Network detection and response (NDR) has emerged as a competitive player within cybersecurity systems. With an increase in complex network environments and bring-your-own-device policies, it is clear why organizations have begun looking to NDR to provide another layer of protection to their digital assets.
But how does an organization evaluate what the best NDR solution is? To answer this question, our NDR experts at Stamus Networks have put together this guide to help you gain an understanding of what NDR is and what it can do for your organization.
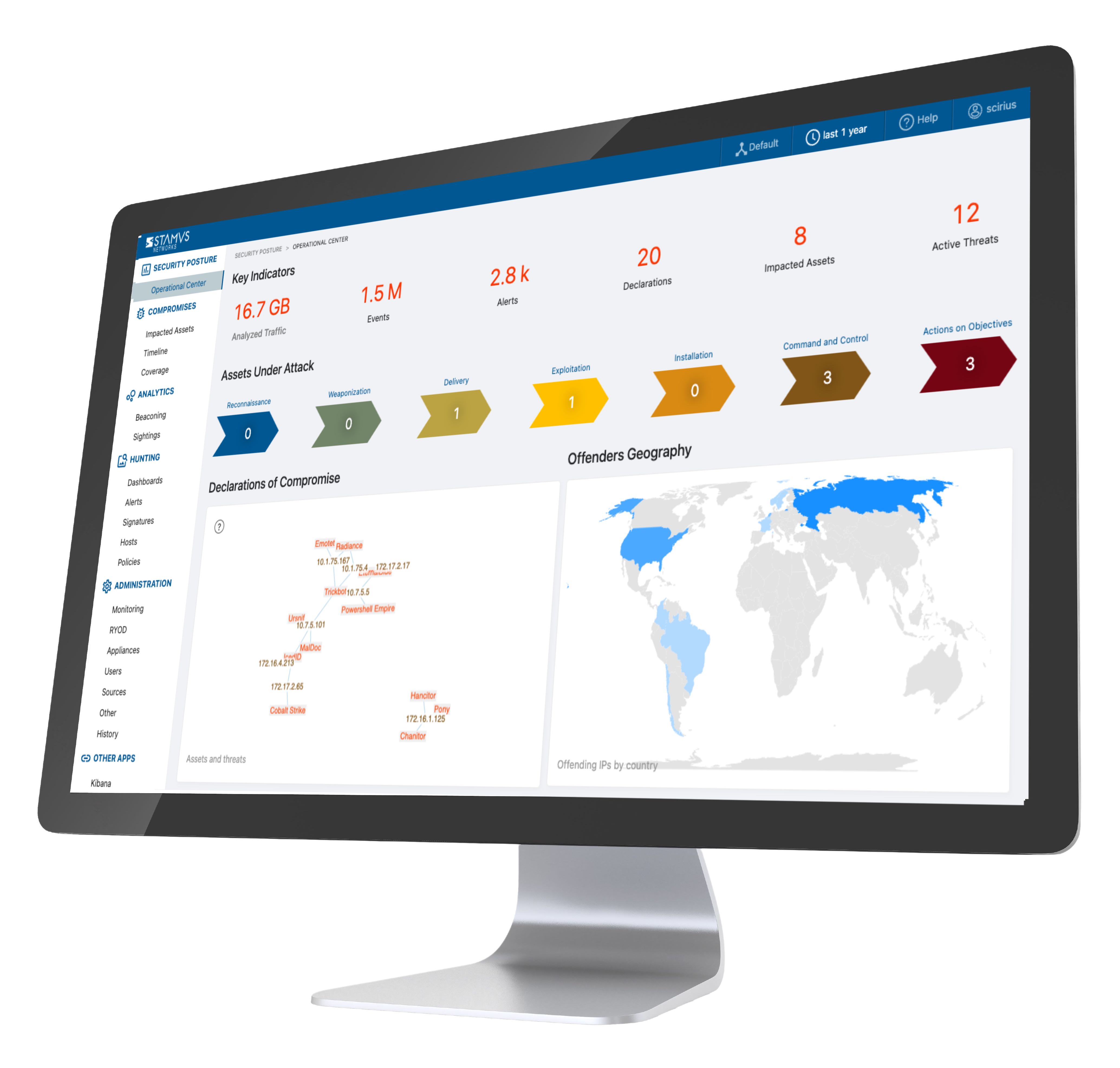
Network detection and response (NDR) is an approach to cybersecurity that uses an organization’s network traffic to identify and respond to potential threats. Using advanced detection mechanisms, such as artificial intelligence and machine learning, network detection and response systems monitor traffic in near real time and then provide actionable insights that enable security professionals to mitigate serious threats. By enhancing an organization’s ability to both detect and respond to threats, NDR reduces the risk of data breaches and unauthorized access.
Network detection and response systems continuously collect and analyze network traffic data, then use a combination of tools to identify known threats, abnormal patterns, or other signs of malware infection. Many NDR systems include tools for behavioral analysis, which allow the system to establish a baseline of “normal” network behaviors, enabling them to recognize deviations indicative of potential security threats.
Network detection and response is different from many other traditional security tools because it combines multiple capabilities. Most NDR systems do include traditional security measures, such as those found in an intrusion detection system (IDS), but they also provide organizations with more modern technologies that are equipped to identify emerging threats.
By pairing both classic and modern detection methods with other features, such as threat hunting interfaces, NDR enables an organization to practice a much more proactive and well-rounded security strategy.
As an advocate for network detection and response solutions, we would argue that the answer to that question is “yes”. NDR is an incredibly effective threat detection and response solution, and for most mature organizations there is a lot of value in the level of visibility NDR can provide. Realistically, the answer will vary for each organization. For those evaluating different network detection and response solutions to see which might be a fit for their organization, consider looking for the following characteristics:
We found that these six traits are the signs of a mature and effective network detection and response solution. When evaluating whether a particular NDR is a good fit for your organization, you should ensure that it has these qualities.
The purpose of NDR is to provide optimum network visibility. The best NDR solutions leverage the information available on the network, giving the organization a greater understanding of what is happening in their network infrastructure. There are three key benefits to this increased visibility:
NDR security tools are used to enhance an organization’s cybersecurity by actively monitoring and analyzing network traffic to detect and respond to threats. This is done by solving the following challenges:
A network detection and response tool is essentially a method or system used to perform an NDR function. The tools included in an NDR system can determine how that NDR examines network traffic and the outcome of that examination. The following network detection and response tools are common in many, but not all, NDR systems:
A network detection and response solution is a set of NDR tools packaged into a single software product. The best NDR solutions offer sophisticated detection methods, transparent results with evidence, and high-fidelity response triggers. Additionally, the best NDR solutions will be open and extensible, allowing organizations to easily integrate with other security systems like SIEM, SOAR, EDR, and XDR.
NDR solutions actively and continuously scan network traffic and then use a variety of detection methods to identify and respond to potential threats in real-time, offering a dynamic defense mechanism against cyberattacks. Then, an NDR solution will often categorize and prioritize incidents, enabling security teams to address the most critical issues promptly. Additionally, network detection and response solutions generally include the ability to automate response actions or send notifications to the organization’s security team.
NDR is only part of the cybersecurity puzzle. Whenever possible, organizations should strive for a comprehensive security strategy that leverages multiple different security tools and systems. Network detection and response is highly effective at monitoring threats at a network level, but it does not address every single security need.
An IDS/IPS (intrusion detection / prevention system) is a network security tool that monitors network traffic for known malicious, suspicious, or unwanted activity. It is impossible to discuss NDR security without also addressing IDS security. IDS functions by checking the network traffic against a set of rules or signatures. When traffic matches a signature, the IDS issues an alert.
It is important to note that there are some problems with traditional IDS measures:
Despite these challenges, IDS is still an incredibly powerful and popular network security tool. It continues to be used in many organizations, and IDS signature-based detection methods are commonly included in many network detection and response platforms.
Both NDR and IDS/IPS function by monitoring network traffic, but the difference between the two security systems lies in their approach to how threats are detected using network traffic data.
IDS/IPS is reactive, relying on a limited database of known threats and vulnerabilities to stop malicious traffic from entering or leaving the network. NDR is proactive, emphasizing the early detection and response to security incidents. IDS/IPS does not have the advanced functionality of NDR, however many NDRs include IDS signature-based detection methods.
IDS simply issues an alert anytime network traffic matches a signature for a known attack signal. This means it is not only unable to detect novel threats, but it also cannot detect more nuanced or weak attack signals like those found in unauthorized user activity, anomalous network activity, malware beacons, or homoglyphs.
Alternatively, NDR includes functionality that filters events from various sources into actionable alerts with context. It also includes more advanced detection methods built with machine learning and artificial intelligence in order to detect the more nuanced attack signals that are missed by IDS. NDR will typically also include other useful features, such as interfaces for threat hunting.
The best NDR solution is whichever solution best fits into your organization’s unique needs. We recommend first determining whether NDR is right for your organization, and then begin evaluating your options.
If you are ready to learn more about what NDR can do for your organization, book a demo with one of our experts.
We recommend first determining whether NDR is right for your organization, and then begin evaluating your options. The following resources could assist you in that decision:
ABOUT STAMUS® NETWORKS
Stamus Networks is the global leader in Suricata-based network security and the creator of the innovative Clear NDR® system. Designed to close visibility gaps and reduce alert fatigue, Clear NDR transforms raw network traffic into actionable security insights with unmatched transparency, customization, and effectiveness. Trusted by leading financial institutions, government agencies, and battle-tested over 9 years in NATO’s largest cybersecurity exercises, Stamus Networks delivers proven, high-performance network detection and response solutions. Stamus empowers security teams – delivering clarity amidst complexity – with greater control, fewer false positives, faster response times, and a more responsive, open approach than legacy vendors.
© 2014-2026 Stamus Networks, Inc. All rights Reserved.