Today we announced the general availability of Scirius Threat Radar (now called Stamus NDR), a powerful addition to our product line that provides a threat-based approach that delivers response-ready insights and a number of capabilities to help security teams know more, respond sooner, and mitigate the risk to their organizations.
And while we are on a lifetime quest to improve the efficacy of and reduce costs associated with cybersecurity through network detection and response (NDR) solutions, we are taking a moment this month to reflect on the early chapters (see first blog in the series) and proudly acknowledge the exciting chapter we just opened this week.
Recap of Chapters 1-4
Last week’s blog introduced the first chapters of our quest:
Chapter 1: A Better IDS/IPS.
Chapter 2: Enrichment
Chapter 3: Addressing Alert Fatigue.
Chapter 4: Focus on the Host.
For more details about these previous chapters, please see this blog post.
Chapter 5 - Radar Love
This week, we at Stamus Networks are proud to formally introduce Scirius Threat Radar, opening a new chapter in our quest. With this addition to the product portfolio, we further address the complexity and cost of implementing a network detection and response process. And in doing so, we aim to help enterprise security teams more cost-effectively mitigate risk.
Stamus NDR introduces 3 new important capabilities:
- Advanced threat detection - Inspects all network activity and threat alerts to cut through the noise and automatically identify the critical active threats targeting your assets. This dramatically reduces the number of potential incidents that your team must investigate.
- Asset-oriented attack insights - Shifts the focus from millions of indicators of compromise to a handful of compromised assets. Groups those assets-under-attack by phases of the cyber kill chain to help analysts prioritize their investigations.
- Custom threat definitions - Empowers expert analysts to create organization-specific threat definitions and apply it to both historic and future network traffic. This improves detection, speeds response and strengthens the contribution of less-experienced analysts.
The new capabilities completely redefine the network cyber threat hunting process from a traditional alert-driven model to an asset-centric approach, allowing the analyst to more clearly understand the threat impact and accelerate incident response.
Advanced threat detection
Some Stamus NDR deployments capture millions of threat alerts every day. While the combination of classification and related metadata is very effective at reducing the volume of alerts, we wanted to do better.
With Stamus NDR, users get high-level threat algorithms developed by the Stamus Networks threat research team and the opportunity to develop custom threat definitions. Stamus NDR automatically applies these algorithms to all network activity and high-probability threat alerts to spot critical threat activity targeting your assets.
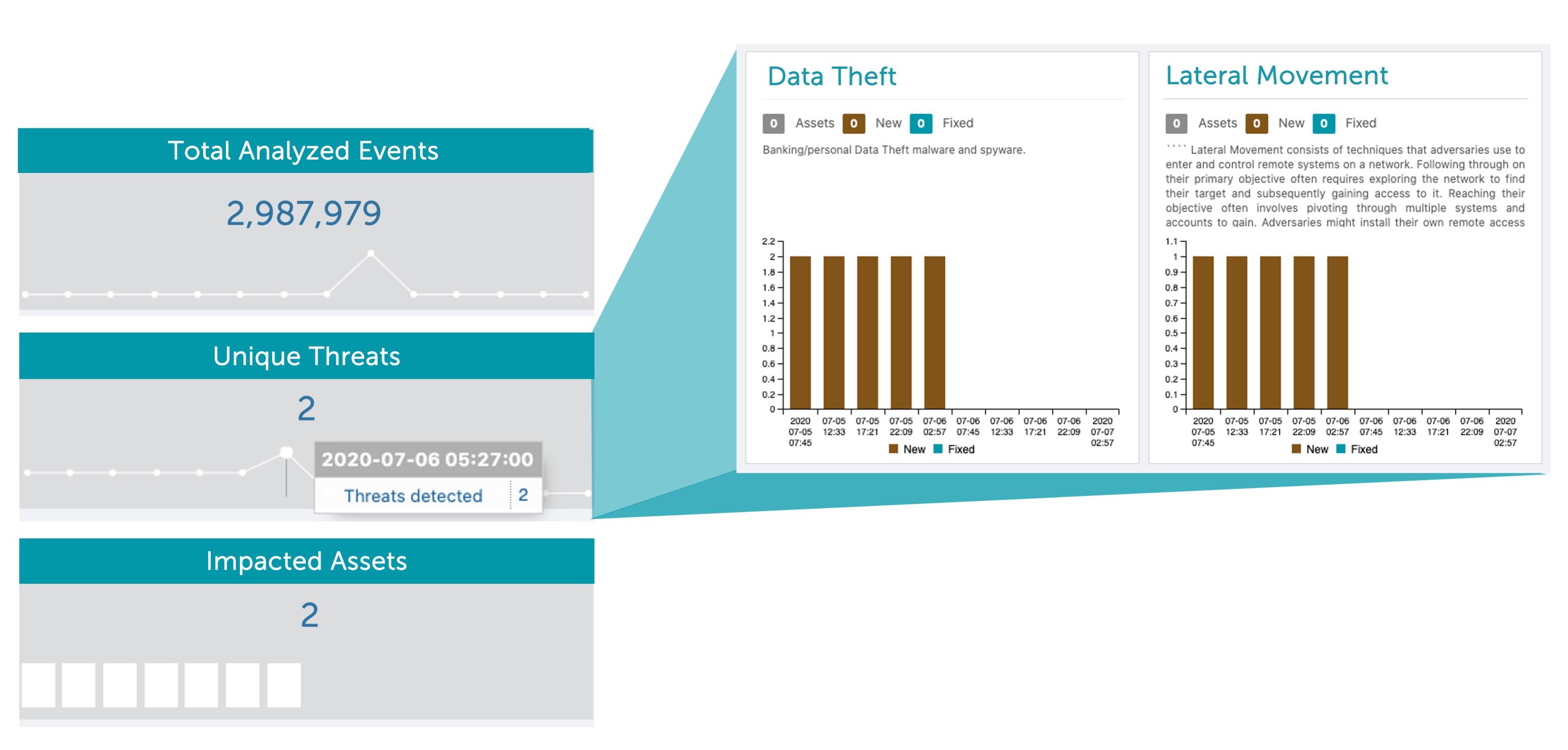
This new layer of threat detection saves users time and allows them to quickly identify the impacted assets, know when they were impacted, and take corrective actions.
Asset-oriented attack insights
The advanced threat definitions allow Stamus NDR to identify all the hosts/assets that are impacted by each threat. Just as importantly, it associates each asset/host being attacked with the relevant phase of the cyber kill chain.
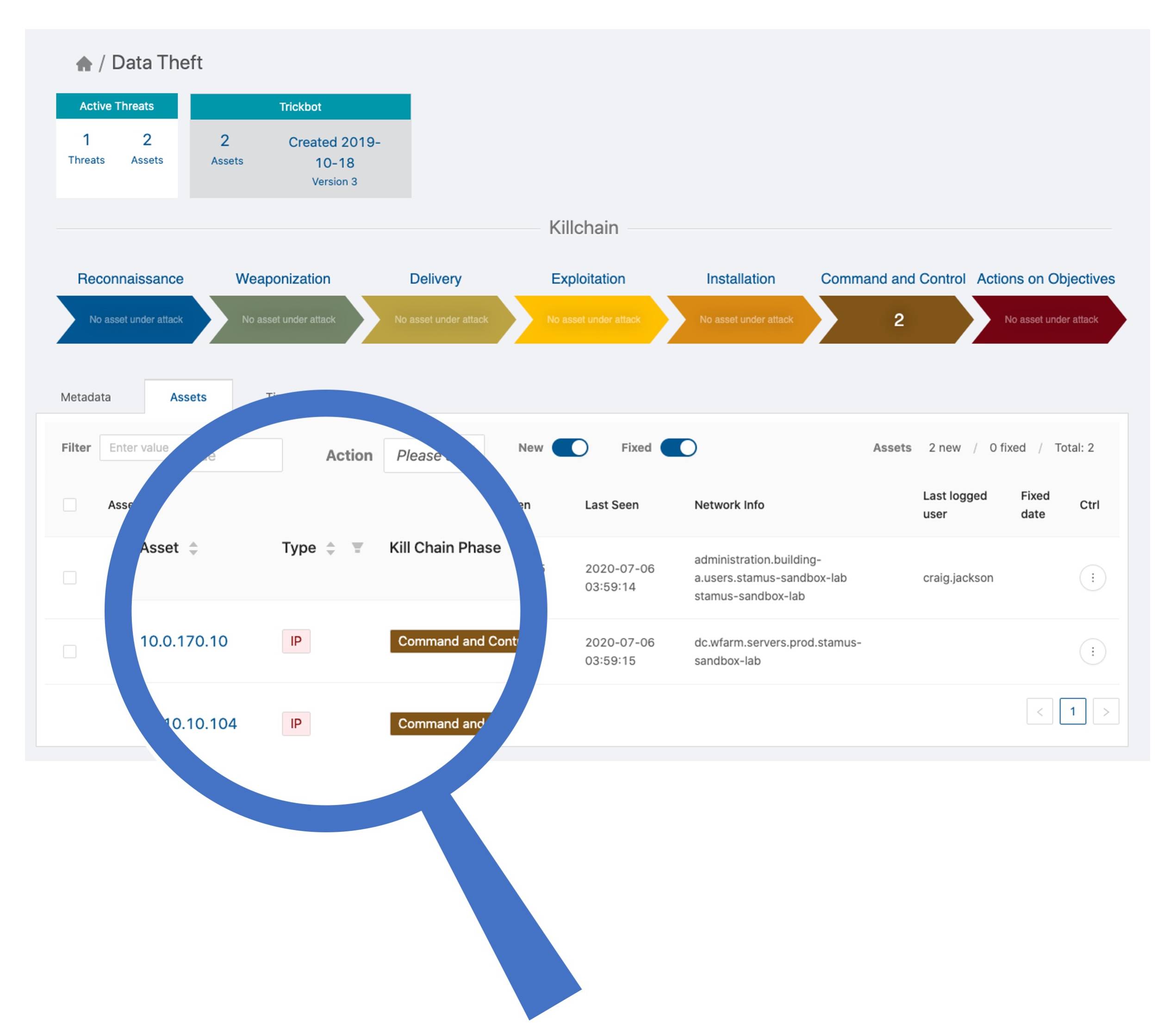
This mapping allows the analyst to prioritize their review of hosts that are, for example, under attack in the “command and control” phase before those which appear earlier in the kill chain such as the “delivery” phase. And by shifting the investigation approach from one that is alert-centric to Scirius Threat Radar’s asset-centric approach, the analyst can more clearly understand the potential impact of the threat and accelerate incident response.
Custom threat definitions
Even a modern well-researched generic threat detection system can not cover the needs of every organization. That’s why we built in a mechanism for users to easily transform data filters they create while threat hunting into custom threat definitions for Stamus NDR. These new threat definitions can be applied to both historic and future data.
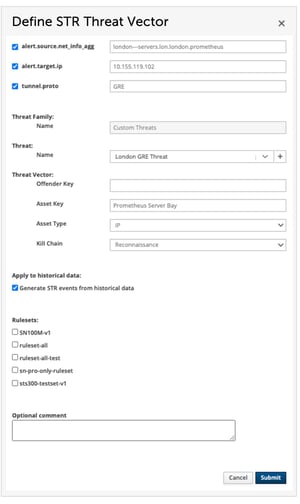
By applying the custom threat definitions to historical data, the analyst will uncover assets under attack that should be investigated by the team. And when applied to future data, this threat definition allows the analysts to follow the threat activity over time.
This feature is another great way for Tier 3 analysts to empower Tier 1 analysts. Once a Tier 3 analyst has created these custom threat definitions in the Stamus Security Platform, the Tier 1 analyst is able to more quickly assess the organization’s threat posture.
Solid foundation
It is critical to build the foundation of any network detection and response system on the best and most up-to-date threat intelligence. So, while you will always have the option to deploy additional rulesets and develop and deploy your own signatures, all users of Stamus NDR also receive a fully automated subscription to the highly-respected Proofpoint ETPro ruleset.
Learn More
With this edition to the product line, organizations can further reduce the complexity and cost of implementing a network detection and response process. Stamus NDR helps security teams know more, respond sooner, and mitigate the risk to their organizations.
As we continue our quest, you can expect new chapters soon. Follow along as we incorporate new technologies and develop tools to improve threat detection, enable more effective hunting, reduce the time for incident response, and ultimately, help you mitigate risk to your organization.
Want to see Stamus NDR in action? Start with this short video demonstration
Visit the Stamus NDR page here >>>
And download the Stamus NDR datasheet to learn more:








