Stamus Networks team is proud to announce the availability of Scirius 1.1. This new release brings a ton of new features:
- Easier enabling/disabling of rules and categories
- Delete events from Elasticsearch corresponding to all alerts of a given rule
- Compatibility with Kibana 4
- Add a graphic presenting Logstash insertion speed
- Graphics with Suricata performance indicators
- Greatly improved source addition
- Preliminary support for Sourcefire ruleset
- Validity checking of ruleset, imported sources and rules
One of the main new feature is the validity checking system. Scirius is now able to test whether a rule, a source or a ruleset will be valid for Suricata. This is not a simulated test as Scirius is using the configuration testing capability of Suricata to get the information.
One of the updated page is the the rule details page. It does now contain the validity of this rule respectively to the existing rulesets: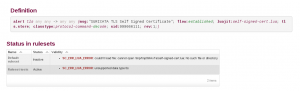
In our example, the rule is invalid for first ruleset because the source containing the lua script is not active in the ruleset. In the second ruleset, the rules is not valid because the Suricata on the system is not supporting the not-yet-official(as of the moment of this writing) TLS extension for lua scripting. As you can see, the validity checking system is much more than a simple parsing and gives you a real view on the validity of rules on your own system. This system will work with any Suricata but it will give accurate information if the system is hosting the latest Suricata. This is due to the fact that Scirius is parsing the JSON console output of Suricata which has been added recently to the Suricata git master. Our team has packaged the latest Suricata and made it available in Stamus Networks repository to the users to give them the best of this new feature.
This testing system has been used to revamp the Source addition. Adding a source to an existing ruleset was complicated and involving multiple steps. Now, user can select to which rulesets a new source should be added when creating the source. So there is now basically one step: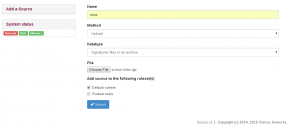
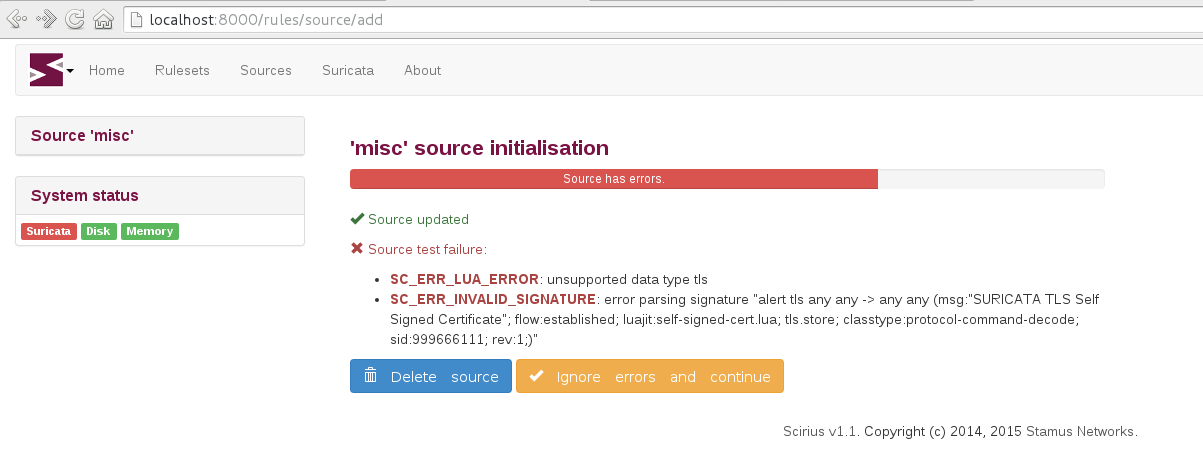
The validity checking system will warn the user about a possible problem during the source creation: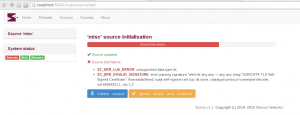
As some rulesets may contain invalid signatures, user has the capability to choose whether or not he/she wants to ignore the detected problems.
The second main change in Scirius is its ability to graph some performance indicators. It is using the logstash metrics capability to get statistics on the insertion speed. This is a good indicator of the load of your logging system.
The second set of graphics is building performance indicators for Suricata. The Suricata page of Scirius is now able to graph:
- Capture stats
- Memory usage
- Problem indicators
If capture stats is showing the usual drop and accept, the two others tabs are more interesting as they are showing the memory consumption of Suricata subsystem succh as TCP, Flow, DNS and HTTP protocols: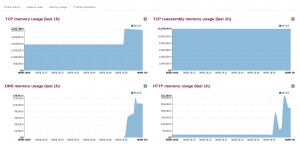
The third tab is showing some Suricata indicators that can help to diagnose problem. All these indicators are extracted from Suricata statistics output in JSON format that will be part of Suricata 2.1.
Happy SELKS users can simply run apt-get update && apt-get dist-upgrade to get new version. Others can get it from Github.