Today, we announced the general availability of Update 39 (U39) - the latest release of the Stamus Security Platform (SSP). We’re excited to bring our users enhanced evidence collection, expanded threat detection and hunting, and a streamlined user experience.
You can read the announcement here: Stamus Networks Announces Availability of Latest Software Release
In this article, we provide additional information and details about the release and each new feature.
Enhanced evidence collection
U39 includes several important improvements to SSP’s evidence collection and logging capabilities. New conditional packet capture (PCAP), protocol transaction, and flow logging give users additional evidence without excessive storage. And SSP now logs additional DCERPC, HTTP header, and TLS cipher suite metadata with each detection event (alert), giving users access to more complete metadata evidence during incident investigation and uncovering hidden anomalies in a proactive threat hunt.
Read more about each below.
DCERPC function name enrichment
SSP now logs additional DCERPC metadata with each detection event (alert). This gives users access to more complete metadata evidence during incident investigation and uncover hidden anomalies in proactive threat hunt.
TLS cipher suite info enrichment
SSP now logs TLS cipher-related metadata with each detection event (alert). This gives users access to more complete metadata evidence during incident investigation and uncover hidden anomalies in proactive threat hunt.
Complete HTTP header content enrichment
SSP now logs all HTTP header content with each detection event (alert). This gives users access to more complete metadata evidence during incident investigation and uncover hidden anomalies in proactive threat hunt.
Conditional packet capture (PCAP) and export
SSP now captures packets (PCAP) associated with detection events (alerts). Users are able to export packets for any detection event from within the Hunting interface. These PCAPs include the full session that triggered the detection in question. PCAPS are de-duplicated, are stored only once on the Stamus Network Probe, and available for download as forensic evidence and for playback into SSP or third party tools such as Wireshark. This gives users access to critical forensic evidence that may be used for investigation, training, or threat intelligence sharing.
Conditional logging (in earlier releases, all records were logged)
SSP now includes the option to capture only the protocol transactions and flow records associated with a detection event (alerts and Sightings™). Previously, all NSM data was logged. This allows users to retain evidence associated with detection events for extended periods without investing in additional storage costs to retain every protocol transaction or flow record.
Optional dedicated external log server
SSP now includes the option to horizontally scale the log pipeline for higher performance and redundancy. This allows users to expand their throughput in high performance environments with the use of an external Elasticsearch cluster.
Expanded threat detection and hunting
In response to experiences gathered during our ongoing participation in NATO live-fire cyber exercises conducted by the Cooperative Cyber Defence Centre of Excellence (CCDCOE) and requests from our growing client base, we have expanded the threat detection and threat hunting capabilities of SSP.
With U39, SSP users now have access to 21 new guided threat hunting filters and additional sources of threat intelligence, including 2 lateral movement rulesets and 3 suspicious domain lists. SSP can now detect activity from a match on the media type (also known as mime-type) and can ingest additional third-party threat intelligence feeds to trigger a detection event based on a match on IP addresses and domain lists.
Read more below.
New bundled threat intelligence
With U39, Stamus Networks now makes additional sources of threat intelligence available to all SSP users.
These include two rulesets:
- Lateral movement ruleset for Microsoft Windows environments
- Lateral scan ruleset
Three domain-related threat intelligence feeds are also included:
- Newly registered domain list
- Newly registered high-entropy domains
- Newly registered top phishing domains
By subscribing to these threat intelligence feeds, SSP users will increase their visibility into potential threats and increase the body of evidence available when performing an incident investigation.
Additional guided threat hunting filters
With U39, SSP adds 21 new guided threat hunting filters. These help threat hunters to proactively identify more suspicious and unauthorized network activity, including rare network services, dynamic domains, lateral movement, and new or previously unseen executables and binaries.
In addition, we made improvements to many of the existing filters.
Match detection using IP and domain IoC threat intelligence lists
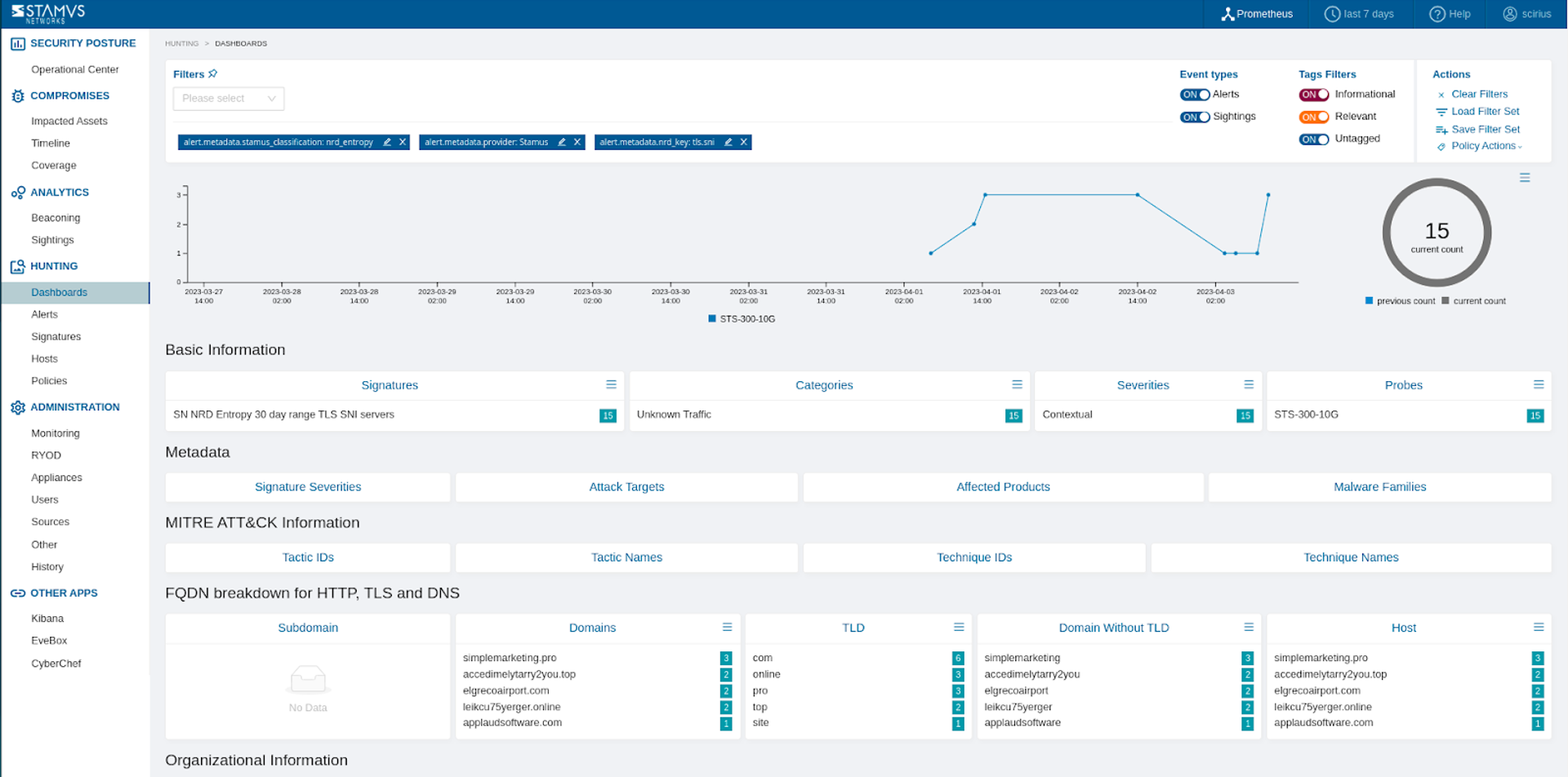
SSP can now ingest threat intelligence feeds and trigger a detection event based on a match on IPv4, IPv6, and domain. This allows users to capture network activity associated with known malicious or suspicious IP addresses and domains contained in public, private, or custom threat intelligence feeds.
First, you add the feed to the SSP source list.
When a detection event (alert) triggers, it logs the activity as shown below.
You can filter on the matches in the Hunting interface.
Detection based on a match of media type
SSP can now detect activity from a match on the media type (also known as mime-type). This allows advanced detection and file extraction based on the media type field, the two-part identifier for file formats and format contents.
Here’s how this manifests itself in the SSP user interface reviewing a detection event that triggered based on a signature matching a mime-type field.
Streamlined user experience
The user experience introduced in U38 now includes the threat hunting console (labeled “Hunting”), which is fully integrated into the user experience. The “app switcher” is no longer required to navigate between the hunting console and the rest of the user interface. Users can now pivot from notification to investigation more quickly and easily without losing important contextual data.
Read more below.
You can see the Hunting section in the screenshot below.
Expanded Host Insights™
The Host Insights™ screens now aggregate even more information collected and maintained by SSP for every host. These data include HTTP user agents, TLS agents, services, application protocols, top 10 detection events, beacons, sightings, Declarations of Compromise™, and an attack timeline -- all on a single screen for each host. This allows users to more rapidly identify all activity associated with a given host.
See a sample of this enhanced screen below.
Note: thank you to Malware Packet Analysis for the traffic sample used to create this screenshot.
Evidence export from hunt interface
With U39, SSP users may download the results of a hunt filter. The data in each block on the hunt screen may be exported individually as a text file. The complete dataset is included in the text file, even if only the top 5 are displayed in the block.
For example, after performing a hunting session and coming up with possible allow or block lists of metadata such as IP addresses or hostnames. The user may now export and save these lists for use in future detections and possible escalations to a Declaration of Compromise™.
Other enhancements
In addition, we made a number of improvements ‘under the hood’ to improve performance and integrations.
Splunk integration improvements
For Splunk users, sightings, network traffic statistics and rule performance parameters can now be forwarded to Splunk from the Stamus Network Probe. This improves visibility into network behavioral anomalies and system performance for Splunk users.
Harmful signature removal
Option to remove signatures from a source when they use potentially harmful features, such as Lua code or datasets. This prevents Stamus Network Probe from negative performance impacts caused by faulty rules.
Authentication and encryption enhancements for external Elasticsearch cluster
SSP adds improved support for authentication and encryption parameters for external Elasticsearch deployments. This provides enhanced security for users of external Elastic clusters.
Includes Elastic 7.17
SSP now includes Elastic 7.17 for the complete ELK stack, and supports up to 7.17 for external cluster installations. This change brings improvements in Kibana visualizations and Elasticsearch cluster coordination improvements, among others.
Deprecating support for Elasticsearch 5
SSP no longer supports external Elasticsearch 5.x clusters.
Summary
Stamus Security Platform is trusted by some of the world’s largest organizations, including government CERTs, central banks, insurance providers, managed security service providers, multinational government institutions, broadcasters, travel and hospitality companies, and even a market-leading cybersecurity SaaS vendor.
This release demonstrates Stamus Networks’ commitment to the continual evolution and improvement of SSP, and we hope our users move quickly to adopt these new capabilities and are better equipped to defend their organizations.



.jpg)


