For all Suricata’s capabilities, building out an enterprise-scale deployment of Suricata with mostly open source tools can be a challenge.
In this second entry in the series of blog posts, we review another one of the five ways to improve the scalability of Suricata in an enterprise deployment - Centralizing Suricata Sensor Management.
Note: for a more complete review of all five improvements, please check out the white paper, Scaling Suricata for Enterprise Deployment. You can download your copy here >>
Centralize Suricata Sensor Management
While Suricata sensors are capable of running extensive signature rulesets, network traffic analysis, and reputation/match lists, each sensor in your enterprise may require different hardware and software configurations based on their network performance requirements and where they are deployed. And you will want to understand how these are performing relative to your expectations.
For example, you may deploy lower performance sensor hardware in your branch office running a subset of your detection rules while you deploy a much higher performance appliance in your datacenter running a complete commercial ruleset and the latest IP and DNS threat intelligence lists. In an enterprise deployment, you may have hundreds of sensors and dozens of different configurations. This presents several challenges for the enterprise.
- How to make sure rules, threat intelligence and data capture is properly deployed and up to date on every sensor
- How to monitor the performance of each sensor to ensure it is processing every packet and every rule, so you won’t miss critical events
- How to maintain backup configurations for each sensor so you can quickly replace a sensor in the event of a hardware failure or revert to a previous known state
- How to upgrade and patch the software on your fleet of sensors
- How to keep track of the inventory of various sensors and configurations
As your deployment requirements grow and the Suricata capabilities continue to evolve, the above challenges are amplified. Logging into individual sensors (or SELKS user interfaces) one-at-a-time to monitor and make changes is simply not practical.
In order to address these challenges at an enterprise scale, you will want to install a centralized sensor management system.
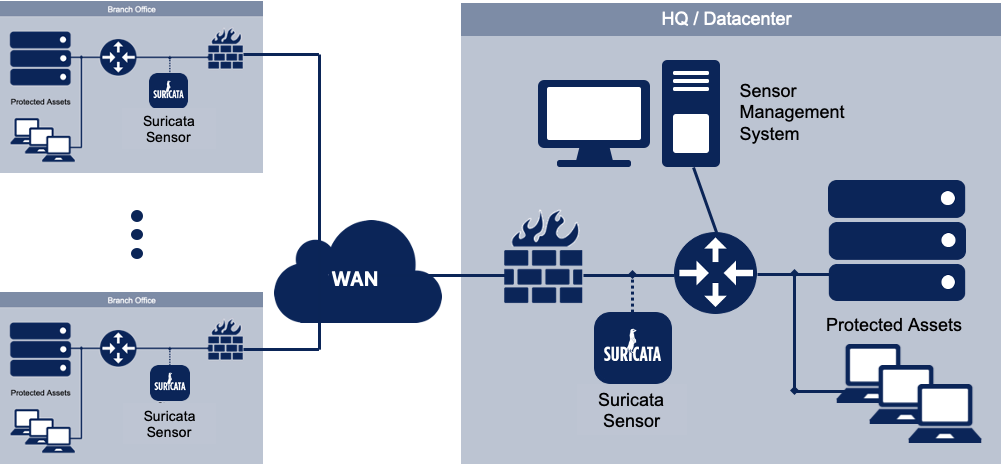
Figure 1. Sample architecture of a Suricata deployment
The options for a centralized management system include in-house development, open-source and commercial solutions.
The advantages of in-house development include the flexibility to include any and all features required for your enterprise and zero out-of-pocket expense. Of course, the challenges include securing the resources needed to develop the sensor management system and having access to those resources for support and continuous improvement. And there are indirect opportunity costs associated with consuming those resources when they could be used to develop other systems.
The advantages of deploying an open source solution are similar to those of an in-house developed system in that there is typically zero out-of-pocket expenses and you will preserve the flexibility of making customizations in the future. The biggest disadvantage to open source solutions is that your team is 100% responsible for support. We have spent time researching this problem and have unfortunately not found a reasonable open source solution for this problem. If you know of any, please let us know and we will update this blog.
Finally, there are several commercially available solutions for sensor management, including Stamus Security Platform from Stamus Networks. Solutions such as Stamus Security Platform include IDS ruleset and match list management, network sensor administration (both native Suricata sensors and Stamus Network Probes), application and OS updates, and a RESTful API for integrating with your security stack. The advantages of a commercial solution include dedicated ongoing support and a roadmap of continuous product improvements.
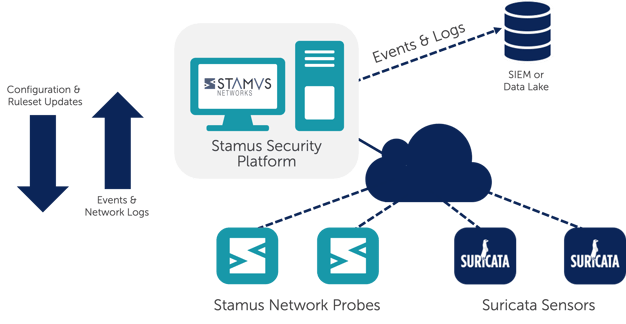
Figure 2. Stamus ND from Stamus Networks
Other Articles in the Series on Scaling Suricata
In an earlier blog article we reviewed ways to optimize your sensor placement. Future blog articles will cover the additional three considerations that can help you improve the scalability of Suricata in your enterprise. Here’s the complete list of articles:
- Optimizing sensor placement
- Deploying centralized sensor management (this article)
- Tune the network of sensors for maximum performance
- Consolidate Suricata alerts and logs from multiple sensors
- Deploy high-level analytics to focus analysts’ time on the the things that matter
Additional Suricata Resources
If you are interested in exploring this topic further, we recommend the following resources:
- Suricata website
- OISF website
- SELKS web page
- SELKS github page
- Just released: Suricata 6 (blog article)
- Suricata dashboards for any ELK stack (open source contribution by Stamus Networks)
- Grafana dashboards for SELKS (open source contribution)
- Suricata user forum
- Strategic Sensor Placement for Intrusion Detection in Network-Based IDS (academic paper)
- Suricata Extreme Performance Tuning (SEPTun) guide - Part 1
- Suricata Extreme Performance Tuning guide - Mark II
- Official Suricata training resources
- Comparing SELKS and Scirius Security Platform (white paper)
- 11 Open Source SIEM Tools (article)
- Splunk enterprise security solutions
- Introducing the Stamus Networks App for Splunk (blog article)
- Stamus Security Platform(web page)







