Introduction
SELKS 1.0 is featuring a privacy dashboard. This is a dashboard focusing on HTTP and TLS protocols. The used data source is events generated by Suricata for these two protocols. The goal of this dashboard is to show the different interaction between website. For example, you will see on the following video that opening elysee.fr which is the French president website is triggering the opening of page on Facebook and Google Analytics. This means that both Facebook and Google knows you've went to the presidential website.
Setup
The setup of the demonstration is simple as we are connecting to the web on the virtual machine. This has been done because it was easier to record the screencast in that case. But the most interesting setup consists in sniffing the traffic of the physical host from SELKS running on the virtual machine. This way, SELKS will analyse your local traffic and you will be able to see in SELKS all the events coming from your real internet life.
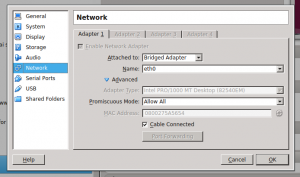
The setup is simple. In Virtualbox, go to the machine details and click on network. Then choose to bridge your physical network interface and allow promiscuous mode on the interface:
Demonstration
Watch the following video to discover how this dashboard can be used:
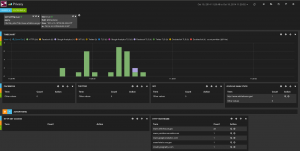
An other way to use this privacy dashboard is to use one of the filter. For instance, if we filter on http.http_refer:"http://www.whitehouse.gov" we get a dashboard containing all HTTP events with a referrer being the US president website. So if you look at the hostname on the following screenshot, you will see that going on whitehouse.gov also lead you to external websites
My favorite in this list is www.youtube-nocookie.com but something like cloud.typography.com is really interesting too. Even a website like whitehouse.gov is not anymore hosting is own fonts.
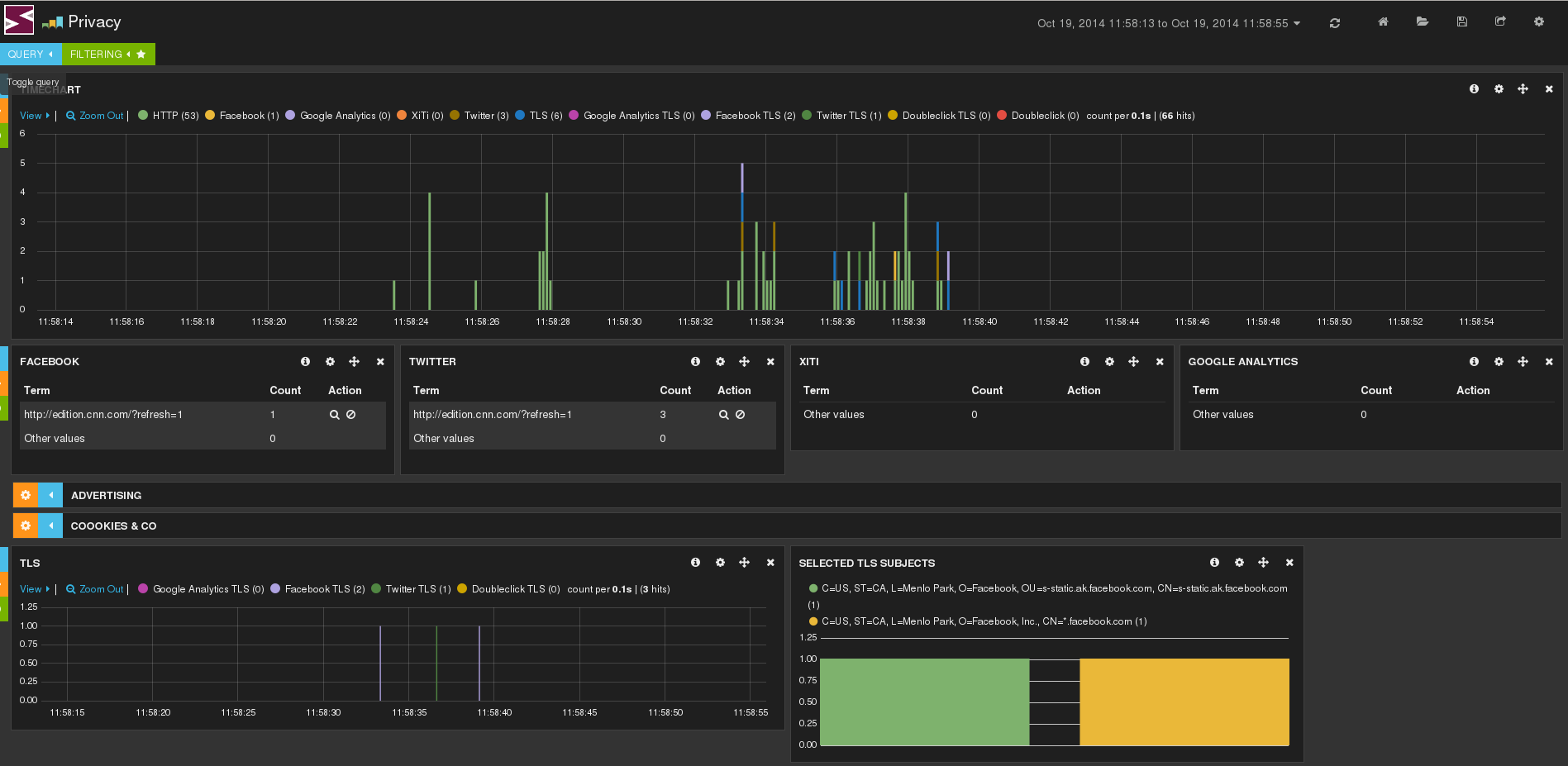
The privacy dashboard is also containing TLS information extracted by Suricata. It lists TLS connections done on well know wesbite such as Facebook, Twitter or Google. For example, we can see that going on CNN cause some TLS hits on Twitter and Facebook.
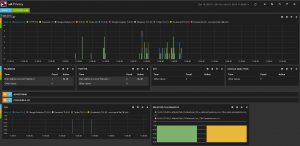
TLS being encrypted we can't prove this link and that's the short time frame that stand for a proof of the link between websites.
Conclusion
SELKS privacy dashboard is just an example of what you can achieve in SELKS by using Suricata network security monitoring capabilities. The demonstration shown here is local but don't forget you can do it at the level of a whole network.