Writing Suricata rules has never been easier or faster since the release of the Suricata Language Server (SLS), an open-source implementation of the embedded Language Server Protocol for Suricata signatures. The Suricata Language Server adds rule (signature) syntax checking, rule-writing hints, and auto-completion to your preferred editor. By utilizing lesser-known features of the Suricata engine, SLS helps Suricata users write better, more effective, and more advanced rules.
Celebrating One Year of the Suricata Language Server
One year ago, we released the first beta of the Suricata Language Server to help Suricata users write better rules, and the response was surprising. To date, we have had over 6,700 downloads, and we have received some very positive feedback from users.
With the upcoming release of Suricata version 7.0.0, it was time to make some updates to the Suricata Language Server to ensure users can continue to enjoy an easier, more optimized rule writing experience.
Easy Suricata Rule Writing with Suricata Language Server v.0.9.0
The new Suricata Language Server is optimized for use with the newest version of Suricata, and while it still includes the same features to help with easy rule writing as before — like real-time Suricata rule syntax checking, Suricata rule auto-completion, and Suricata rule performance guidance — there are also some new features that can help users in their Suricata rule writing. In this article, we describe these new capabilities that are included in version 0.9.0, released this week.
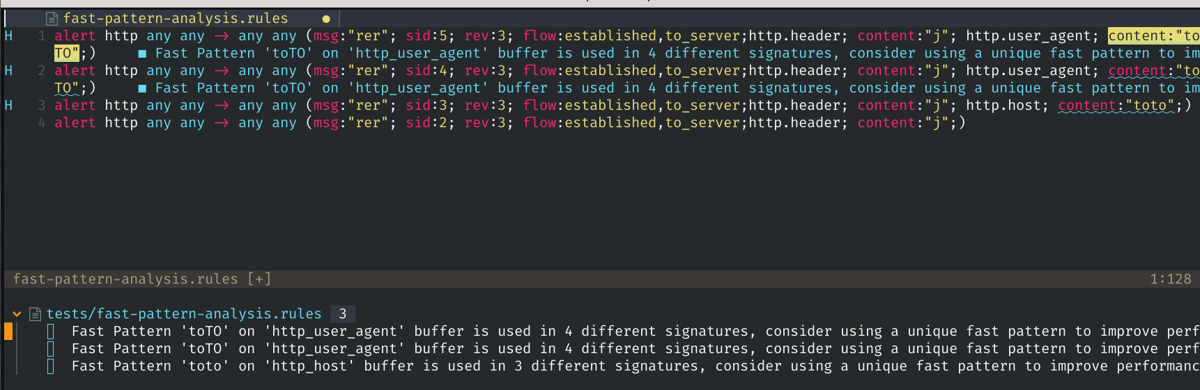
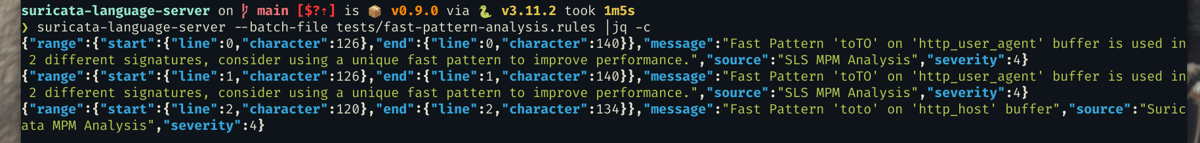
Multi pattern matching/fast pattern analysis
The performance of a signature is bound to the number of the times it is evaluated. Suricata uses a multiple pattern matching algorithm on various buffers to only evaluate a signature if there is a partial content match. This limits the full evaluation of a signature to the case where it is likely to match. With v0.9.0, SLS provides MPM analysis information to the user. It warns when a signature has no fast pattern (which means it will be evaluated a lot), and it also warns the user when a fast pattern in a signature is used multiple times (resulting in evaluation of multiple signatures). This last check is performed over all the workspace (so all files in a directory or in a git project are analyzed).
Support for Suricata 7
It is important to note that a change in error reporting for Suricata 7 will break the SLS analysis. The code has been updated to support earlier versions, and will be addressed in the upcoming Suricata release.
Support for configuration file
Suricata-language-server now accepts the use of a configuration file so it can adapt to local changes such as custom variables.
Run from the command line
SLS can now be invoked from a command line to parse a file and will return the diagnostic results on stdout. This allows SLS to be used in continuous integration workflow or embedded in custom tools that do not support LSP.
Under the hood
This version includes an important code refactoring for easier maintenance and contribution and adds unit tests to improve stability over releases.
Happy rule writing
I am hopeful that these new capabilities will make Suricata rule writing more accessible to the novice and will save time and streamline the process for expert rule writers.
Where to Get Suricata Language Server
The Suricata Language Server is available under the GPLv3 license and is hosted on Github. It is also published on Pypi, so a simple pip install suricata-language-server is enough for the installation. Configuration instructions for tested editors are described on the Github page.
Don’t hesitate to provide us feedback or ask questions if you find this project useful. You can contact us on Discord, use the issue system on Github, or simply send us an e-mail (contact@stamus-networks.com).