Perhaps the most exciting thing about the release of SELKS 7 is the various practical applications that the platform’s new capabilities make available. As a free, open-source, turn-key Suricata IDS, SELKS 7 is meant to make highly effective network defense available to anyone who wants it. With this latest version, there are multiple ways to deploy the system, making it accessible whether you use a virtual machine, the cloud, Linux, or Windows operating systems.
This article describes those deployment options, as well as various practical applications and use cases the SELKS system is optimized for. If you need a brief overview of the SELKS platform or want to know more about the new capabilities included in the seventh version, take a look at the previous articles, SELKS 7: An Introduction and SELKS 7: Updated Capabilities.
How to Deploy SELKS 7
SELKS 7 is built with ease of deployment in mind. No matter which environment works for you, whether virtual, cloud, or physical, SELKS is easy to download and launch. It can be imported as a virtual machine, installed as an image, or deployed on any Linux or Windows operating system that supports Docker.
- ISO
If you plan to have SELKS running offline, you can download ready to use images from the SELKS download page. You’ll find the first time set-up guide here. - Docker
SELKS 7 can be set up on any Linux OS in minutes via Docker compose. The system comes in a container setup, allowing you to deploy it on any major Linux OS distribution. With only a few command lines, you can launch a brand new SELKS 7 IDS, IPS, or NSM. Read here to learn more about the process.
Practical Applications
As an open-source toolset, SELKS 7 is provided as a free resource to the greater cyber defender community. The intent is to give powerful tools for network defense to anyone who wants it.
While you can freely use SELKS 7 however you wish, here is a short list of some different use cases that might provide context for the types of applications SELKS 7 could be used.
- Protection and Visibility
SELKS 7 provides strong network monitoring and threat detection thanks to its use of Suricata. It natively provides alerts, network protocol transactions, file extraction, pcap capture, network flows, and ready-to-use dashboards and hunting filters. By seamlessly integrating several open-source tools, SELKS consolidates various network information onto a single platform. This, in turn, provides context and visibility to each network event or alert, ultimately helping to protect your network. - Training
Due to its ease of deployment, SELKS is a perfect tool for training and teaching network visibility and threat hunting. It is also the perfect program to use for “Capture the Flag” exercises in university cyber security classes and programs. Students can learn about different Suricata alert metadata and how to decipher which alerts are truly important amidst all the noise generated by a typical IDS.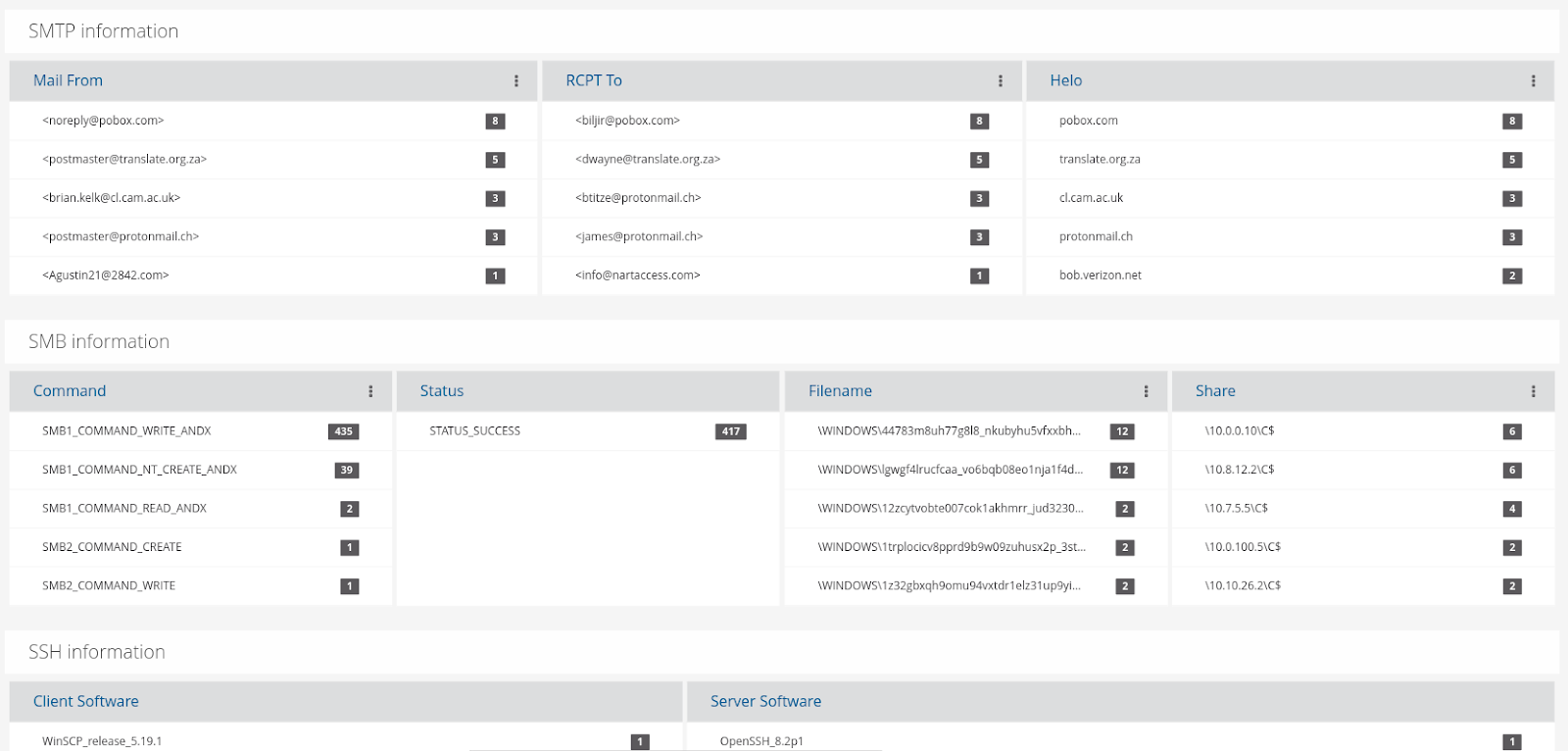
- Reading PCAP Files
With SELKS, you can ingest multiple different PCAP files in a series, while also keeping those cases separate. This allows the user to stay organized while still receiving important context. Importing a PCAP only requires one simple line of code:
scripts/readpcap.sh -a /opt/hunt/Workshops/2022/pcaps/2022-01-12-IcedID-with-Cobalt-Strike-and-Dark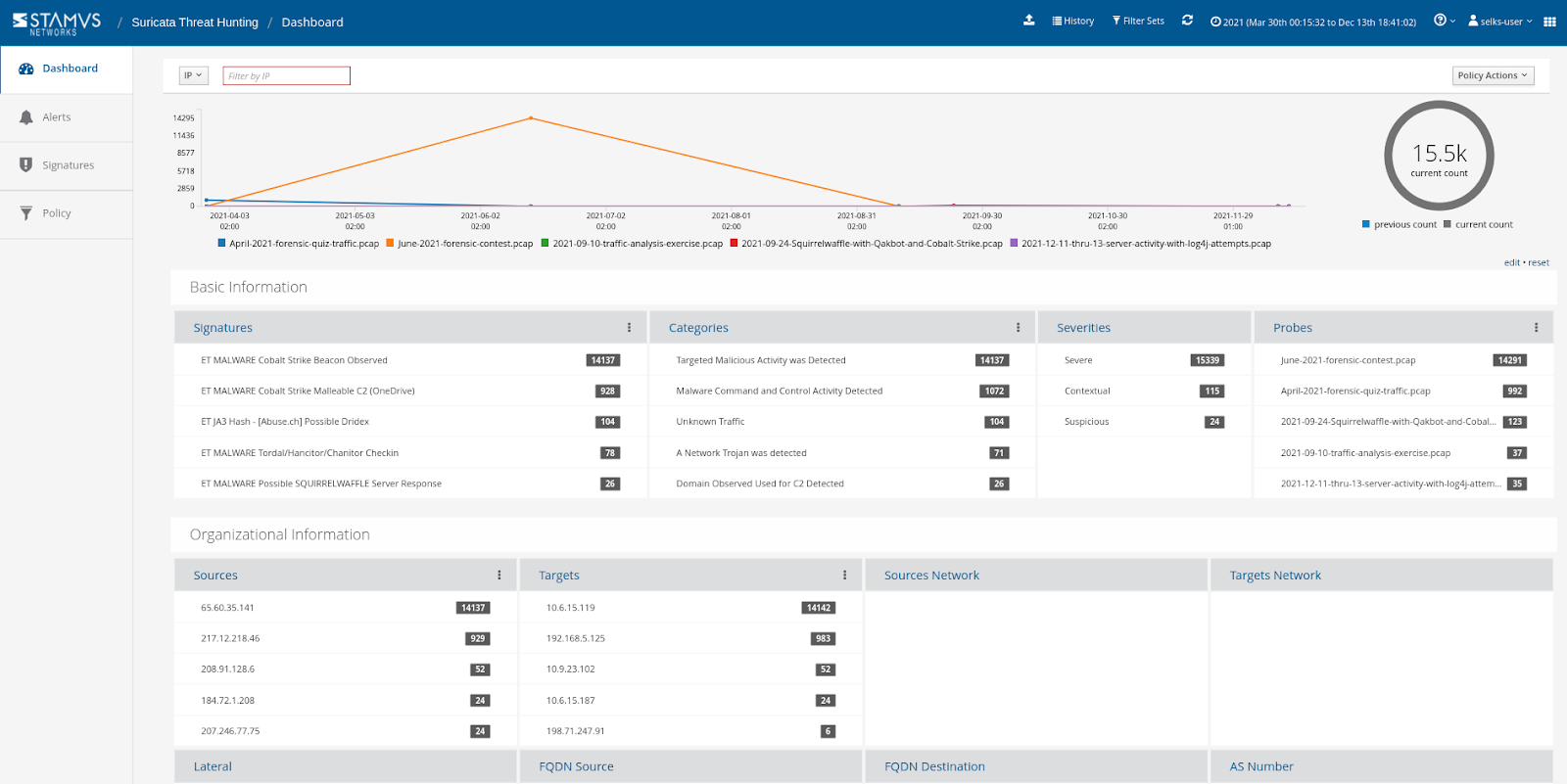
- Comparing Different Malware Behavior and Cases
By taking advantage of the SELKS system’s ability to ingest PCAPs, you can teach, train, analyze ,and compare the behaviors of different malware from the network perspective. For example, we retrieved some free malware samples from malware-traffic-analysis.net to collect and analyze this data: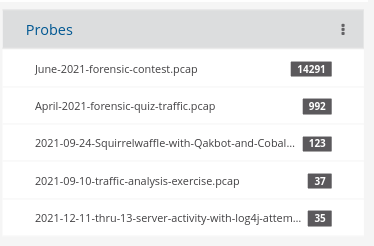
- Incident Response and Analysis
Though primarily used for threat detection and prevention, SELKS 7 can also serve as an important element in incident response by providing valuable network visibility via its easy-to-use interface. It can help you assess your current cyber threat posture with powerful threat detection while also providing fast, valuable network monitoring information in an ongoing incident response.
SELKS 7: A Complete, Free, Open-Source Network Security Solution
SELKS 7 is an open source network detection and security monitoring tool that is easy to deploy. It is operating system agnostic and allows you to quickly spot trends and anomalies within your network. Additionally, it further enhances your cyber defense by providing context and traceability around alerts and/or network protocol events such as malicious user agents or vulnerable application versions. With this extracted data, you can make more informed decisions on how to respond to and protect your network from any harmful threats.
SELKS is also very straightforward to deploy, allowing users to start learning more about network security monitoring from a Cyber Security perspective. It has a community of followers and contributors that are ready to help. As always, Stamus Networks gives a big and respectful thank you to all the open-source tools that are a part of SELKS, their authors, and the communities around them!
To connect with the SELKS, Suricata, and threat hunting community, take a look at these resources:
- Discord - join the community and get support
- Wiki - read the docs
- GitHub - contribute to the codebase, log an issue, or access the individual pieces of code
- The Other Side of Suricata - Blog
- Suricata Myth Busting: Alerts and NSM - Blog
- Complete Suricata Network Security Platform in 2 minutes - Blog
- Other Stamus OSS Projects






