A Turnkey Suricata-based Network Detection and Response System
As the next generation open source turnkey Suricata implementation from Stamus Networks, the Clear NDR - Community edition is the successor to SELKS. We incorporated many lessons learned from the 10 years of SELKS innovation and user feedback into this platform.
Wondering why we made the change from SELKS to Clear NDR? Check out the FAQ here >>
Released under GPL 3.0-or-later license, the distribution is available as either via Docker compose on any Linux operating system or as an installable Debian-based ISO (coming soon).
The Clear NDR - Community user interface (also known as Scirius) is the Stamus Networks open-source application that brings all these components together. It provides the web interface for the entire system, giving you the ability to:
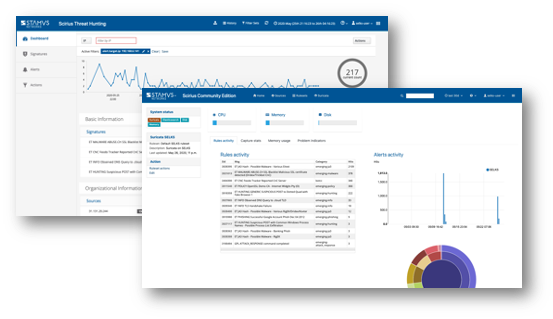
For many small-to-medium sized organizations, Clear NDR - Community can be a suitable production-grade network security monitoring (NSM) and intrusion detection (IDS) solution.
And because all the data available in Clear NDR - Community is generated by the Suricata engine, Clear NDR - Community is widely used by network security practitioners, researchers, educators, students, and hobbyists to explore what is possible with Suricata IDS/IPS/NSM and the network protocol monitoring logs and alerts it produces.
For enterprise scale applications, please review our commercial solution, Clear NDR - Enterprise, described below.
Use the image with Desktop when you want a turnkey installation that includes the Debian x64 12 (Bookworm) Linux desktop environment. Can be deployed on bare metal hardware or VM
Use the image without Desktop when you want a turnkey Clear NDR - Community installation in a headless environment (based on Debian x64 12 Bookworm). Can be deployed on bare metal hardware or VM.
To access README documentation, issues tracker and the Clear NDR - Community components, please visit our GitHub pages here:
Visit the documentation site for complete installation instructions, here >>
To ask questions or ask for help, join our Discord server here >> %20PNG-1.png?width=50&name=Discord%20Logo%20(black)%20PNG-1.png)
While Clear NDR - Community is a great system to test out the power of Suricata for intrusion detection and threat hunting, it was never designed to be deployed in an enterprise setting. For enterprise applications, please review our commercial solution, Clear NDR - Enterprise (formerly Stamus Security Platform).
To learn more about the differences between Clear NDR - Community and our commercial solutions, download the white paper, Understanding SELKS and Stamus Commercial Platform.


ABOUT STAMUS NETWORKS ™
Stamus Networks believes that cyber defense is bigger than any single person, platform, company, or technology. That’s why we leverage the power of community to deliver the next generation of open and transparent network defense. Trusted by security teams at the world’s most targeted organizations, our flagship offering – Clear NDR™ – empowers cyber defenders to uncover and stop serious threats and unauthorized network activity before they harm their organizations. Clear NDR helps defenders see more clearly and act more confidently through detection they can trust with results they can explain.
© 2014-2025 Stamus Networks, Inc. All rights Reserved.