In the past few blog posts, we have discussed at length the importance of creating a comprehensive threat detection and response strategy. This can be achieved by combining systems like Endpoint Detection and Response (EDR), which monitors systems at an endpoint-level, and Network Detection and Response (NDR), which leverages insights from network traffic to detect and respond to threats. This poses the question: is there a single system that can do both?
To answer this question, we must explore the newest threat detection and response system — Extended Detection and Response (XDR). In this blog post, the fourth in a five-part series on threat detection and response systems, we take a closer look at XDR and seek to determine whether or not XDR is the comprehensive solution it claims to be, or whether it should simply be included as part of a larger security strategy.
Approaches to XDR: Open XDR, TDR Extended, and Single Vendor XDR
Three distinct approaches to XDR have emerged, each with its own characteristics and implications. The first approach is known as Open XDR, where vendors seek to develop a versatile system that is accepting of various sources of telemetry and seamlessly integrates with different components like EDR, NDR, server logs, etc. Open XDR evolved from the community of SOAR and SIEM vendors, aiming to create an improved version of the traditional SIEM and SOAR combo by providing greater flexibility, interoperability, and functionality.
The second approach, which could be considered “TDR Extended”, involves vendors extending their existing threat detection and response (TDR) technology, such as EDR or NDR, to incorporate additional capabilities. This extension typically involves integrating diverse telemetry sources into a broader analytics, hunting, and response system. The goal with this approach is to leverage the foundation of the vendor's established TDR solution and enhance it with additional visibility and more advanced features. This approach allows organizations to build upon their existing investments and expand their threat detection and response capabilities.
The third approach is Single Vendor XDR, where a vendor with an extensive portfolio of security solutions repackages their individual point solutions into a comprehensive XDR system. This integrated system is positioned as seamlessly interconnected and capable of delivering exceptional collaboration among its components. While Single Vendor XDR promises benefits of integration and unified management, it also presents potential drawbacks such as vendor lock-in and the "weakest link" syndrome, where the effectiveness of the entire system relies heavily on the performance of its weakest component.
By understanding these different approaches to XDR, organizations can assess which approach aligns best with their needs, infrastructure, and security objectives, as each approach comes with its own benefits and limitations.
Extended Detection and Response (XDR) Use Cases
Regardless of the approach, XDR seeks to provide a more holistic solution to detect and respond to threats. But outside of general threat detection, XDR has 3 other primary use-cases:
- Threat Hunting: With XDR's advanced analytics and machine learning capabilities, security teams can spot patterns, anomalies, and indicators of compromise across endpoints, networks, and cloud services. By identifying threats at their early stages, organizations can respond swiftly, contain the attack, and minimize potential damage.
- Triage: Because XDR integrates the functionality of SIEM and SOAR platforms, it inherently enables its users to prioritize or triage alerts and quickly respond to the most crucial ones. Most XDR vendors assert that their platform helps security teams reduce the noise of alerts by correlating and prioritizing a high volume of alert events into a smaller number of more actionable ones.
- Investigation: XDR promotes greater visibility into different types of environments including the network, endpoints, and the cloud. This visibility, paired with telemetry from different sources and features for automated analysis, allow security teams to quickly and easily establish where a threat originated, how it spread, and what other users or devices might be affected. This is important not only for removing threats, but also for identifying vulnerabilities within the organization that need to be patched.
The Value of Cross-Environment Visibility
Due to the diverse nature of IT environments, including endpoints, networks, cloud platforms, and applications, it has become crucial to have a holistic view that transcends individual silos. This is why cross-environment visibility, as promised by many XDR systems, is incredibly valuable when creating a comprehensive security strategy.
By establishing cross-environment visibility, organizations gain the ability to identify and correlate threat indicators across different platforms, enabling the detection of sophisticated attacks that may use multiple entry points. This comprehensive view allows security teams to piece together the puzzle of an attack, understanding its scope and impact across various environments. It empowers analysts to make informed decisions and prioritize response efforts effectively.
Furthermore, cross-environment visibility enhances response orchestration and remediation. By having a unified view of the attack, security teams can coordinate response actions across different platforms, automating containment measures and triggering incident response playbooks. This coordinated approach enables faster and more effective response, reducing the time to mitigate the threat and restore normal operations.
XDR: One System to Rule Them All?
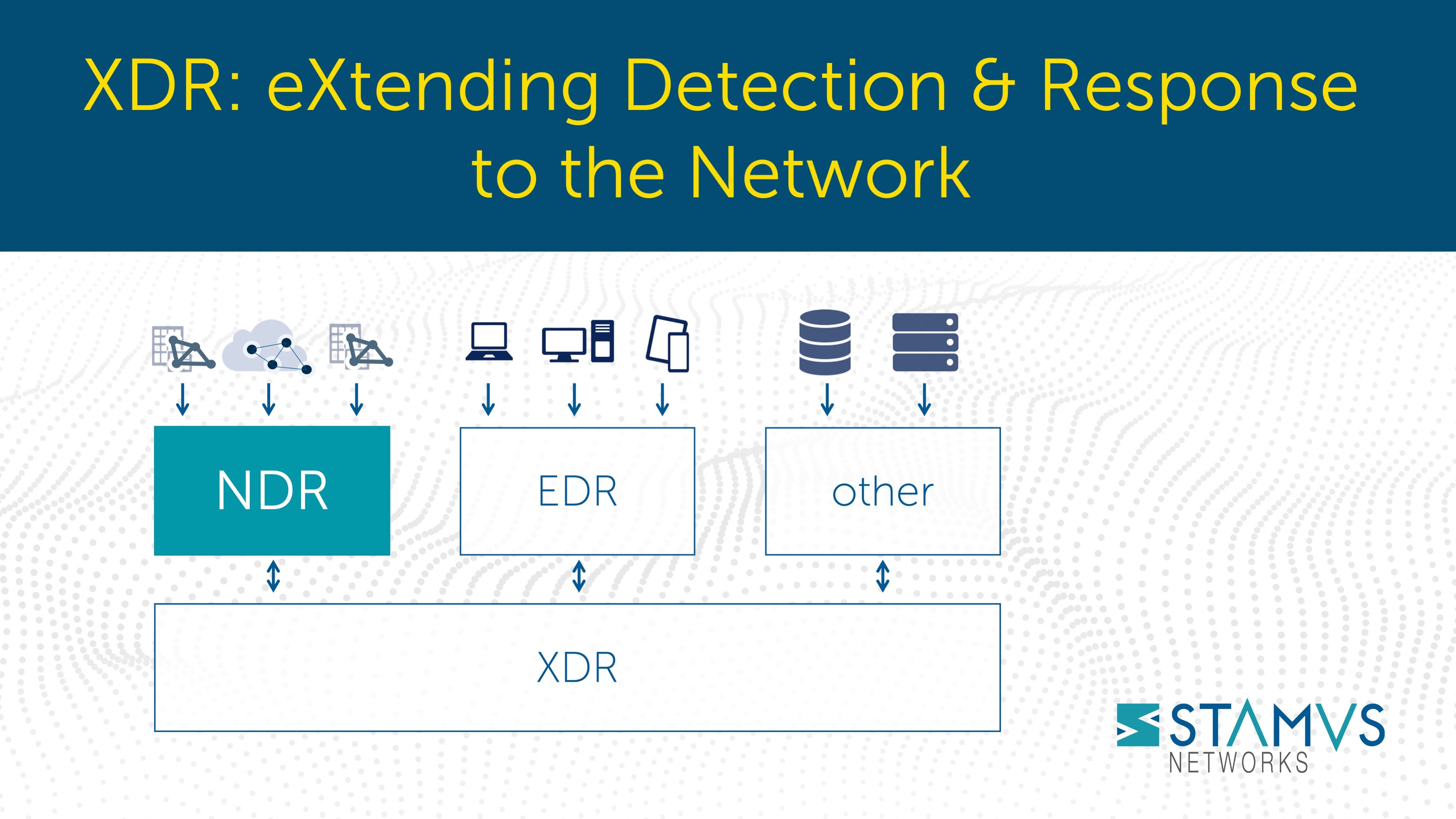
Though XDR systems, regardless of the approach, are often marketed as a “one-stop-shop” solution that provides visibility across numerous environments, it doesn't necessarily replace other existing systems like EDR and NDR. Instead, integrating XDR with these systems can leverage their strengths and create a stronger and more comprehensive security strategy.
Integrating XDR with EDR allows organizations to combine endpoint visibility and detection capabilities with cross-environment visibility provided by XDR. This integration enables a more comprehensive view of threats and facilitates more effective detection and response.
Similarly, integrating XDR with NDR enhances network visibility and threat detection. XDR can leverage the network telemetry and detection capabilities of NDR to correlate network-based threats with endpoint and other security data sources. This integration enables faster identification and response to threats that span across the network and other environments.
By integrating other systems with XDR, organizations can leverage the strengths of each system to create a more unified and coordinated security approach. This integration can enable better threat detection, faster incident response, and improved overall security posture. It can provide security teams with a more holistic view of the organization's security landscape and respond to threats more effectively.
Make sure to subscribe to the Stamus Networks blog, follow us on Twitter and LinkedIn, or join our Discord to be notified of new posts.