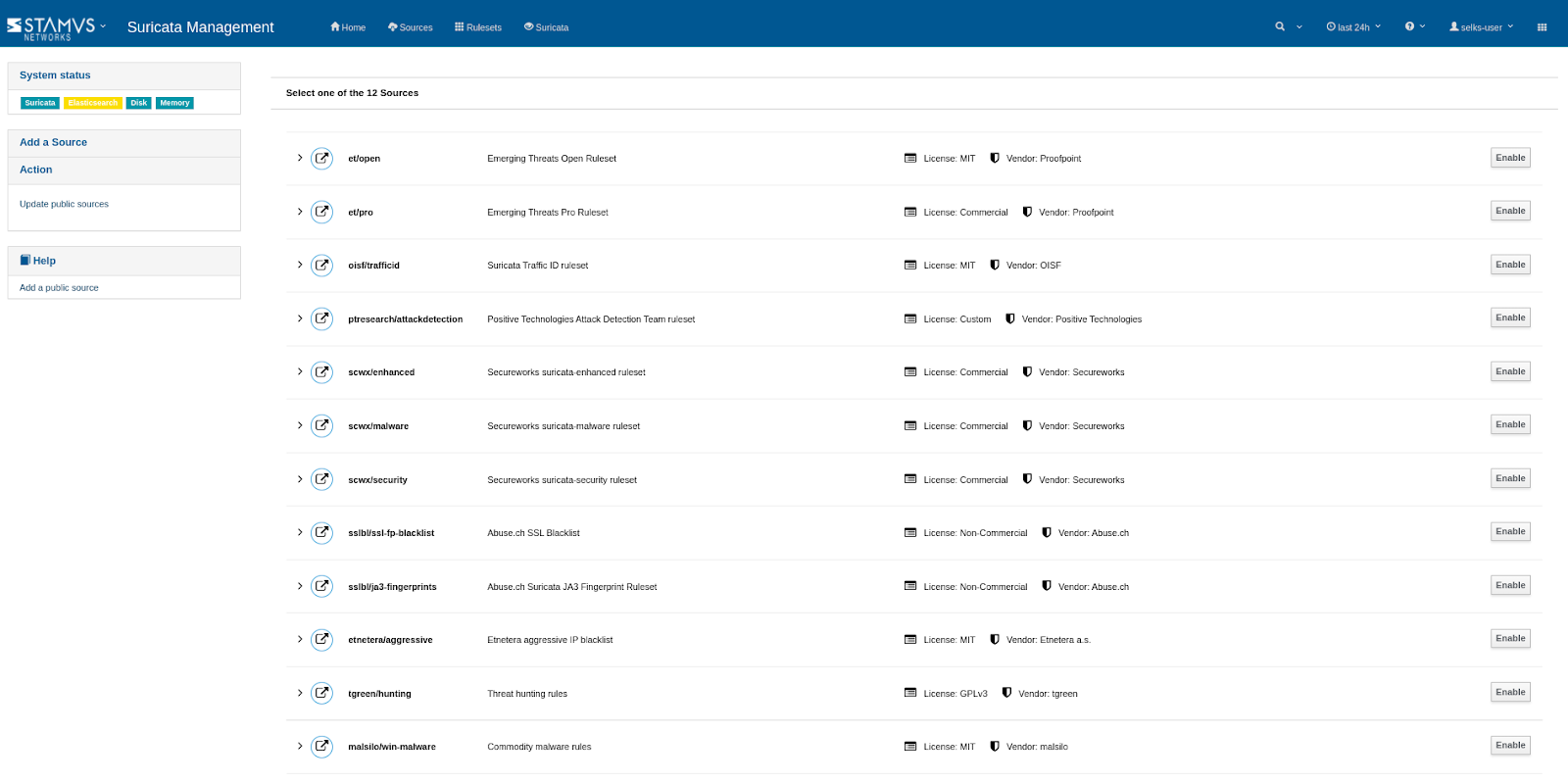
Example: Multiple sources used for the same ruleset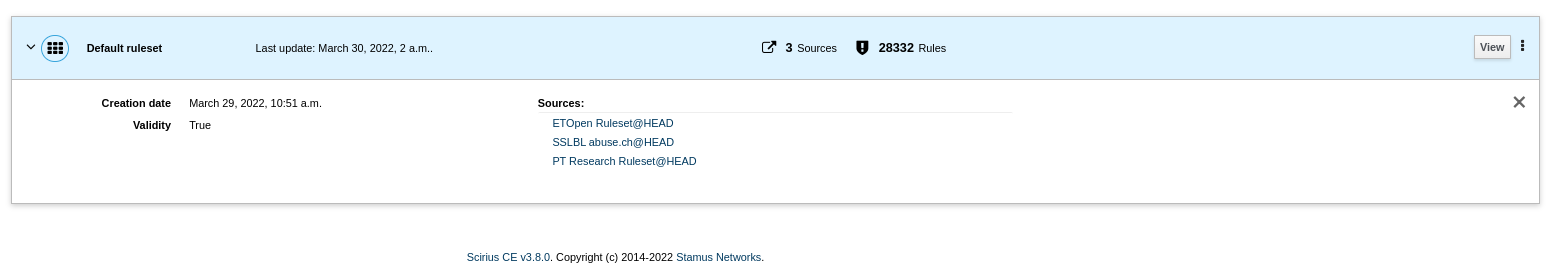
- System Monitoring
By utilizing Portainer, SELKS 7 now enables you to manage and observe the health status of the SELKS Docker stack:
Example: Portainer Dashboard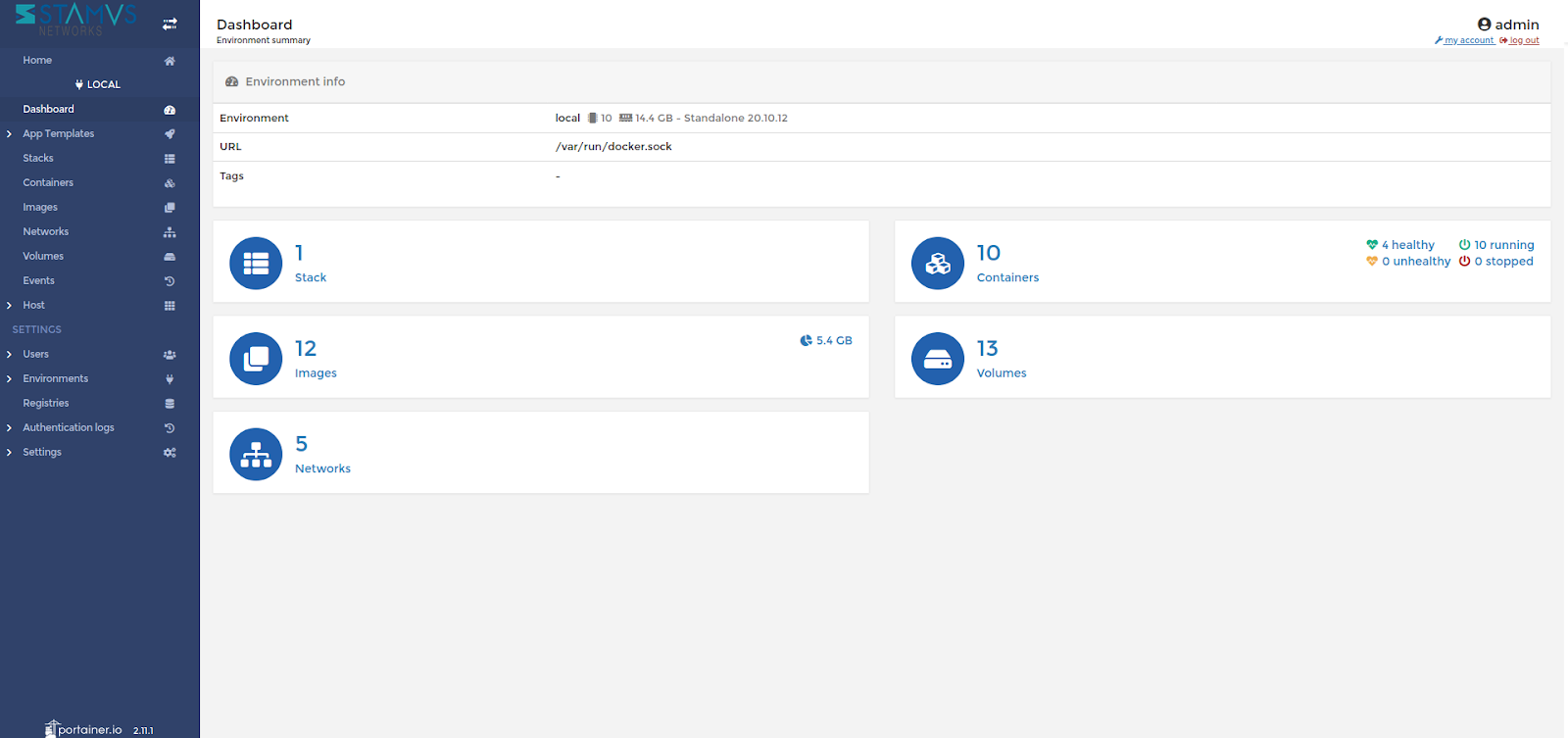
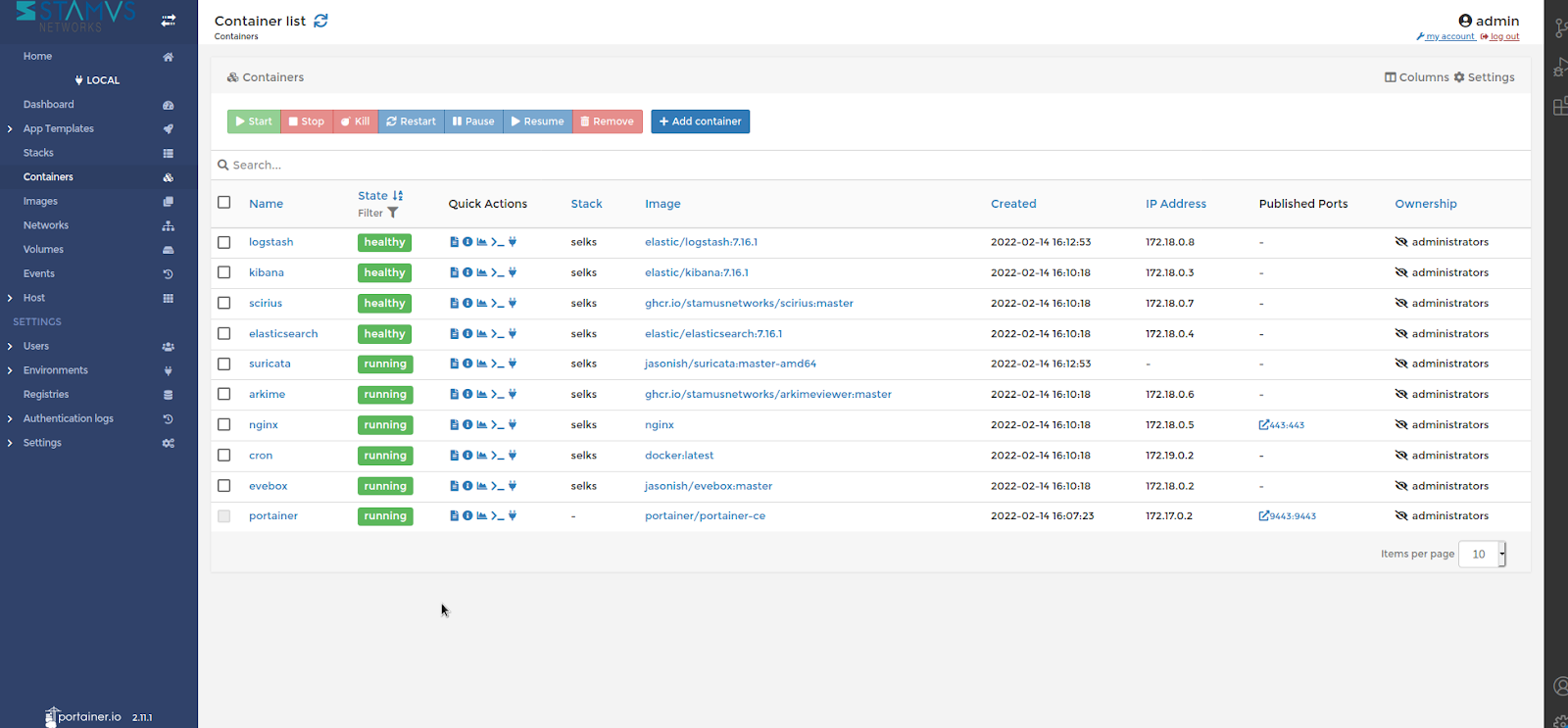
- Example: Container List
SELKS 7: Always Improving
These new features were included with the cyber defender in mind. No matter what you use SELKS 7 for, you can be sure that the system has included as many tools as possible to ensure that your network stays secure. Feel confident in your ability to locate threats and neutralize them before they cause any harm.
To learn more about how to deploy SELKS 7 and get an idea of some of the ways it can be used, read SELKS 7: Deployment and Application. Try it for yourself today – have the system downloaded and launched in less than 2 minutes.






