SELKS 6 is out!
If you are still teleworking, you may wish to test and deploy this new edition to monitor the traffic in your home office. SELKS comes as a ready-to-use Suricata engine and web interface for management and data exploration.
SELKS is an open source project. As such, we would like to say a big “thank you” to all in our community for your support, your contributions, and your feedback!
Special thanks to github contributors:
- @ManuelFFF https://github.com/ManuelFFF
- @im-batman https://github.com/im-batman
- @Jeroen0494 https://github.com/Jeroen0494
What is SELKS
SELKS is a turnkey Suricata-based ecosystem with its own graphic rule manager and basic threat hunting capabilities. SELKS is a Debian-based live distribution built from 5 key open source components that comprise its name – Suricata, Elasticsearch, Logstash, Kibana and Stamus Scirius Community Edition (Suricata Management and Suricata Hunting). In addition, it includes components from Moloch and Evebox, which were added after the acronym was established.
SELKS gives you a Suricata intrusion detection and prevention (IDS/IPS) system within a network security monitoring (NSM) platform, Kibana to analyze alerts and events, EveBox to correlate flows, archive/comment on events, reporting and pcap download. Your user interface is the Scirius Community Edition which allows you to configure and manage the Suricata ruleset and perform basic threat hunting.
SELKS is released under GPLv3 license.
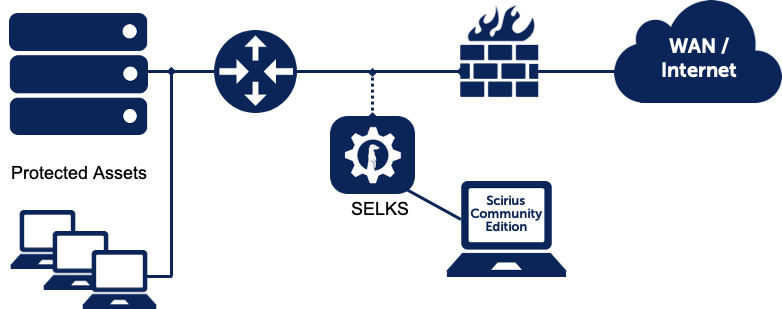
Figure 1. SELKS deployment example
SELKS is a showcase for the OISF Suricata project. Any and all data displayed on the tools and dashboard visualizations are generated entirely by the Suricata engine. SELKS users will find that the system can provide valuable insights from security events enriched by valuable metadata context contained in Suricata alerts and protocol event logging generated by Suricata. Indeed, the Suricata engine is an excellent foundation for a Network Detection and Response (NDR) solution, and SELKS provides an open source demonstration of that.
What’s new in SELKS 6
This latest edition of SELKS contains a number of new capabilities, including:
- New threat hunting interface. Improved new GUI with drill down and click-based filters based on Suricata alert data.
- New dashboard views. Twenty-six (26) new/upgraded Kibana dashboards and hundreds of visualizations that correlate alert events to network security monitoring (NSM) data and vice versa. Examples of the new dashboards include updates to application layer anomalies, alerts, TLS and JA3/JA3S views.
- Updated versions of each component. These include ELK stack (7.7.0), Suricata (6.0.0-dev), Debian (Buster), EveBox (1:0.11.1), Moloch (2.2.3), and Scirius Community Edition (3.5.0).
What follows is a short screenshot view of several new additions to threat hunting and Kibana dashboards functionality for events such as: alerts, TLS/JA3/JA3S logs, HTTP logs, anomalies detection and correlation.
New SELKS Hunting interface
The improved graphical “Suricata Hunting” user interface includes drill down and filter features that allow the user to quickly and easily navigate the Suricata alert data and protocol events.
As with earlier versions of SELKS, the “Suricata Management” interface includes ruleset management and administration or the Suricata sensor. With a single click, the user has access to all of the free and open rulesets available for Suricata.
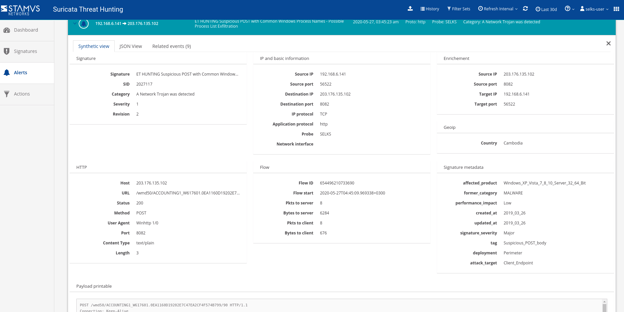
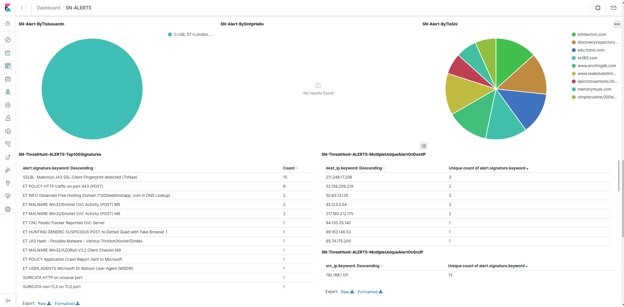
Overview of click search and filter functionality of Suricata alert events with metadata correlation
While Suricata alerts contain basic information such as alert payload, the real magic in these event records is the network metadata that is captured at the time of the event and used to enrich the basic security event. For example, an alert on HTTP protocol will also feature crucial meta-information such as:
- HTTP request and response body
- HTTP header fields such as User agents, URL, status code, method, content type, length etc..
- Flow information - packets, bytes, IP information, flow flags, time info
- File transfer info - filename, size, filetype, md5sums
Figure 2. SELKS "Suricata Hunting" examples
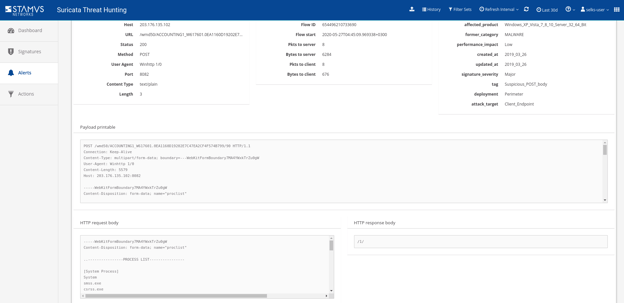
Figure 3. SELKS "Suricata Hunting" examples
But Suricata not only generates alerts. It also - by default - provides a detailed log of every protocol transaction. And by pivoting on the flow id, the analyst is able to gather more context about an alert event - and ultimately gain more insight into what’s really going on.
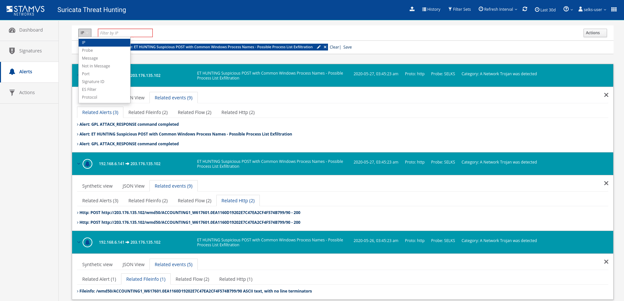
Figure 4. SELKS "Suricata Hunting" examples
In fact, this protocol logging and network security monitoring capability can provide the user with enough additional information that you can eliminate the need for a solution like Zeek for most protocols (in cases where no Zeek scripting is required).
The SELKS interface also comes with a number of ready-to-use Hunting filter sets (pre-defined by Stamus Networks) that you may apply to alert metadata that allow rapid focus on potentially meaningful events:
Figure 5. Pre-defined filter set examples
Of course, you can also create your own filter sets and share with the community :)
New and Updated Dashboards
SELKS 6 includes twenty-six (26) new or upgraded Kibana dashboards and hundreds of visualizations that correlate alert events to network security monitoring (NSM) data and vice versa. These are listed below:
- SN-ALERTS
- SN-ALL
- SN-ANOMALY
- SN-DHCP
- SN-DNP3
- SN-DNS
- SN-FILE-Transactions
- SN-FLOW
- SN-HTTP
- SN-IDS
- SN-IKEv2
- SN-KRB5
- SN-NFS
- SN-OVERVIEW
- SN-RDP
- SN-RFB
- SN-SIP
- SN-SMB
- SN-SMTP
- SN-SNMP
- SN-SSH
- SN-STATS
- SN-TFTP
- SN-TLS
- SN-TrafficID
- SN-VLAN
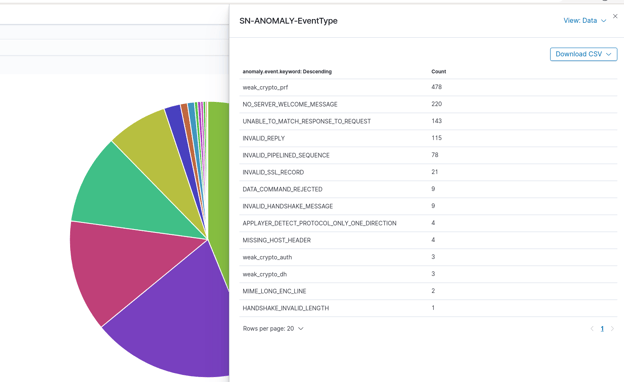
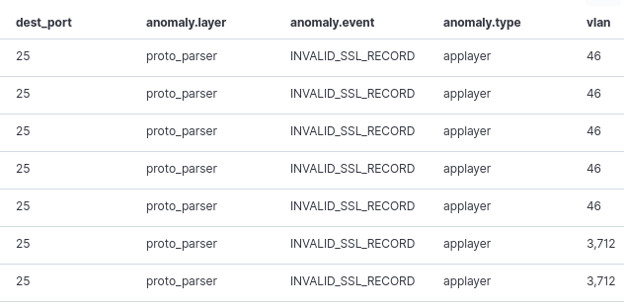
SELKS 6 is built on the most-recent available version Suricata, and it benefits from one of its newest features -- application layer anomalies. This capability allows SELKS to detect and expose application layer anomalies without using an IDS signature:
Figures 6 and 7. Suricata anomaly event type
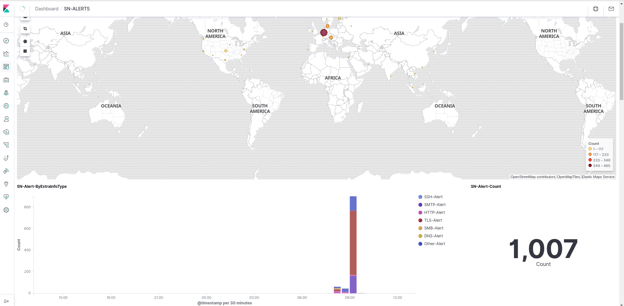
Below you can see the new SELKS alert dashboard:
Figure 8. SELKS alert dashboard.
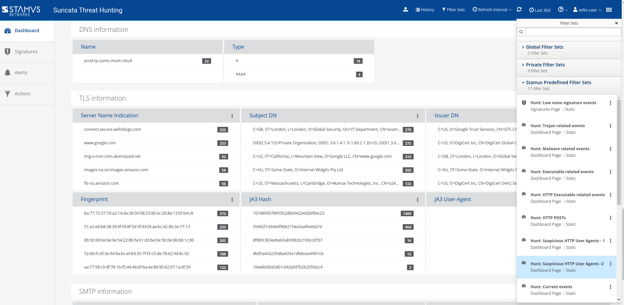
TLS Protocol Capture
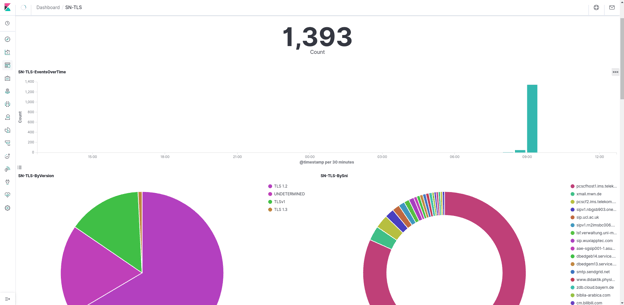
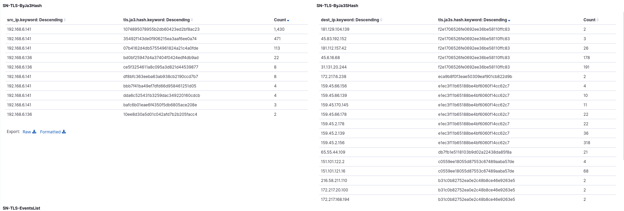
Because Suricata includes extensive network security monitoring (NSM) capability, it can log and document TLS (and many other) events on the network.
Figures 9 and 10. TLS protocol display.
JA3/JA3S
Suricata can by default analyze and produce JA3/JA3S records on encrypted traffic which makes it possible to effectively hunt even within encrypted traffic.
Figure 11. JA3/JA3S record display.
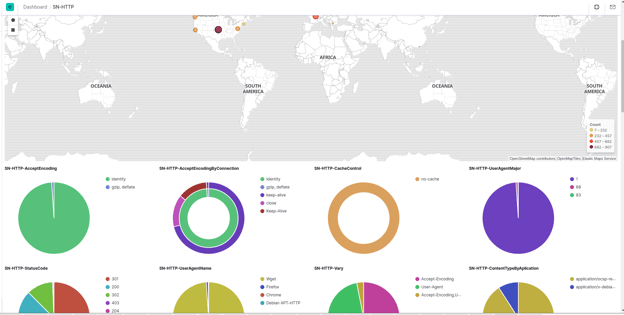
Here is an example of how SELKS displays HTTP protocol info, broken down by events, user agents etc.
Figures 12. HTTP protocol information display.
Updates to Underlying Components
In addition to all the functionality upgrades listed above, SELKS 6 contains updated versions of each component. These include ELK stack (7.7.0), Suricata (6.0.0-dev), Debian (Buster), EveBox (1:0.11.1), Moloch (2.2.3), and Scirius Community Edition (3.5.0).
Threat Hunting Webinar
If you are interested to learn more about threat hunting with encrypted traffic using Suricata/SELKS, we recommend you check out this recent (May 2020) OISF webinar, entitled “Suricata Threat hunting with encrypted traffic”: https://www.youtube.com/watch?v=3GcIfJI0ygg
Download
Visit this SELKS webpage to download SELKS 6, pick one of the two flavors:
SELKS with desktop
Sha256sum: 1d901e039d79748aa2781ff9d19f2265cb47aef504f099dbdac8d8f40ebc44cb
SELKS without desktop
Sha256sum: 23c160ea5d16586fb07d23b32d01b645f7d5d77083245b68a9138e0f088491d8
Usage
You can find the first time setup instructions on our SELKS 6.0 wiki page.
SELKS 5 users can upgrade their running systems using the following Upgrade instructions.
Feedback is Welcome
As always, we would greatly appreciate any feedback you might have. :)
Give us feedback and get help on:
- Freenode IRC on the #SELKS channel
- Google Mailing list
While this test upgrade/installation has been verified and tested, please be sure you try it in your test/QA set up before deploying in a production environment.
Thank you!