Clear NDRTM helps bank identify threat to its accounting network
With the help of the Clear NDR, one of our European financial services customers made an interesting discovery of suspicious activity on their network that resulted in a substantial incident investigation and response.
Background
In this series of articles, we explore a set of use cases that we have encountered in real-world customer deployments of our network detection and response solution, Clear NDR. In each case we work to explain what we found, how we found it, and why it matters.
In this situation, the customer is a subsidiary of a large European banking and insurance conglomerate (also a customer) with a mix of on-premise, branch office, public and private cloud assets. They have a substantial security infrastructure in place, including endpoint detection, VPN, firewall, and multi-factor authentication from many of the industry’s top security vendors.
Their network detection and response solution from Stamus Networks is deployed with a mixture of physical and virtual probes (Clear NDR Network Probes) feeding the centralized analytics engine and console, Clear NDR Central Server.
Active threat hunting finds suspicious user agents
It was a typical Friday afternoon … or at least that’s what the Stamus Networks incident support team was thinking.
But, then we received the call.
One of the bank’s security analysts informed us that, during a recent active threat hunting session, they uncovered a “substantially unusual security event” in the network traffic data provided by their Clear NDR installation.
They identified what appeared to be Chinese and Korean alphabet characters in the HTTP user agent fields within protocol transactions on the accounting department’s network. This was suspicious because the bank does not do business in China or Korea, and would not expect to see these characters from any of its systems.
Investigation with Clear NDR
What follows is an account of our team’s findings after we were brought in to assist in the investigation. Our analyst decided to initiate the hunt from scratch to see if we would come to the same conclusions as the bank’s analysts.
Notes:
- The screenshots shown are heavily redacted due to the sensitivity of the investigation and of the nature of the supply chain breach that was involved.
- This environment poses a couple of challenges to the threat hunter. The sheer volume (100s of millions) of daily network log transactions creates a massive haystack in which to find the proverbial needle in the haystack. And a 45 minute IP address lease time for remote clients creates a large number of dynamic IP addresses, each with very temporary behaviors.
While looking into a few of the security events that had been automatically classified by Clear NDR as “relevant”, our analyst clicked on a particular IP address and pivoted to the SSP Host page.
The Host page displays all the services, user agents, JA3 fingerprints, usernames, hostnames associated with a given asset, based on protocol transactions observed by Clear NDR. The best part about this display is that it presents the data with all the organizational context available, such as network names and department names, making it easy to make sense out of the information.
We expected to see access to these hosts from potentially dangerous geographies or perhaps rogue software running on the network. Instead, we mostly saw a number of expected regular engagements from business partners operating in expected locations.
However as we kept digging, our analyst discovered a series of transactions involving very unusual HTTP user agents. In Figures 1 and 2 below, you can see that one of the communications to a specific business partner of the bank stands out.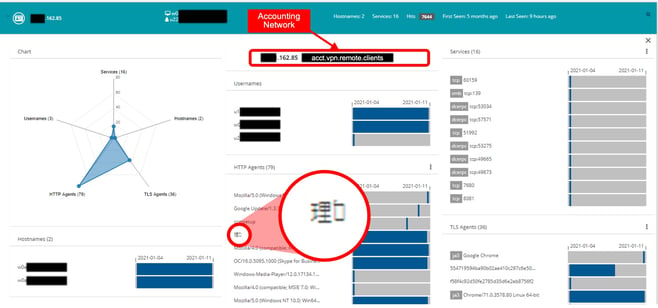
Figure 1. Initial portion of the host page for the first IP address 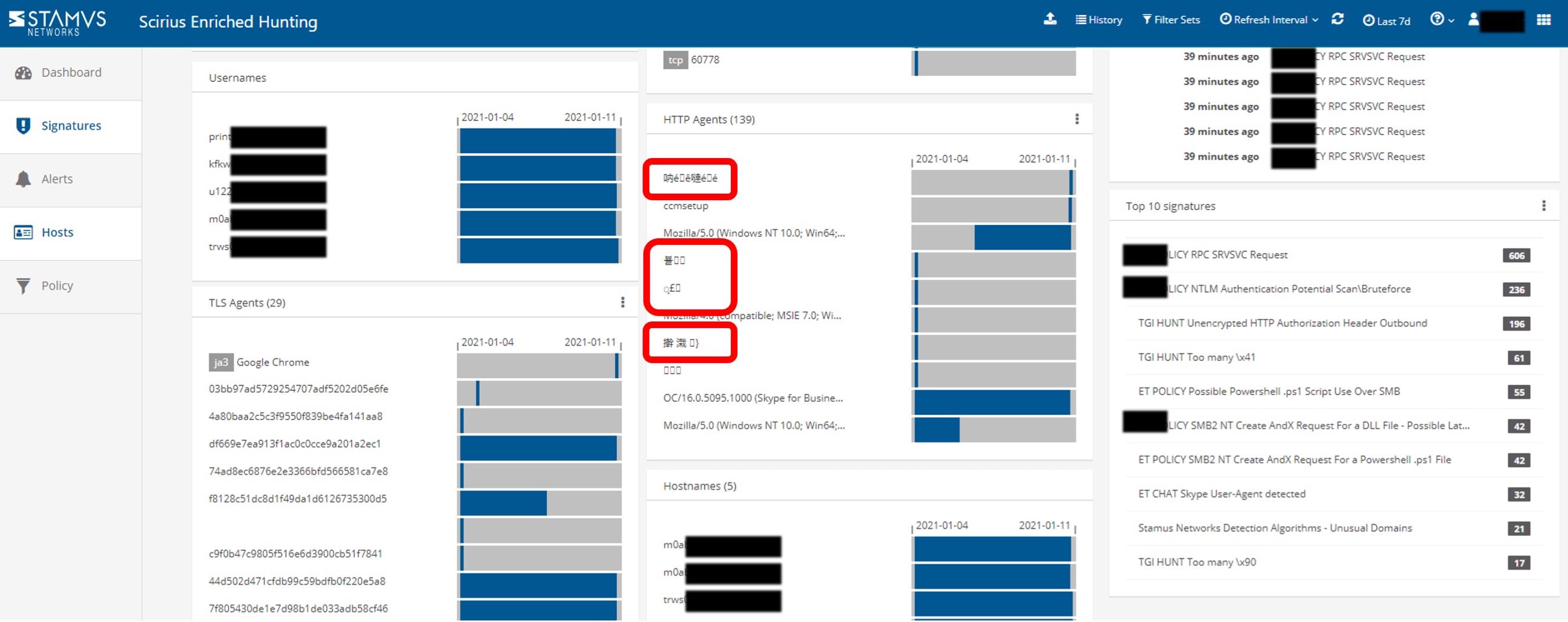
Figure 2. Second part of the host page for the first IP address
Here, we can see that specific clients from the accounting department are using Chinese and Korean alphabet characters in the HTTP user communications. The bank confirmed they do not do business in China or Korea nor do they have any known customers or partners in Asia, so we continued the investigation.
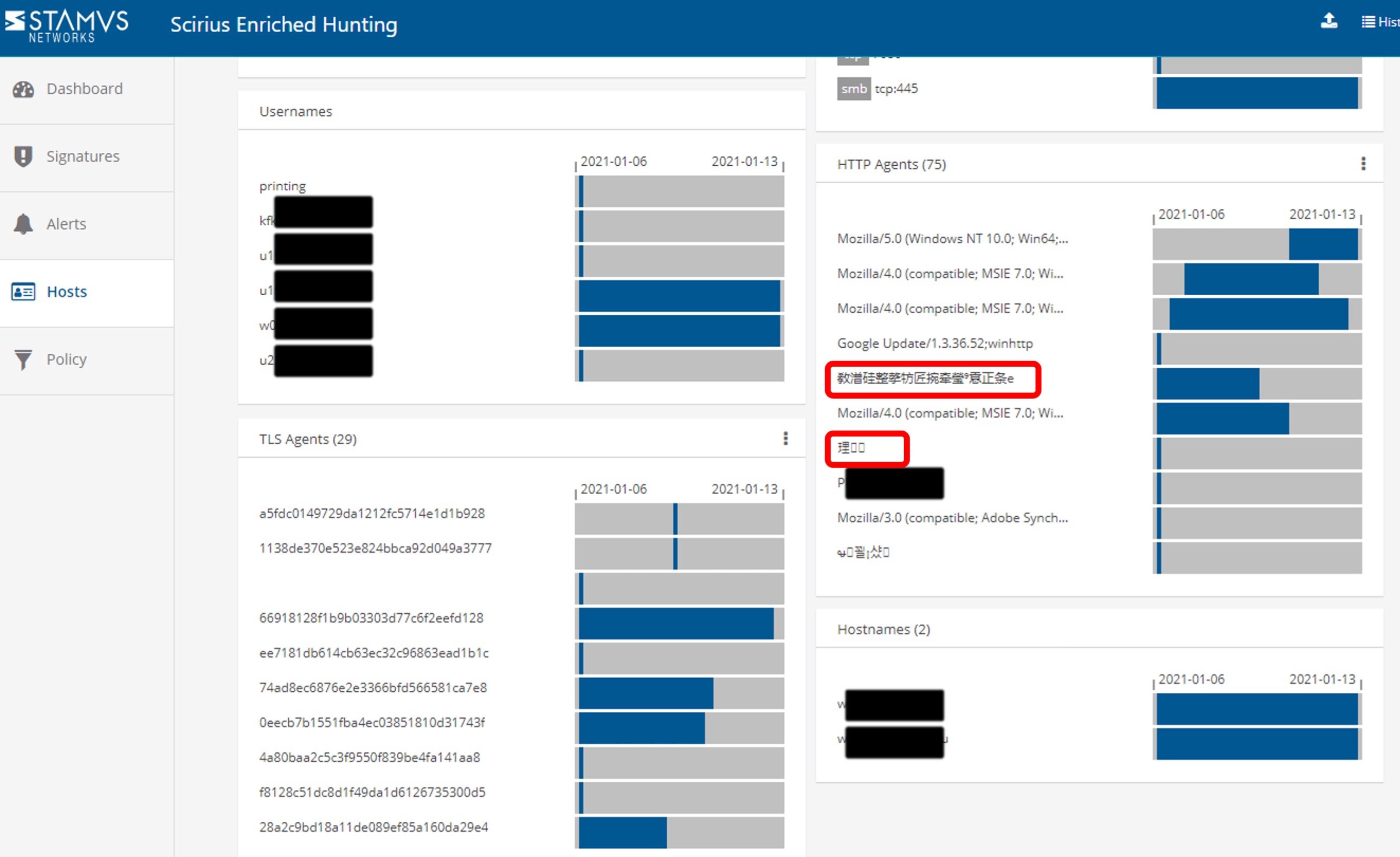
Figure 3. Further examples of Chinese and Korean characters in the user agents.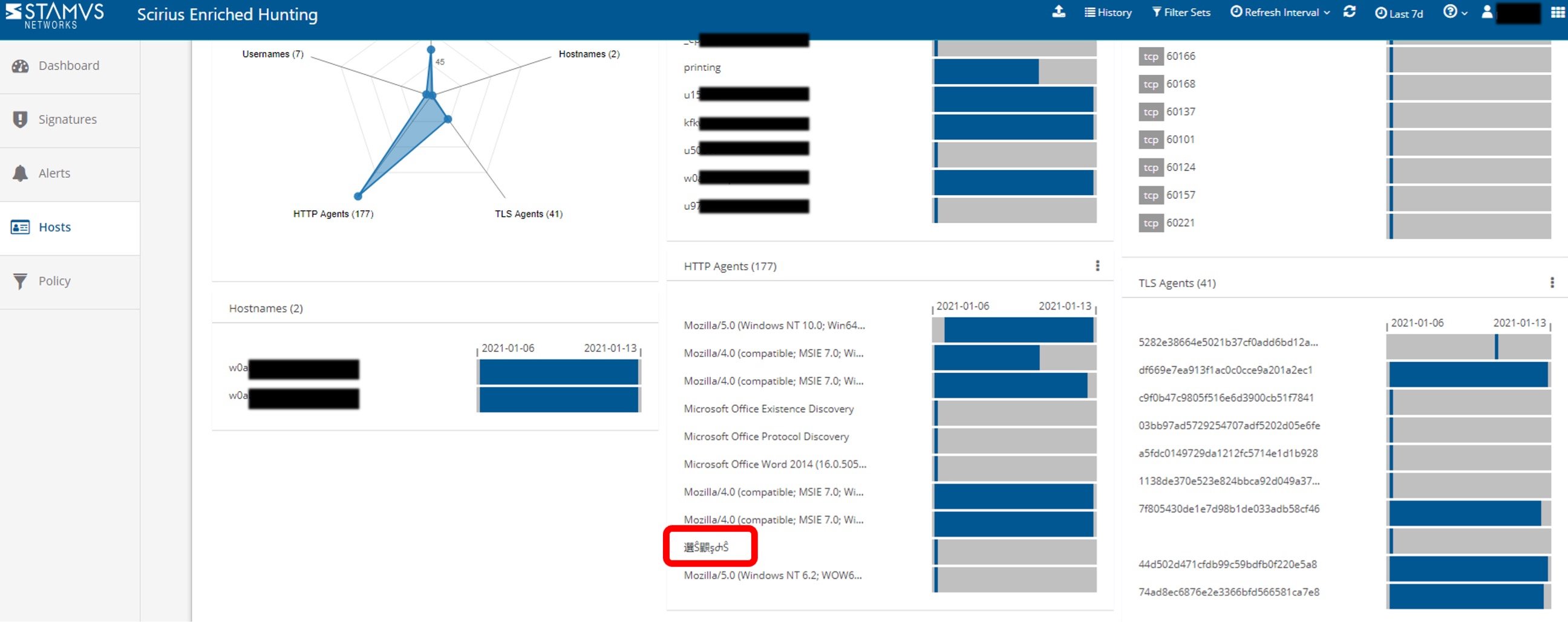
Figure 4. Further examples of Chinese and Korean characters in the user agents.
One of the powerful features of the Clear NDR hunt interface is it’s search and filter capabilities that allows us to search (or wildcard-negate) for specific letters/symbols or any combination thereof, regardless of alphabet. By using this capability, we were easily able to identify all the offending systems.
See Figures 5 and 6 below.
Figure 5. Example searching for strings used in HTTP user agents.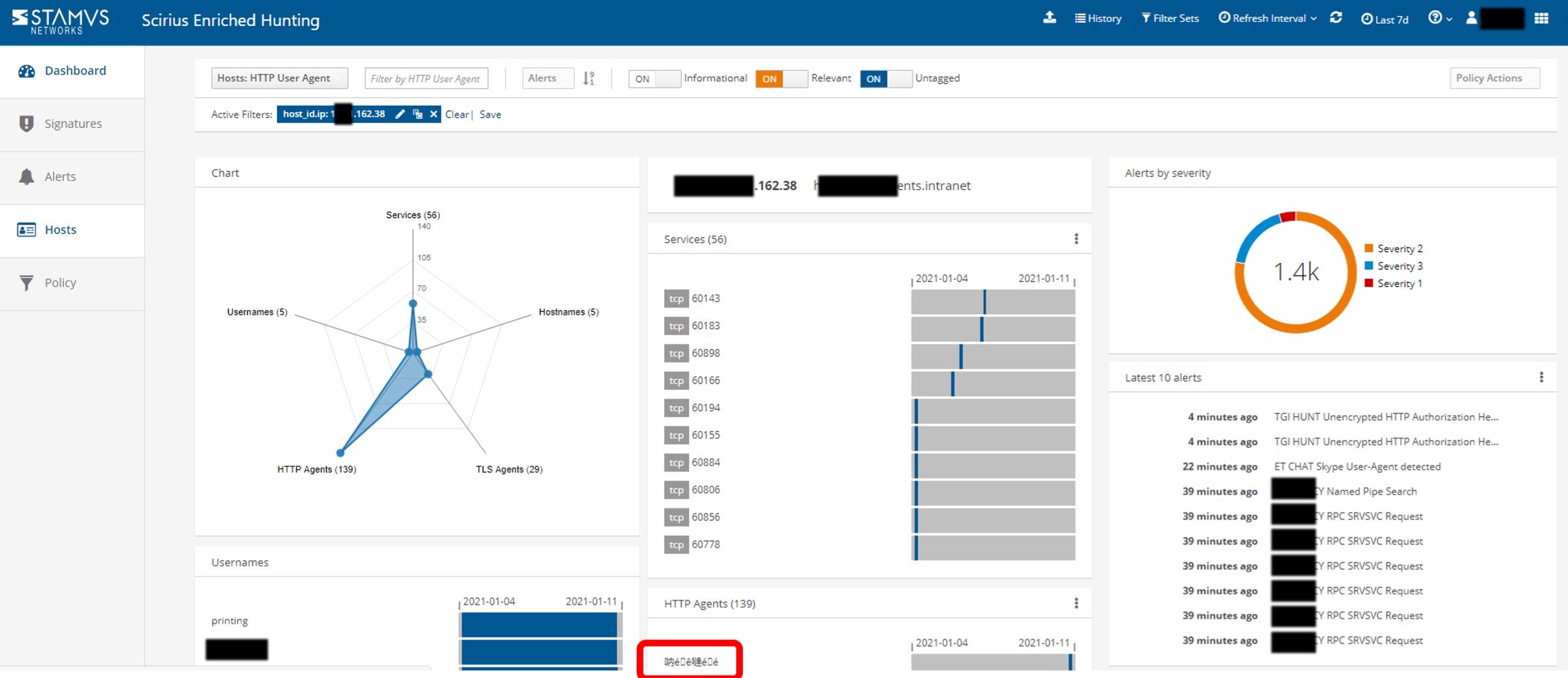
Figure 6. Results of searching for specific strings used in HTTP user agents.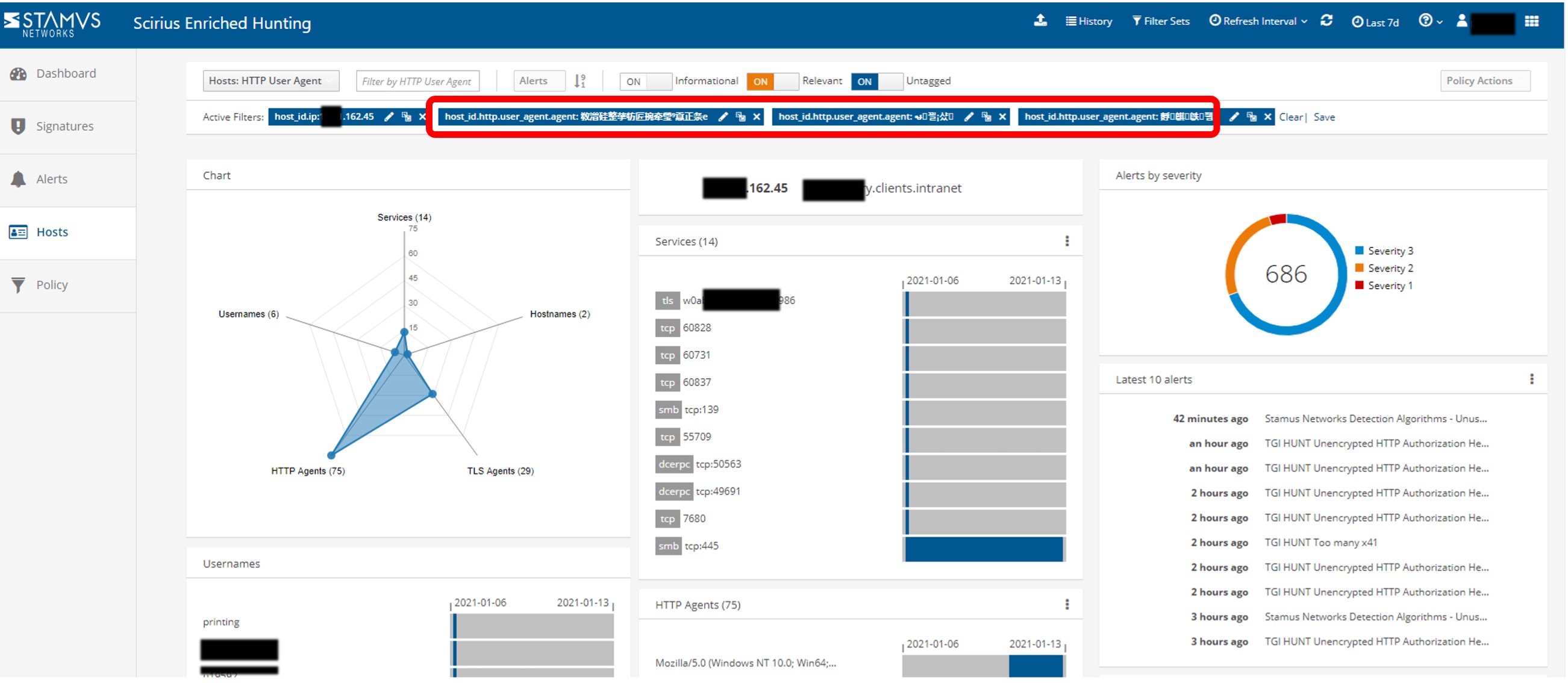
Figure 7. Additional results searching for strings used in HTTP user agents.
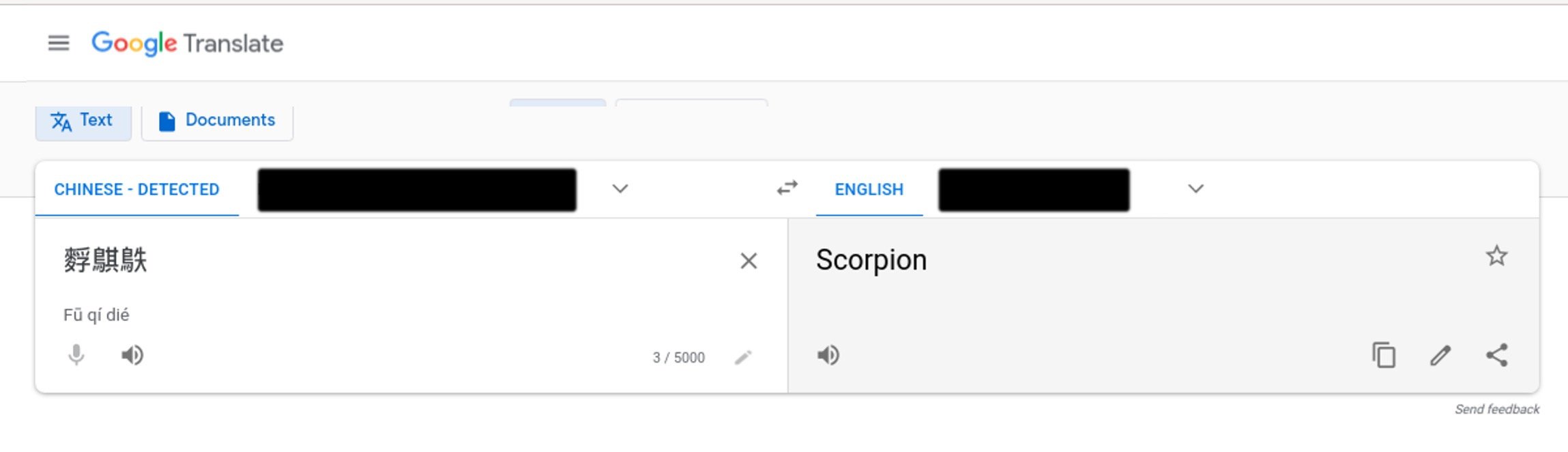
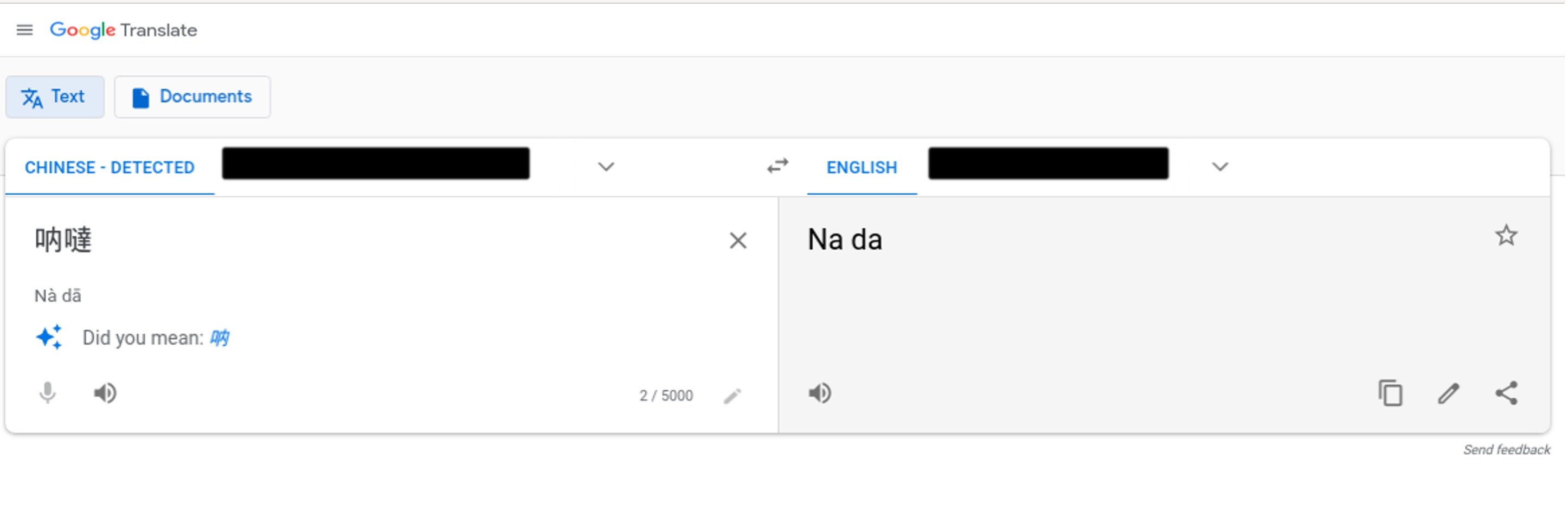
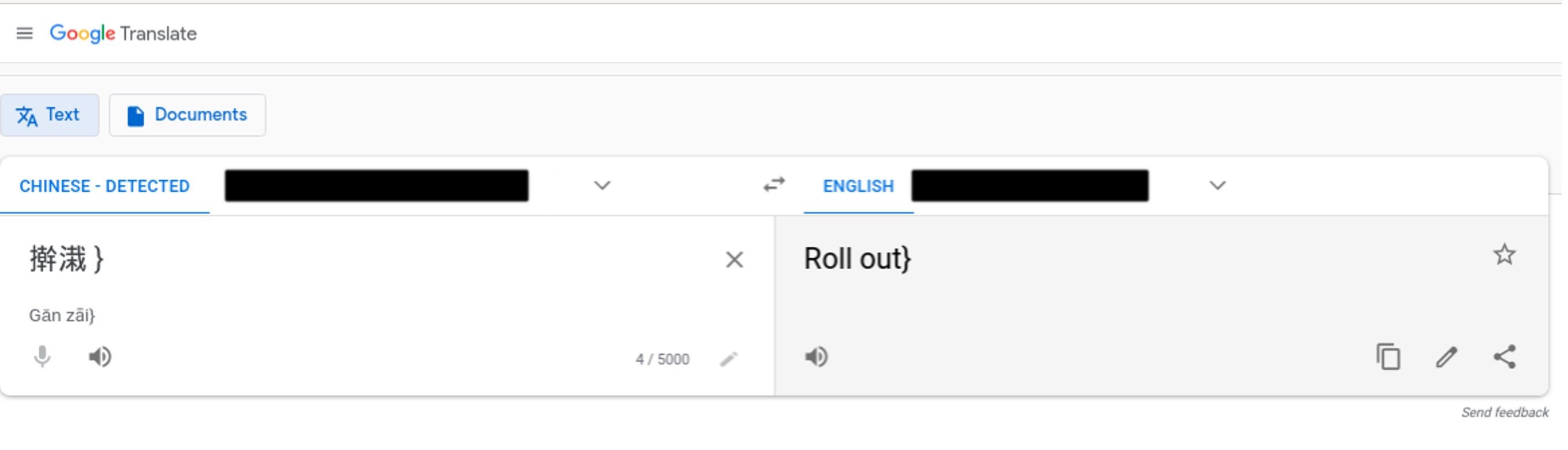
Initially, the symbols in the HTTP user agents seemed arbitrary and did not make any sense to us in isolation -- even after a rough translation.
But once we pieced together the symbols from several sequential user agent transactions, this unusual appearance in the HTTP user agents started to tell a more complete story. See the series of translations in Figure 8 below.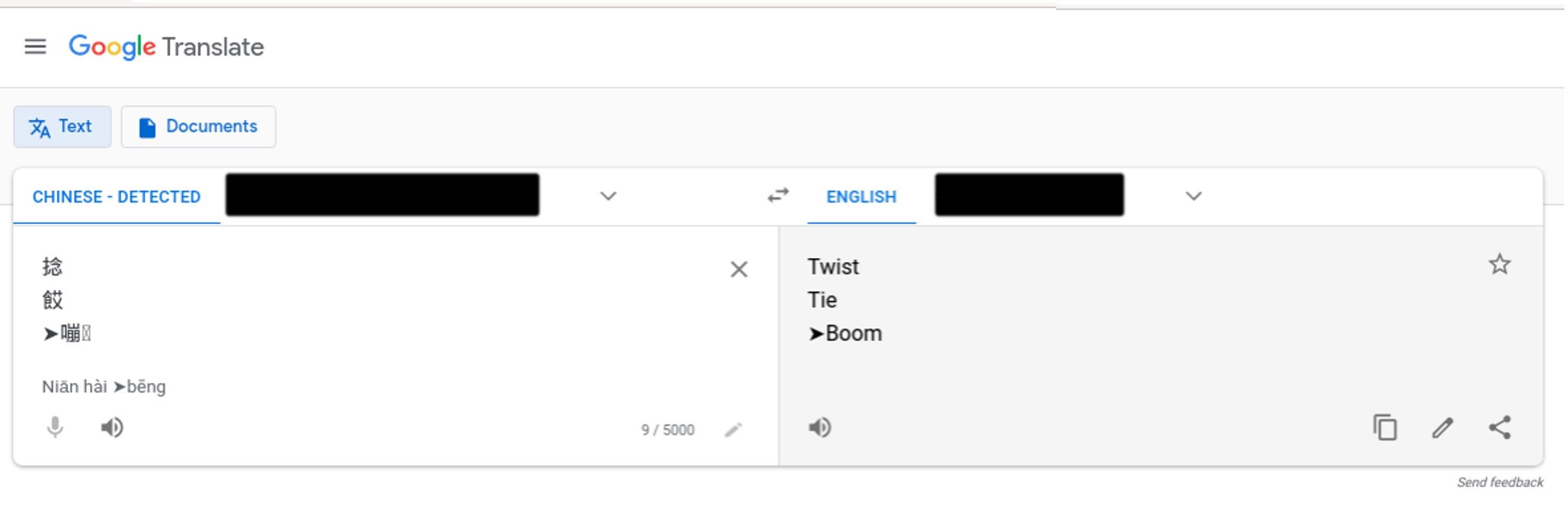
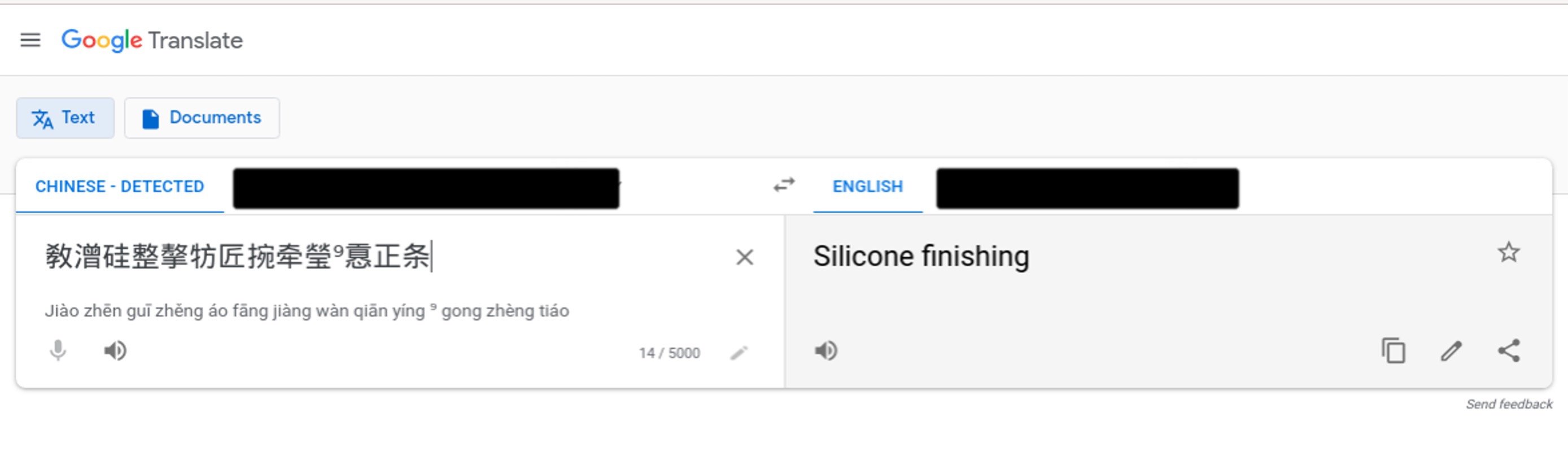 Figure 8. Sequence of translations from the symbols identified in the HTTP user agents.
Figure 8. Sequence of translations from the symbols identified in the HTTP user agents.
Legacy software system is implicated
We were able to isolate the internal sources of this unusual communication to a specific department (accounting) and group of staffers from within that department. Upon further investigation it turned out all these users were accessing the same legacy software system that appeared to be generating those communications.
Why this Matters
Based on these findings and other events uncovered, the priority of this incident was escalated and a formal investigation was launched. Unfortunately, because this is a sensitive issue and an ongoing investigation, we are not allowed to share further details at this point
Even if the story remains incomplete, we believe this example shows the power of the Clear NDR to correlate network flow data and security events and uncover an ongoing attack that had previously gone unnoticed by other security monitoring tools.
Ready to learn more?
Hopefully this gives you a taste of how the Clear NDR can help security teams know more, respond sooner, and mitigate the risk to their organizations. To request more information about how Clear NDR can help your organization or to schedule a live demonstration, please click on the link below to contact us.