Intrusion detection systems (IDS) are a critical component of many organizations’ cyber security strategies around the world, continuously monitoring network traffic and system activity for indications of potential attacks. For those unfamiliar with IDS, it can be difficult to begin learning about the nuances between different IDS approaches.
This guide explores the functionalities of the two main types of IDS, the three different detection methods all IDS adheres to, the components that make up most IDS tools regardless of type, and other common IDS questions.
Intrusion detection/prevention system software is a security mechanism employed to safeguard computer networks and systems from unauthorized access and malicious activity. Both IDS and IPS are commonly used as a first line of defense for many organizations. Intrusion detection techniques often include monitoring traffic, comparing traffic to a set of predefined rules or signatures, and then issuing alerts when traffic matches a malicious pattern.
Intrusion detection usually concentrates on identifying and reporting potential security breaches, while intrusion prevention seeks to actively block threats. Early detection of intrusions allows security teams to take action and minimize damage. This can involve isolating infected devices, blocking attackers, or launching incident response procedures.
There are two main types of Intrusion Detection Systems (IDS) based on their deployment and data source:
1. Network Intrusion Detection System (NIDS): NIDS act as network monitoring devices deployed at strategic points within a computer network. Their primary function is to continuously capture and analyze network traffic data traversing a specific network segment. NIDS can be implemented in two primary ways:
NIDS typically utilizes network adapter promiscuous mode. This mode allows the NIDS to capture all network traffic on the attached network segment, regardless of its intended recipient. NIDS employs two main techniques for analyzing captured network traffic data: signature-based detection and anomaly-based detection.
2. Host-Based Intrusion Detection System (HIDS): In contrast to NIDS which focuses on network traffic analysis, HIDS provides security for individual devices (hosts) within the network. HIDS function as software agents deployed directly on the operating system of the host device itself. Their primary function is to monitor and analyze activity occurring on the host device. HIDS are deployed as software agents on individual servers, desktops, or laptops within the network. A single HIDS agent is typically installed on each host device for dedicated monitoring.
HIDS collects data from various sources on the host device, including:
HIDS primarily utilizes anomaly-based detection techniques. By analyzing the collected data, HIDS establishes baselines for typical host activity. Significant deviations from these baselines, such as unusual file access attempts or unexpected processes running, can indicate potential intrusions or suspicious behavior.
The three types of intrusion detection systems based on detection methods are anomaly-based, signature-based, and hybrid. These methods define how the IDS analyzes data to identify potential intrusions.
Each of these three detection methods (anomaly-based, signature-based, hybrid) offers different strengths and weaknesses. Choosing the most suitable approach depends on factors like the specific security requirements of the network, the resource availability for managing the IDS, and the acceptable level of false positives.
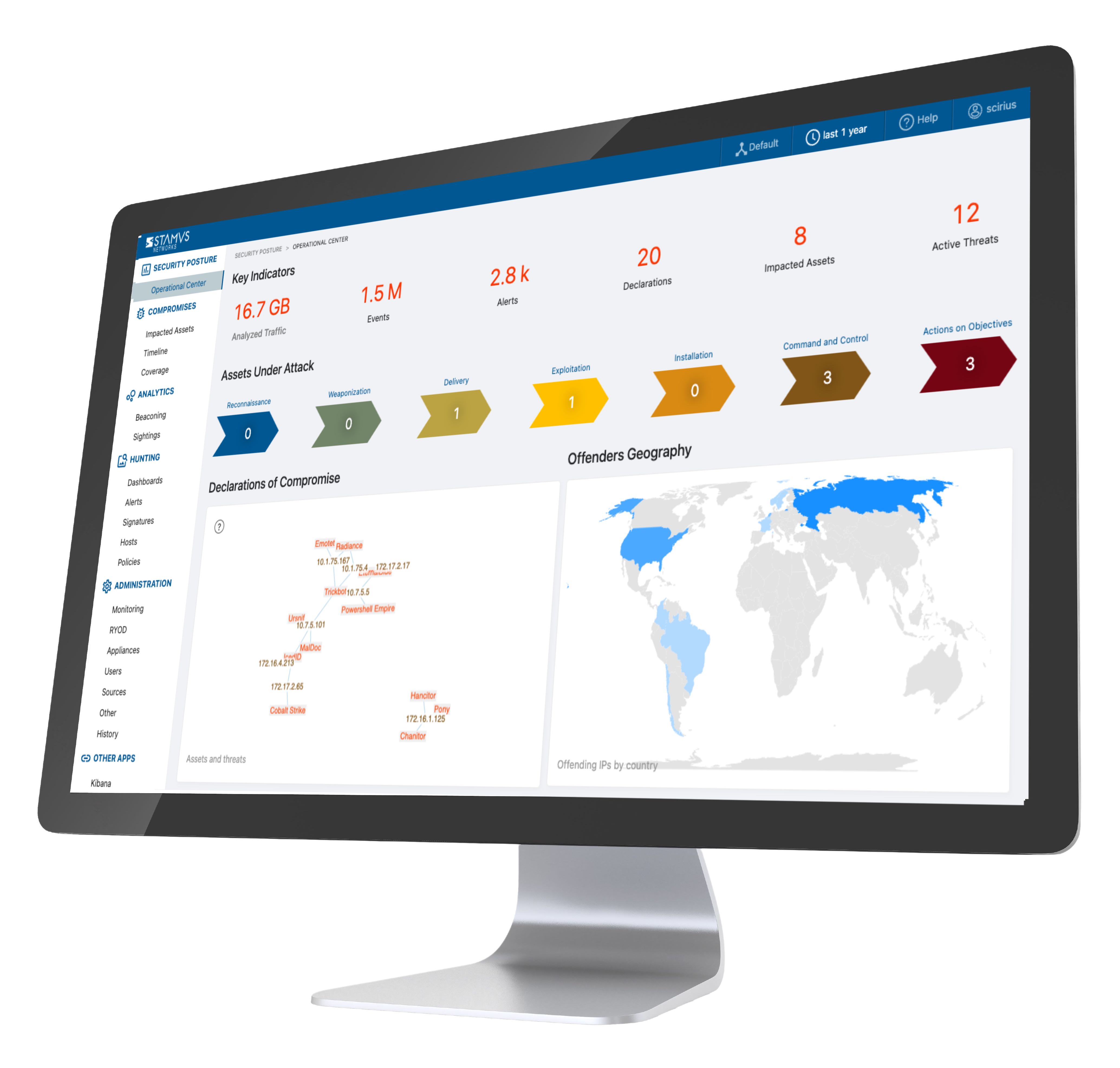
It is also important to consider switching to a more advanced modern network security solution, such as network detection and response (NDR). The Stamus Security Platform (SSP) is a modern NDR solution that leverages the best from IDS technology without the same challenges faced by IDS users.
Regardless of the IDS detection types, Intrusion detection system software can generally be broken down into 5 essential components that work together to detect suspicious activity:
1. Sensors (Data Acquisition Units): These modules function as the primary data collection mechanism for the IDS. They are deployed at strategic points within the network (network sensors) or on individual hosts (host-based sensors). Network sensors continuously capture and transmit network traffic data to the IDS for analysis. Host-based sensors monitor system activity on the device, including logs, file access attempts, and running processes.
2. Data Processing and Analysis Engine: The analysis engine is the core component responsible for evaluating data collected by the sensors. It employs various techniques to identify potential intrusions:
3. Alert Generation Engine: Upon detecting suspicious activity, the analysis engine triggers the alert generation engine. This engine is responsible for formulating alerts that include details of the suspected intrusion, such as the type of activity detected, its timestamp, and the source IP address. These alerts are then disseminated to:
4. Management Interface: This software component provides a user interface for security administrators to interact with the IDS. It allows them to:
5. Knowledge Base: The IDS maintains a repository of critical information for reference and analysis purposes. This knowledge base typically includes:
Intrusion Detection Systems (IDS) in cyber security offer several advantages in bolstering your network or system's security posture. Here are some key benefits:
It's important to note that IDS are not foolproof. They can generate false positives and may not be able to detect all types of attacks. However, the benefits they offer in terms of early threat detection, improved visibility, and enhanced security response make them a valuable tool for any organization looking to strengthen its cybersecurity defenses.
The difference between intrusion detection and prevention systems is that IPS actively blocks threats while IDS simply provides alerts. Both systems serve a purpose in an organization’s strategy and come with their own benefits and challenges.
No list of intrusion detection/prevention system examples is complete without mentioning Suricata.
Suricata is a free, open-source IDS/IPS cybersecurity tool that acts as both Intrusion Detection System (IDS) software and an Intrusion Prevention System (IPS). It is used by organizations all around the world to detect cyber threats and monitor networks for suspicious activity.
Suricata’s strength lies in its versatility. When tuned correctly, it is a high-performance tool that can handle large volumes of network traffic and generate vast amounts of network traffic data. It is also extremely flexible, offering deep analysis of various protocols and the ability to customize rule sets to fit your organization’s specific needs. Because it’s an open-source IDS/IPS, Suricata benefits from a large, active community that constantly develops and refines its capabilities.
To be used as an IPS, users simply need to configure Suricata to run in IPS mode during set-up.
A firewall is neither an IPS or an IDS, though the best intrusion detection systems can function in IPS mode to perform firewall capabilities. The main difference between a firewall and an IDS is that a firewall is simply a control mechanism, while an IDS actually detects and alerts on potentially malicious traffic. Firewalls enforce a set of predefined rules to permit or deny traffic flow based on characteristics like IP addresses, ports, protocols, or applications. It allows only authorized traffic through the network perimeter.
IDS is a monitoring and detection system. It analyzes network traffic for malicious activity or suspicious patterns that might indicate an ongoing attack. IDS doesn't directly block traffic but raises alerts for further investigation and potential response by security personnel. However, some IDS solutions, like Suricata, can be configured to function as an IPS. In this instance, the IPS actually can block traffic much like a firewall. Some organizations opt to use an IPS instead of a firewall, while others use a firewall and an IDS together.
IDS is undoubtedly a powerful and effective means to detect known threats on your organization’s network. Unfortunately, most IDS deployments are riddled with false positives, provide limited threat detection, and lack sufficient visibility into anomalous activity and subtle attack signals. Traditional IDS vendors have failed to innovate in ways that solve these challenges, leading to inefficient or downright ineffective threat detection.
You need a network security platform that doesn’t generate an endless stream of useless alerts across part of your network, and instead automatically identifies alerts of interest and notifies you of only serious and imminent threats. Your organization deserves response-ready detection with visibility into your entire network regardless of the environment with easy access to all the contextual evidence you need to stop an attack before it can cause damage. Replace your legacy IDS with a modern network detection and response platform that gives you these features and more.
The Stamus Security Platform™ is a network-based threat detection and response solution that eliminates the challenges of legacy IDS while lowering your response time. Stamus Security Platform harnesses the full potential of your network, bringing state-of-the-art threat detection, automated event triage, and unparalleled visibility to the security team.
Book a demo to see if Stamus Security Platform is right for your organization.
If you're considering upgrading from IDS to a modern alternative, we recommend looking at the following resources.
ABOUT STAMUS® NETWORKS
Stamus Networks is the global leader in Suricata-based network security and the creator of the innovative Clear NDR® system. Designed to close visibility gaps and reduce alert fatigue, Clear NDR transforms raw network traffic into actionable security insights with unmatched transparency, customization, and effectiveness. Trusted by leading financial institutions, government agencies, and battle-tested over 9 years in NATO’s largest cybersecurity exercises, Stamus Networks delivers proven, high-performance network detection and response solutions. Stamus empowers security teams – delivering clarity amidst complexity – with greater control, fewer false positives, faster response times, and a more responsive, open approach than legacy vendors.
© 2014-2026 Stamus Networks, Inc. All rights Reserved.