Stamus Networks is proud to announce the availability of Scirius Community Edition 2.0. This is the first release of the 2.0 branch that features a brand new user interface and new features such as lateral movement and target transformations. Both modify signatures to improve them. Lateral movement uses an algorithm to enlarge the signature IP address filter to detect attacks in the internal networks. Target transformation implement an other algorithm to add target keyword to signatures thus helping to find and visualize attack paths.
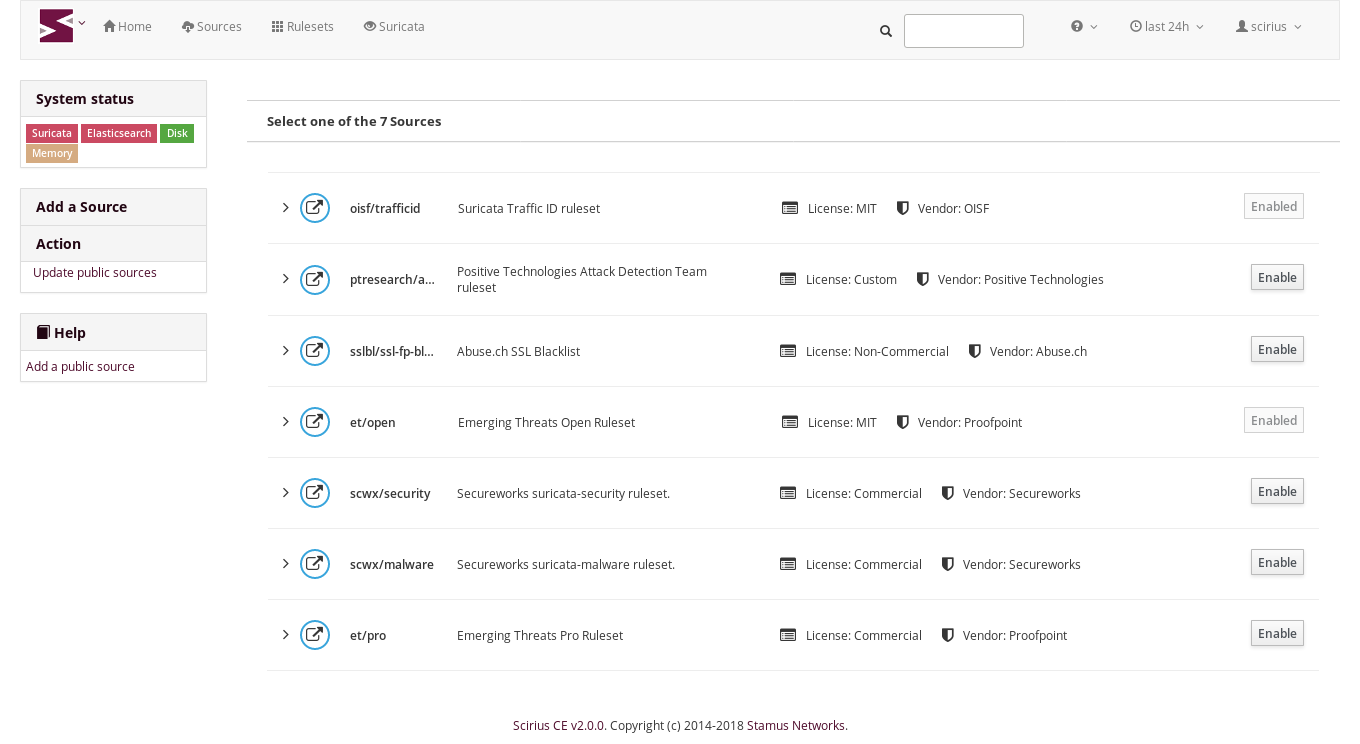
Scirius 2.0.0 now features an automated addition of any of the sources defined in the public ruleset list published by the OISF:
So you can now add to your ruleset a new feed/source in two clicks. That's really easier compared to the form based method where a series of fields as to be entered. The addition process itself is also faster. The parsing and update time of a ruleset like ET Pro has been improved to be three times faster in this version.
As you may have noticed, Scirius 2.0.0 interface is really different from one from the previous versions:
Scirius is now using the Patternfly framework to provide a consistent interface and usability oriented components. Usability has also been improved by the integration of the documentation in the interface.
On Suricata related side, the most important change is the handling of transformations. Scirius can now modify the signatures through a transformation:
Currently two transformations are available and they aim at making Suricata's detection capabilities stronger:
Lateral Movement
Lateral movement transformation modifies signatures to have them detect lateral movement. As signatures are often written with the EXTERNAL_NET and HOME_NET variables, this means they won’t match if both sides of a flow are in the HOME_NET. Thus, lateral movements are not detected. This transformation changes EXTERNAL_NET to any to be able to detect lateral movements. Scirius propose per ruleset, per categories and per signature changes. One of the value proposed is auto that use an algorithm that trigger the substitution if the signature verifies some properties.
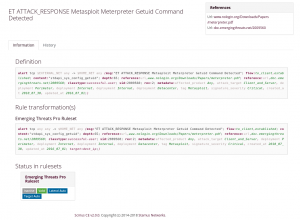
Target Keyword
The second substitution is the addition of the target keyword donated by Stamus Networks. Available since Suricata 4.0, the target keyword can be used to tell which side of a flow triggering a signature is the target. If this key is present then related events are enhanced to contain the source and target of the attack. Once more the user can choose the value of the option or let Scirius determine what side to use via an algorithm using signature properties.
For the eye candy fans, pktcity is now part of Scirius. This 3D webGL visualization interface is now available as part of the new dashboards: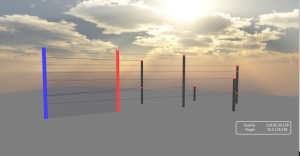
Finally, for the list addicts, here is Scirius 2.0.0 changelog:
- Rule transformation with lateral movement and target
- Support of OISF public sources for easier setup
- Convert documentation to sphinx and integrate it in interface
- Rework of interface with Patternfly components
- Link to Onyphe to get IP informations
- Rules parsing optimization
- More dashboards including pktcity webGL visualization
- Initial REST API to interact with Scirius from outside
Scirius 2.0.0 is available on github. Debian packages for SELKS are also available. Users of Scirius Enterprise Edition will get access to this feature in the upcoming 29 release.