Network Detection and Response Use Cases
What challenges does network detection and response solve?
Network Detection and Response (NDR) play a crucial role in addressing cybersecurity challenges that could impact an organization’s ability to safeguard its networks, assets, and data. Some common challenges that are solved by network detection and response use cases are:
- Evolving Threats: Cybercriminals constantly develop new tactics, techniques, and procedures (TTPs), making it difficult to stay ahead with signature-based security solutions. NDR uses machine learning and behavioral analysis to detect anomalies and suspicious activities, even unknown threats.
- Expanding Attack Surface: With cloud adoption, remote work, and the proliferation of devices, attack surfaces are wider than ever. NDR provides comprehensive network traffic monitoring, encompassing traditional IT, cloud environments, and IoT devices.
- Hidden Threats: Attackers often move laterally within a network, hiding malicious activity amongst legitimate traffic. NDR's deep inspection and behavioral analysis help uncover these hidden threats before they escalate.
- Alert Fatigue: Traditional security solutions generate overwhelming numbers of alerts, leading to "alert fatigue" and hindering analysts' ability to focus on critical threats. NDR prioritizes alerts based on risk and context, reducing noise and streamlining investigation.
- Timely Response: Rapid incident response is crucial to minimize damage. NDR automates investigation workflows, enables faster threat identification, and facilitates quicker containment and remediation actions.
- Resource Constraints: Security teams often lack the manpower and expertise to effectively manage security tools and respond to incidents. NDR simplifies operations, automates tasks, and provides actionable insights, even with limited resources.
What are the challenges of network detection and response?
Network detection and response (NDR) faces some challenges and limitations that are common among network security systems, such as encryption, false positives, limited endpoint visibility, and scalability. Despite these limitations, the overall value provided by NDR outweighs the potential impact of these challenges. Let’s take a closer look at the challenges commonly faced by network detection and response (NDR):
- Encryption:
NDR encounters difficulties in detecting threats within encrypted network traffic, particularly with the widespread use of Transport Layer Security (TLS). As encryption becomes more prevalent, it becomes harder for NDR solutions to analyze the contents of encrypted communication. To address this, organizations can implement measures like SSL/TLS decryption proxies or specialized decryption software to allow their security teams to inspect encrypted traffic.
- False Positives and Negatives:
Like any threat detection system, NDR solutions may generate false positives and false negatives. False positives lead to benign activities being mistakenly flagged as threats, resulting in unnecessary alerts and resource diversion. False negatives occur when actual threats go undetected, posing a risk to the organization. Fine-tuning NDR systems to minimize false positives while maintaining high detection accuracy can be challenging, but modern systems, such as the Stamus Security Platform, offer solutions to this problem.
- Limited Endpoint Visibility:
NDR primarily focuses on monitoring and analyzing network traffic, offering insights into network-based threats and behaviors. However, it provides limited visibility into endpoints — individual devices — and user activities on those devices. To enhance threat detection originating from endpoints, integration with Endpoint Detection and Response (EDR) solutions may be necessary for more comprehensive coverage.
- Scalability and Performance:
NDR may face scalability and performance challenges in large and complex network environments. Real-time processing and analysis of vast amounts of network data can demand significant computational resources. Organizations must select NDR systems capable of handling high network traffic volumes to meet their specific performance requirements.
- False Sense of Security:
Implementing any threat detection and response system, including NDR, should not lead to reliance on a single system. Organizations, whether favoring NDR, EDR, or XDR, should integrate multiple systems to maximize coverage and avoid a false sense of security. Neglecting other crucial security measures is not advisable.
Why is network detection and response important?
Network detection and response is important because it enhances network visibility, which is the key to unlocking a deeper understanding of your organization’s network infrastructure. Network detection and response vendors have identified three primary benefits to increased network visibility:
- Early Threat Detection:
By maximizing network visibility, organizations can identify malicious activities and indicators of compromise (IOCs) at their earliest stages. Network traffic holds essential information to spot abnormal behaviors, suspicious communication patterns, and unauthorized activity. This early detection empowers security teams to respond promptly and mitigate threats before they cause significant damage or compromise sensitive data.
- Rapid Incident Response:
Increased network visibility enables real-time monitoring and analysis of network traffic, allowing organizations to respond swiftly to security incidents. Clear visibility into network activities helps security teams identify the incident's scope, trace its origin, and take immediate action to contain and remediate the threat. Timely incident response minimizes potential damage, reduces downtime, and aids in quickly restoring normal operations.
- Comprehensive Threat Analysis:
Expanded network visibility facilitates in-depth analysis of network traffic, aiding organizations in understanding the context, nature, and scope of potential threat proliferation. By scrutinizing network communication patterns, traffic flows, and data exchanges, security teams can identify malicious behavior, detect malware infections, unveil hidden threats, and gain valuable insights into attackers' tactics, techniques, and procedures (TTPs). This comprehensive threat analysis empowers security teams to develop effective countermeasures and enhance overall defenses.
What are the capabilities of NDR?
Network detection and response products are made up of a number of different tools and features that make it capable of identifying, analyzing, and mitigating various cyber threats, such as deep packet inspection, behavioral analysis engines, threat intelligence integration, and more. The following features are common in many modern NDR solutions:
- Deep Packet Inspection:
Certain NDR systems engage in the real-time capture and analysis of network traffic. This involves extracting metadata, understanding communication patterns, detecting potential threats, identifying anomalies, and logging activity.
- Behavioral Analysis Engines:
Network detection and response products leverage machine learning and behavioral analysis to establish baselines for normal network behavior. These engines excel at detecting deviations that may indicate malicious activities, providing a proactive layer of defense against evolving threats.
- Threat Intelligence Integration:
Competent NDR solutions seamlessly integrate with third-party threat intelligence feeds. This integration enhances detection capabilities by continuously providing up-to-date information about known threats and indicators of compromise, ensuring a more robust and adaptive security posture.
- Network Forensics:
Network forensics tools play a crucial role in investigating security incidents by analyzing historical network data. This aids security teams in gaining insights into the scope and impact of potential breaches, facilitating a more comprehensive understanding of the cybersecurity landscape.
- Automated Incident Response:
Most NDR systems offer the capability to initiate predefined automated responses to security incidents. This feature ensures swift containment and mitigation of threats, contributing to an efficient incident response strategy.
- Vulnerability Discovery:
Certain network detection and response products claim the ability to identify and assess vulnerabilities within the network that could be exploited by attackers. This proactive approach to vulnerability discovery contributes significantly to threat mitigation efforts, fortifying the network against potential exploitation.
- Threat Hunting:
Integrated into some NDRs, a threat hunting platform utilizes data collected by the system to sift through network traffic. This enables the identification of user-selected threats, suspicious behaviors, or anomalous activities, empowering security teams to proactively hunt for and address potential security risks.
Why is NDR needed?
Network detection and response tools are needed to improve an organization’s understanding of network traffic and activities that might be missed by their other cybersecurity systems or outdated network security tools. Modern NDR systems are highly effective at detecting and responding to threats, offering significant value to established organizations aiming for increased visibility. However, the suitability of various NDR systems varies for each organization. When evaluating network detection and response tools, look for the following characteristics:
- Sophisticated Detection: Choose an NDR with advanced detection capabilities that effectively identify complex threats.
- Transparent and Explainable Results: Prioritize NDRs that provide clear and understandable results supported by evidence, promoting transparency.
- High-Fidelity Response Triggers: Look for NDRs with precise response triggers to ensure accurate and targeted actions.
- Guided Threat Hunting: Opt for NDRs that support guided threat hunting, empowering security teams to proactively explore potential risks.
- Openness and Extensibility: Select NDRs that offer openness and extensibility, allowing seamless integration with existing infrastructure and future adaptability.
- Complete Data Sovereignty: Ensure that the chosen NDR guarantees complete data sovereignty, protecting your organization's data in compliance with regulations.
We believe that these six traits indicate a mature and effective network detection and response solution.
What is the future of network detection and response?
The 2022 Gartner NDR Market Guide claims that the network detection and response market will evolve in one of three ways:
- Hybrid-network NDR:
Gartner predicts that some NDR products will expand beyond network traffic analysis due to the increase in hybrid environments. In this scenario, the NDR will add new detection mechanisms geared specifically toward cloud environments, such as “security posture anomalies for cloud infrastructure”.
- XDR:
Gartner believes it is possible for many existing NDR products to evolve into extended detection and response (XDR) systems, due to the rising popularity of XDR platforms.
- Commoditized as part of another security platform:
NDR could become a feature of a larger, consolidated security platform. This type of consolidation of tools is popular in organizations with smaller security teams or with budget restrictions that can’t justify dedicated, single-vendor solutions.
What is detection and response in cyber security?
The concept of "detection and response" in cyber security spans a spectrum of solutions, including those targeted at network security, endpoints, or a hybrid approach that combines both. This strategy centered around detection and response products acknowledges the inherent challenge of completely preventing all potential cyber threats, leading to an emphasis on timely detection and a rapid, effective response to mitigate potential damage. Organizations must recognize that, realistically, preventing every cyber threat is impossible. A proactive stance focused on identifying and neutralizing malicious activities is needed instead.
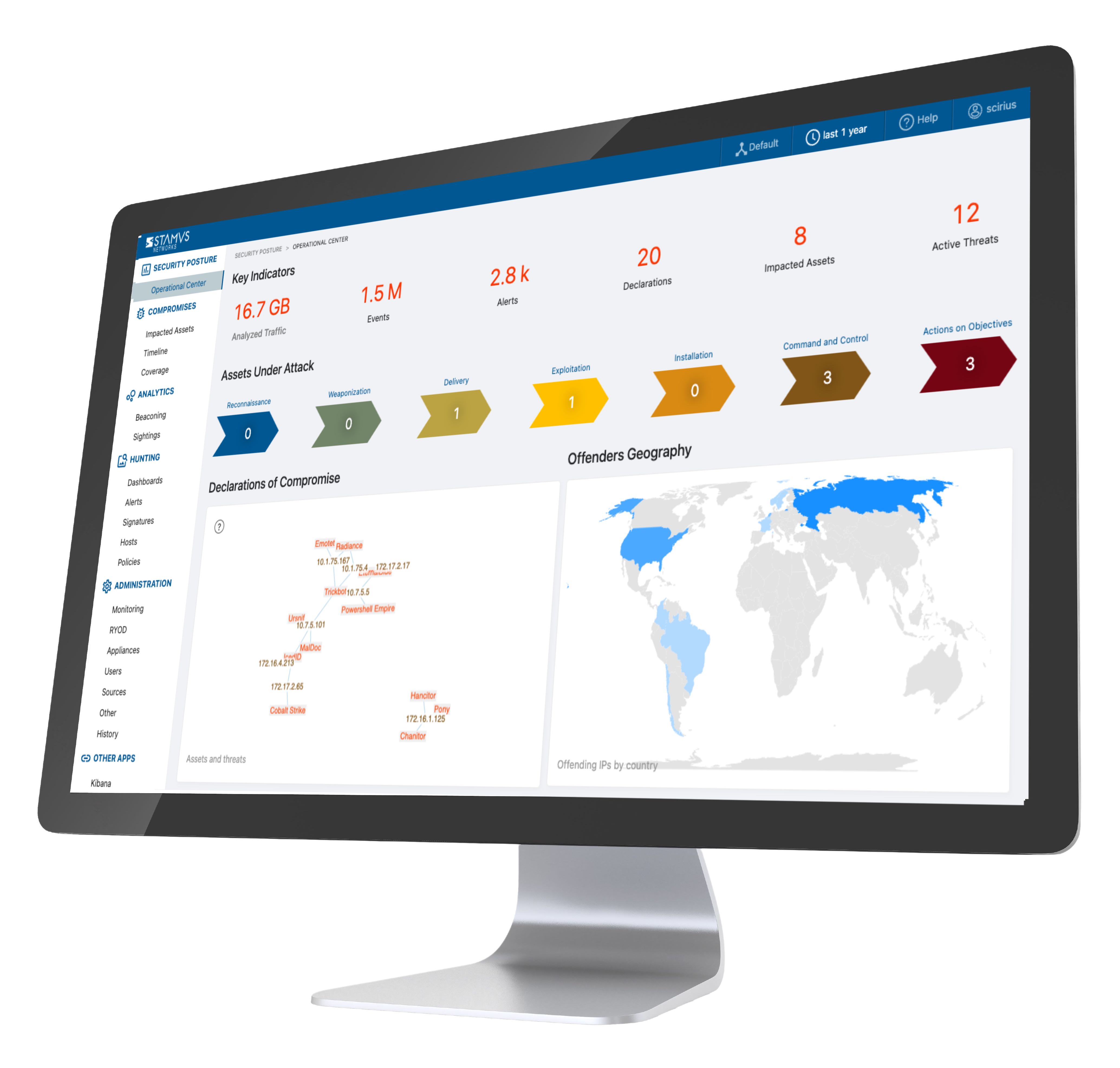
Network detection and response (NDR) seeks to achieve this goal by monitoring the communication and traffic happening on an organization’s network. A network detection and response product example would be the Stamus Security Platform (SSP), which is the world’s most advanced Suricata-based network detection and response (NDR) system. SSP combines the very best of machine learning, signature-based, IoC matching, and algorithmic threat detection into a single platform that identifies both known and unknown threats lurking on the network. It then provides high-fidelity response triggers to help analysts stop threats quickly.
Why do I need network detection and response?
You need network detection and response because it provides unique features and capabilities not found in other cybersecurity tools. The best network detection and response products achieve the following functions:
- NDR Fills Gaps Left by EDR and Similar Tools:
EDR systems require installing an agent on every device, creating coverage gaps in certain environments like those with IoT devices, many medical facilities, or Bring-Your-Own-Device policies. NDR — operating without agents — provides real-time monitoring for optimal visibility in any environment.
- NDR Secures Cloud and Hybrid Environments:
As cloud and hybrid setups become more common, the need for security systems that can monitor these environments is increasing. NDR utilizes network telemetry data — a valuable source for monitoring, analysis, threat detection, and investigation — to monitor cloud assets that use the network for communication.
- NDR Benefits Both Security and IT Teams:
Beyond its security advantages, NDR is beneficial for IT teams. It offers heightened visibility into the network, assisting in diagnosing network issues and optimizing overall network performance.
- NDR Empowers Zero-Trust Security:
The widely adopted zero-trust security model requires continuous verification of users, devices, and applications on the network. Achieving this verification is challenging without comprehensive visibility into the network, a task easily accomplished with NDR.
NDR: More Than Just Threat Detection
Realistically, organizations cannot get by using only one cybersecurity solution. There are a number of other controls, strategies, and frameworks that must be in place to ensure a strong cybersecurity posture. Mature organizations should consider the use-cases and merits of each type of solution and then determine which combination will satisfy their unique needs.
Network detection and response should most definitely be part of that consideration, as it provides robust threat detection and maximum network visibility among other benefits.
If you want to discuss the Stamus Security Platform with one of our NDR experts, book a demo at the link below.