We've had the privilege of working closely with a diverse range of organizations around the world - some of the most targeted, in fact. These include central banks, insurance companies, government institutions, critical infrastructure, energy producers, compute hosting providers, government CERTs, and more.
During those deployments we have witnessed remarkable successes, many of which are captured in this eBook.
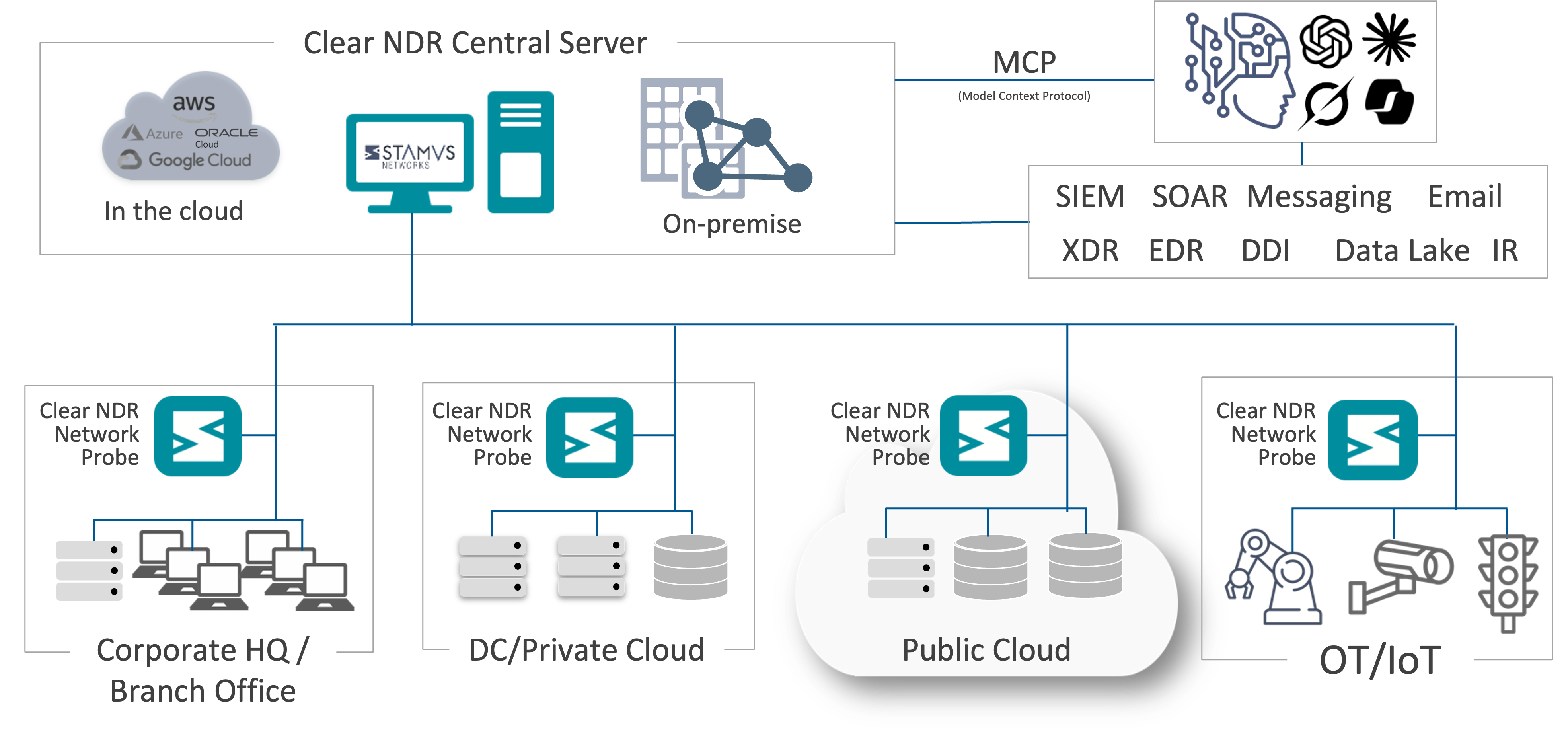
In each of these stories, Clear NDR (formerly Stamus Security Platform) played a pivotal role in safeguarding networks, mitigating attacks, and minimizing the impact of security incidents.