After a very valuable round of testing and feedback from the community we are pleased to announce the SELKS 4 RC1 availability.
SELKS is both Live and installable Network Security Management ISO based on Debian implementing and focusing on a complete and ready to use Suricata IDS/IPS ecosystem with its own graphic rule manager. Stamus Networks is a proud member of the Open Source community and SELKS is released under GPLv3 license.
This is a the release candidate of a new major branch with an updated storage visualization stack and latest Suricata.
New Features
- Suricata IDS/IPS/NSM 4.0.x - latest git master Suricata packaged with Hyperscan enabled for extra performance boost. This edition of Suricata besides many improvements and bug fixes also includes extra alert data like for example http body added to the alert json logs wherever available.
- Elasticsearch 5.5.0 - part of the ELK5 stack upgrade making available a ton of new features and enhancements.
- Logstash 5.5.0 - performance improvement over 2.x and ES5 compatibility.
- Kibana 5.5.0 - taking advantage of the latest dashboarding features of ES.
- Scirius 1.2.2 - bugfixes, better correlation capability with EveBox and introduction of IPS rules support.
- Evebox - many new features including reporting and comments on the log events.
- Debian Stretch - All new features, kernel and tools.
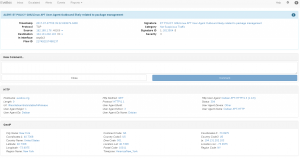
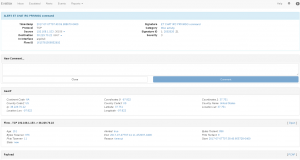
Alert event with a comment field.
Download
To download SELKS4-RC1:
Usage
Usage and logon credentials (OS and web management user)
- user:
selks-user - password:
selks-user(password in Live mode islive)
The default root password is StamusNetworks
To remotely access the web management interface :
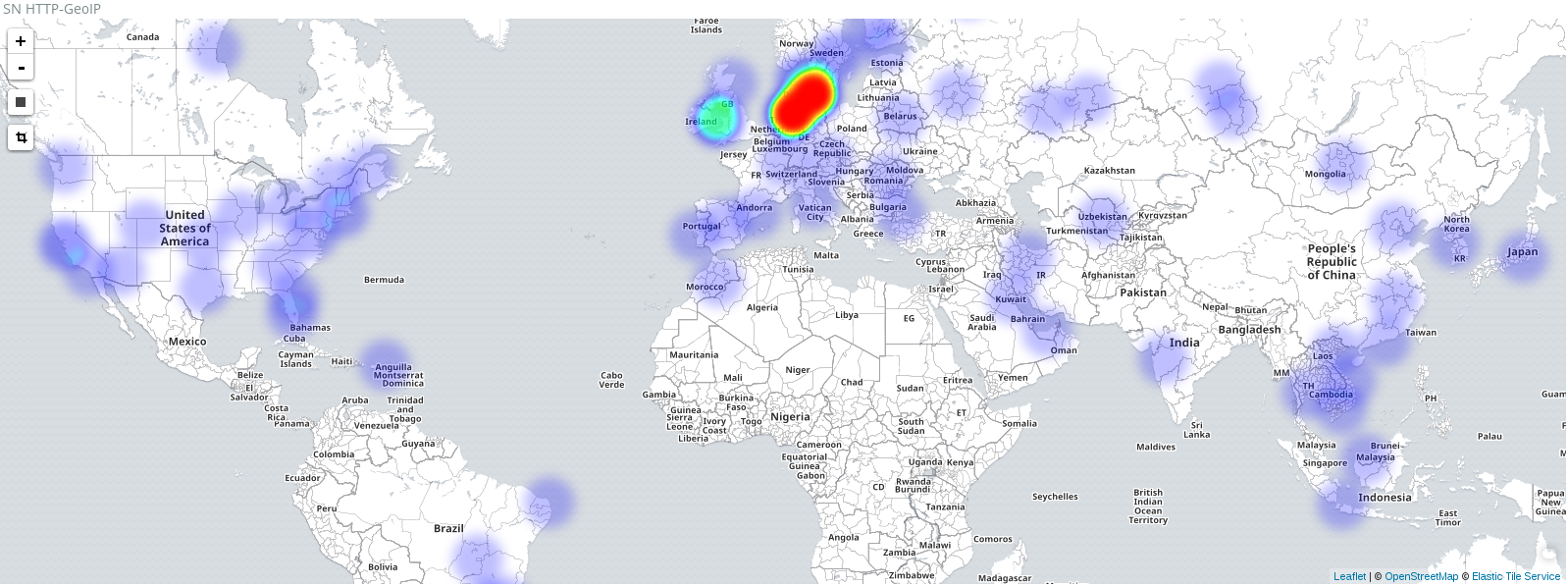
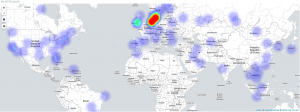
- https://your.selks.IP.here/ - Scirius ruleset management and a central point for all dashboards and EveBox alert and event management.
Howto
Upgrade
To upgrade your existing SELKS 3 to SELKS 4 preview, please refer to SELKS-3.0-to-SELKS-4.0-upgrades wiki page.
It is recommended to follow the onscreen instructions and if needed answer "yes" to all changes. At the end of the upgrade you will be asked to enter the interface that you will use for IDS/sniffing. Please enter (eth0 for example) the interface name and reboot when the script is done.
Create your own ISO
To create your own SELKS 4 preview ISO (if your host OS is Jessie):
git clone https://github.com/StamusNetworks/SELKS.git
git checkout SELKS4-dev
./install-deps.sh
cd /usr/share/live/build/data/debian-cd/ && ln -s squeeze stretch
./build-debian-live.sh
It will take probably 30-40 min and you should end up with the SELKS.iso under the Stamus-Live-Build folder.
Once installed/upgraded
- Please feel free to choose the IDS sniffing/listening interface either via the desktop icon Setup-IDS-Interface or via the cmd calling /opt/selks/Scripts/Setup/setup-selks-ids-interface.sh
- Any further upgrades are done via a wrapper script located in /opt/selks/Scripts/Setup/selks-upgrade_stamus.sh
- Recommended set up for SELKS 4.0RC1 is 2CPUs 5-6Gb RAM
- If you need to reset/reload all the dashboards - you can do like so
- In Scirius on the top left corner drop down menu select System Settings
- click on the Kibana tab
- choose Reset SN dashboards
Feedback is welcome
Give us feedback and get help on:
- Freenode IRC on the #SELKS channel
- Google Mailing list
While this test upgrade/installation has been verified and tested and aims at upgrading your current SELKS 3.0 to SELKS 4.0RC1 please make sure you try it in your test/QA set up first and give us any feedback.
Thank you!