NDR providers (also known as NDR vendors) are companies or organizations that offer network detection and response (NDR) solutions. These NDR vendors typically develop and offer software or hardware solutions that help organizations detect and respond to security incidents within their networks.
NDR solutions may include features such as real-time monitoring, behavior analytics, threat intelligence integration, automated response capabilities, and AI or machine learning threat detection methods.
.
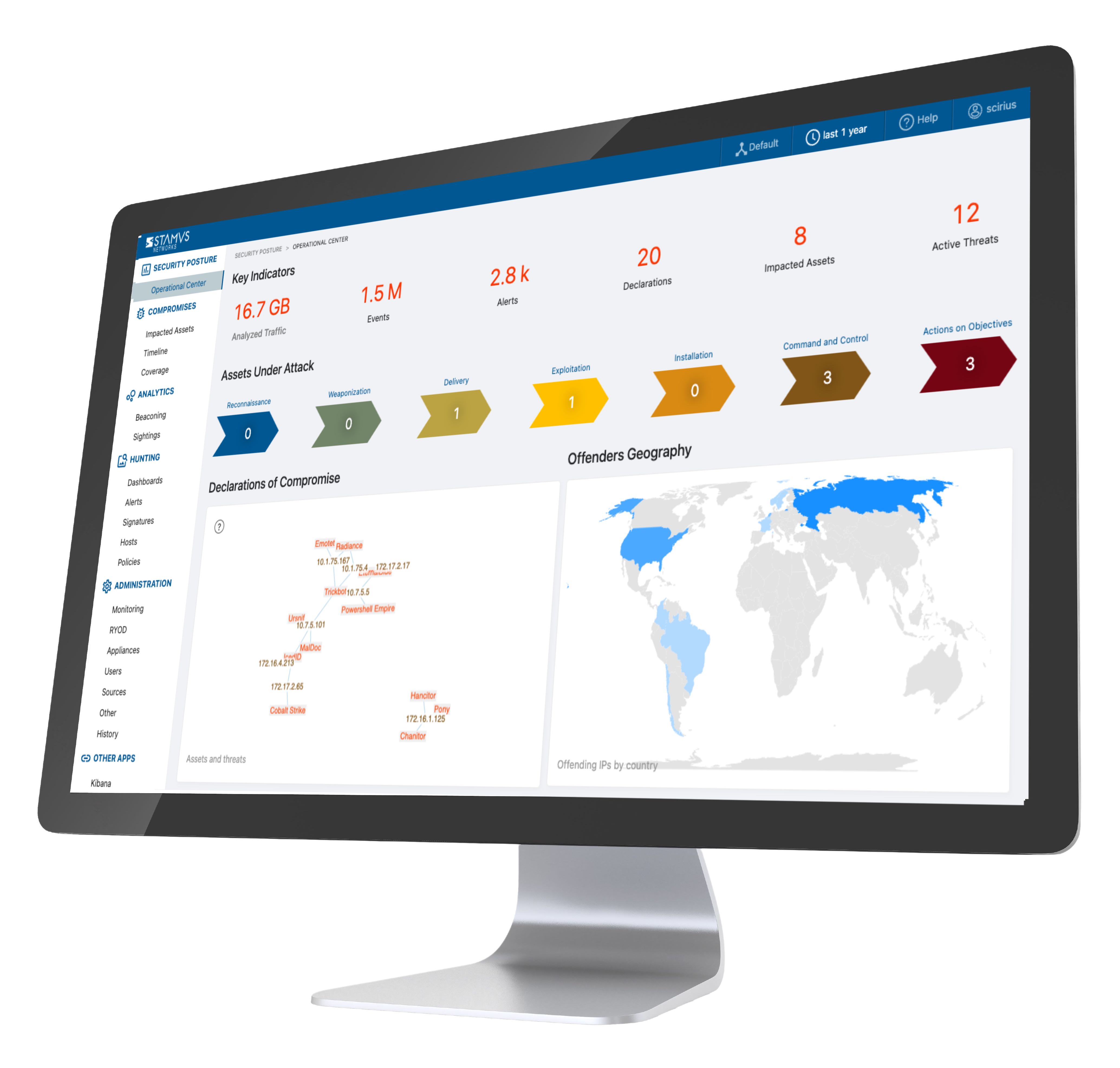
While each NDR vendor offers a different product with different capabilities, limitations, and requirements, a mature NDR solution will have the following characteristics:
When looking for an NDR vendor to support your organization’s needs, it is important to consider the differences between each solution to determine which will be the best fit.
Network detection and response (NDR) is a cybersecurity solution that monitors and analyzes network traffic for signs of malicious activity or security threats. This is done using a combination of advanced detection methods paired with automated incident response and threat hunting tools. NDR enhances an organization’s ability to proactively detect and respond to potential threats, reducing the risk of data breaches and unauthorized access.
Because network detection and response (NDR) functions by analyzing network traffic data, it continuously collects that data to provide near real-time detections. This is different from other popular threat detection and response systems, such as EDR, which perform data collection and analysis on individual devices.
NDR is a natural evolution from traditional network security tools like intrusion detection systems (IDS). Unlike IDS however, NDR enables a proactive response by providing the advanced detection methods, anomaly detection, threat hunting, high-fidelity alerts, and automated response needed to combat emerging threats. Many NDR systems will include IDS signature-based threat detection methods, but no IDS is capable of performing NDR-level functionality.
The role of NDR is to provide visibility and enable threat detection, analysis, and response at a network level. Network detection and response vendors build solutions that can process and categorize vast amounts of network traffic data in real time.
This visibility enables the organizations that use NDR solutions to have the full picture of what is happening in their network, regardless of whether or not they have access to the individual devices on their network. Network visibility is especially useful in environments where an organization’s network is accessed by outside devices and users or where there is a bring-your-own-device (BYOD) policy.
Increased network visibility leads to three key benefits:
The 2022 Gartner NDR Market Guide offers the following definition for NDR:
“Network detection and response (NDR) products detect abnormal system behaviors by applying behavioral analytics to network traffic data. They continuously analyze raw network packets or traffic metadata between internal networks (east-west) and public networks (north-south). NDR can be delivered as a combination of hardware and software appliances for sensors, and a management and orchestration console in the form of an on-premises software or SaaS.”
To put it simply, Gartner’s definition of NDR is a system that detects unusual activity by analyzing network traffic. This analysis is performed on both internal and public networks. In Gartner’s words, the mechanism used to monitor network traffic can be either physical or virtual, while the user interface is offered as a downloadable software or accessed through a web-portal.
This definition provides a broad understanding of what Gartner classifies as network detection and response. Many products that claim to be NDR will fit within this definition, however each product will perform their data collection, analysis, threat detection, and incident response in different ways.
NDR security tools can detect a variety of both known and unknown threats, including but not limited to:
This detection is done through a variety of methods. For example, known malware is often identified through the use of signature-based detection. Network packets are compared against a series of signatures developed by third-party threat intelligence, and when a packet matches on a signature, an alert is issued. Some NDR security tools will then determine whether or not that alert signals a serious and imminent threat, and if so forward the needed information to the organization's security team.
Other attack signals, like those found in malware beacons, homoglyphs, and lateral movement are much more subtle and cannot be detected with traditional detection methods like signature-based detection. In these instances, many NDR security tools will have AI or machine learning detection methods capable of identifying those behaviors.
Many NDR solutions also include an interface for proactive threat hunting, where the user can filter through historical network traffic data for specific types of activity. Threat hunting is a common way to identify Shadow IT or other unauthorized user activities.
NDR monitors network traffic to detect and respond to threats and EDR monitors endpoint traffic to detect and respond to threats.
Network detection and response is done passively, meaning that monitoring is performed without installing software. Endpoint detection and response is done through active monitoring of individual endpoint devices (laptops, servers, phones, tablets, etc). This monitoring is only possible after an endpoint agent software is installed.
Both tools fall under the category of “threat detection and response (TDR)”, however they achieve their goals in different ways. When evaluating NDR vendors, it is easy to misunderstand the distinction between the two systems. Both NDR and EDR have benefits and limitations, and due to the popularity of both, many organizations try to compare the two to see which is a better fit for their security strategy. Ultimately they are complementary solutions, and an organization should not compare NDR vs. EDR, but rather seek to achieve NDR + EDR.
There is no difference between a NAV (network analysis and visibility) solution and an NDR solution. They are simply two ways to classify network security products. Forrester defines NAV as:
“Security solutions that deploy passively in networks to analyze network traffic to detect threats using behavioral and signature-based approaches; discover and establish relationships between assets; analyze traffic flow; extract relevant metadata; enable full or targeted packet capture; integrate with other control points to remediate detected threats; and enable network forensics.”
This is similar to the Gartner definition of NDR which describes NDR as a system that detects unusual activity by analyzing network traffic. The Forrester definition is more technical in nature, describing certain traits a NAV system must possess, however all the traits found in Forrester’s NAV definition are present in systems classified as NDR by Gartner.
Network detection and response is undeniably the more commonly used classification, although some NDR/NAV vendors use the two terms interchangeably.
Organizations need NDR security solutions because they provide functionality and utility that is not found in other cybersecurity products. Here are four reasons why you need NDR:
There are a lot of NDR vendors to choose from, and that choice can make a large impact on your organization’s cybersecurity posture. Stamus Networks is a global provider of high-performance network-based threat detection and response (NDR) systems. Our solution, the Stamus Security Platform, helps enterprise security teams know more, respond sooner, and mitigate threats.
If you are in the market for NDR, schedule a call below with one of our experts to see if SSP is a fit for your organization.
If you're considering adding network detection and response to your cybersecurity strategy, we recommend looking at the following resources to determine whether Stamus Security Platform is right for you:
ABOUT STAMUS® NETWORKS
Stamus Networks is the global leader in Suricata-based network security and the creator of the innovative Clear NDR® system. Designed to close visibility gaps and reduce alert fatigue, Clear NDR transforms raw network traffic into actionable security insights with unmatched transparency, customization, and effectiveness. Trusted by leading financial institutions, government agencies, and battle-tested over 9 years in NATO’s largest cybersecurity exercises, Stamus Networks delivers proven, high-performance network detection and response solutions. Stamus empowers security teams – delivering clarity amidst complexity – with greater control, fewer false positives, faster response times, and a more responsive, open approach than legacy vendors.
© 2014-2026 Stamus Networks, Inc. All rights Reserved.