Like with any platform, network detection and response (NDR) is a combination of a number of tools and functions. These tools combine to create a comprehensive security solution that enables organizations to identify, analyze, and respond to emerging threats. Understanding these tools, including what they are for, the challenges they solve, and whether they are a fit for your organization, is imperative when learning more about NDR.
Network Detection and Response (NDR) is an advanced cybersecurity approach focused on monitoring and analyzing an organization's network traffic to promptly identify and address potential threats. Unlike traditional network security measures, an NDR solution operates in near real-time, employing sophisticated detection mechanisms like artificial intelligence and machine learning. The primary objective of NDR is to bolster the organization's capability to both detect and respond to threats, thereby mitigating the risk of data breaches or unauthorized access.
NDR solutions continuously gather and scrutinize network traffic data, utilizing a combination of predefined rules, signatures, and advanced algorithms to detect known threats, abnormal patterns, or indications of malware infection. The anomalies that NDR systems can pinpoint include unusual data transfers, suspicious user behaviors, potential malware beaconing activity, and data exfiltration, among others.
Many NDR solutions incorporate tools for behavioral analysis, enabling them to establish a baseline of normal network behaviors. This capability allows the system to recognize deviations that may signify potential security threats.
What distinguishes NDR from conventional security tools is its multifaceted capabilities. While NDR systems do include detection methods based on predefined rules or signatures, similar to those in an intrusion detection system, they also integrate modern detection methods. These modern techniques enable the system to dynamically adapt and respond to emerging threats.
NDR plays a critical role in the overall cybersecurity strategy of an organization by offering deep visibility and insights into network activities. This, in turn, empowers security professionals to respond swiftly to potential incidents.
NDR systems incorporate a diverse set of network detection and response tools that determine the approach used for identifying potential threats. These tools are integral to the examination of network traffic and significantly influence the outcomes of this analysis. While not all NDR systems include the same set of tools or capabilities, many commonly feature the following:
Network detection and response solutions address key challenges in cybersecurity, enhancing an organization's ability to protect its networks, assets, and data. These challenges encompass various use cases that organizations should consider when assessing their security needs.
NDR is needed because of its unique functionality and utility in relation to other available cybersecurity products. Network detection and response vendors develop these systems to support organizations that can’t maintain full coverage using other types of systems. Here are four reasons why NDR is needed:
The primary use cases for NDR software are:
Automated Threat Detection:
Utilizing advanced algorithms and machine learning, NDR software automatically pinpoints potential threats within network traffic. By continuously monitoring and analyzing network data, NDR swiftly identifies anomalous behaviors, malicious patterns, and Indicators of Compromise (IOCs) in near real-time. This functionality is pivotal for executing incident response strategies.
Incident Response:
NDR software captures detailed logs of network activity and traffic data, empowering security teams to reconstruct the sequence of events, investigate the root cause, and comprehend the extent of a breach. This heightened visibility accelerates response times, allowing organizations to efficiently contain and mitigate the impact of security incidents.
Proactive Threat Hunting:
Security analysts leverage the advanced search capabilities, behavioral analytics, and threat intelligence provided by NDR for proactive threat hunting. By actively exploring network data, analysts can identify hidden threats and uncover emerging attack patterns. This proactive approach keeps organizations ahead of threat actors, enabling the detection and neutralization of threats before they cause harm.
Remediation:
Once a threat is identified, NDR software can automatically initiate response actions through integrations with other systems, such as EDR. These actions may involve blocking suspicious IP addresses, isolating compromised end-user devices, or implementing access control policies. Such automated responses effectively contain the threat, prevent lateral movement, and minimize the impact of a security incident.
Network detection and response (NDR) is an evolution from network traffic analysis (NTA). Initially, NTA was just a method of network monitoring using flow data (from devices like routers) or packet data (from SPAN, network TAPs, or mirror ports). As time advanced, the best NDR solutions emerged, building upon the foundational principles of NTA and effectively rendering the two terms synonymous.
NDR tools, in their expansion beyond NTA systems, bring enhanced capabilities for exploring historical metadata, engaging in threat hunting, and executing automated threat responses. Notably, many of today's prominent NDR solutions originated as simpler NTA solutions but have evolved to encompass a broader range of functionalities. As a result, the terms NTA and NDR are now commonly used interchangeably in the cybersecurity industry. When seeking the best NDR solutions, understanding this evolution and the convergence of these terms is essential for making informed choices in network security.
Endpoint detection and response (EDR) tools focus on monitoring and responding to threats at the individual device level, encompassing computers, servers, mobile devices, etc. To achieve this, EDR tools employ an endpoint agent — a discreet application embedded in the device’s operating system. This agent continuously monitors for suspicious activities, malware, or malicious processes that have infiltrated the endpoint.
The goal of EDR, like NDR, is to swiftly identify and respond to threats. Upon detection, an EDR solution can initiate response actions such as quarantining the endpoint. When integrated with an NDR, the threat might be discovered through the network but the response might be through action at the endpoint level.
EDR tools are a common counterpart to NDR, and many organizations choose to use both for maximum visibility into user activities. Combining both of these tools is essential to creating a comprehensive cybersecurity strategy, as they complement each other to provide a holistic view of the organization's infrastructure.
Your organization might need NDR to enhance visibility into network traffic and activities that are being overlooked by your existing security solutions or outdated network monitoring tools. The best NDR tools stand out as highly effective solutions for threat detection and response, offering substantial value, particularly for well-established organizations seeking heightened visibility. However, the suitability of NDR varies for each organization. To assess which network detection and response solution aligns best with your needs, consider examining the following characteristics:
We believe that these six traits are the signs of a mature and effective network detection and response solution. When evaluating whether a particular NDR is a good fit for your organization, you should check for these qualities.
Network detection and response tools vary between each NDR solution. The tools listed above, including the use-cases and benefits, are not present in every NDR. It is up to each organization to carefully evaluate their unique needs before making any purchasing decision.
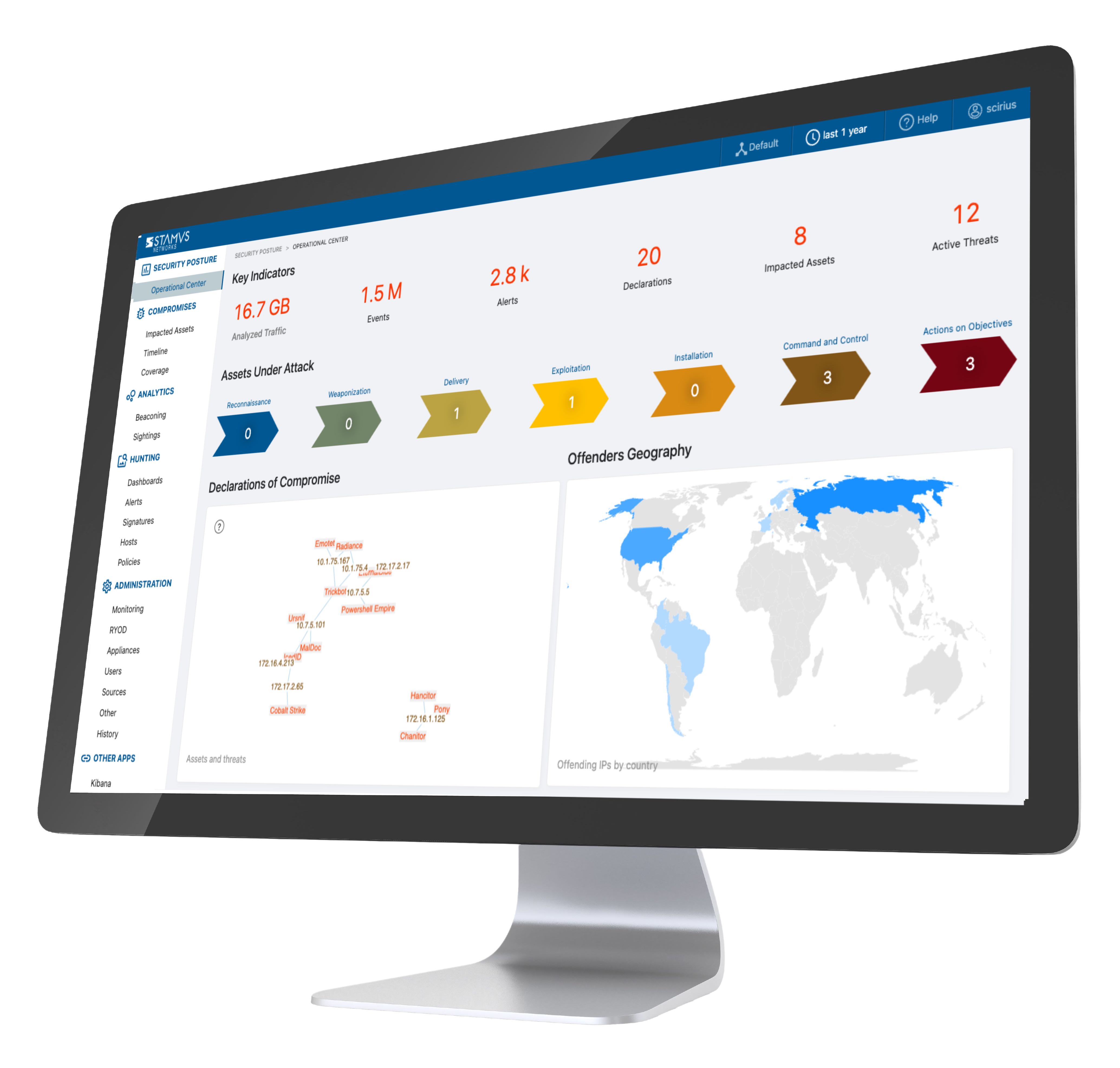
If you are in the market for an NDR solution, consider the Stamus Security Platform (SSP).
SSP is the world’s most advanced Suricata-based network detection and response (NDR) system. We combine the very best of machine learning, signature-based, IoC matching, and algorithmic threat detection into a single platform that identifies both known and unknown threats lurking on your network.
If you want to see the Stamus Security Platform in action, schedule a demo with one of our NDR experts at the link below.
ABOUT STAMUS® NETWORKS
Stamus Networks is the global leader in Suricata-based network security and the creator of the innovative Clear NDR® system. Designed to close visibility gaps and reduce alert fatigue, Clear NDR transforms raw network traffic into actionable security insights with unmatched transparency, customization, and effectiveness. Trusted by leading financial institutions, government agencies, and battle-tested over 9 years in NATO’s largest cybersecurity exercises, Stamus Networks delivers proven, high-performance network detection and response solutions. Stamus empowers security teams – delivering clarity amidst complexity – with greater control, fewer false positives, faster response times, and a more responsive, open approach than legacy vendors.
© 2014-2026 Stamus Networks, Inc. All rights Reserved.